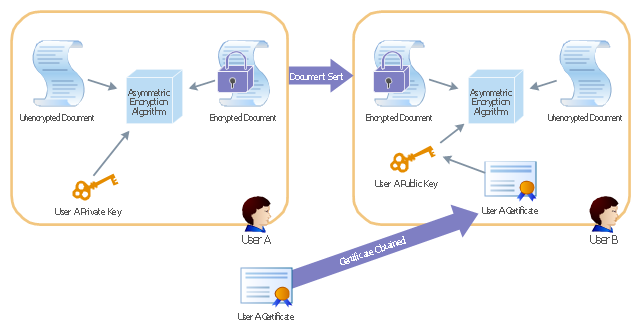
This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
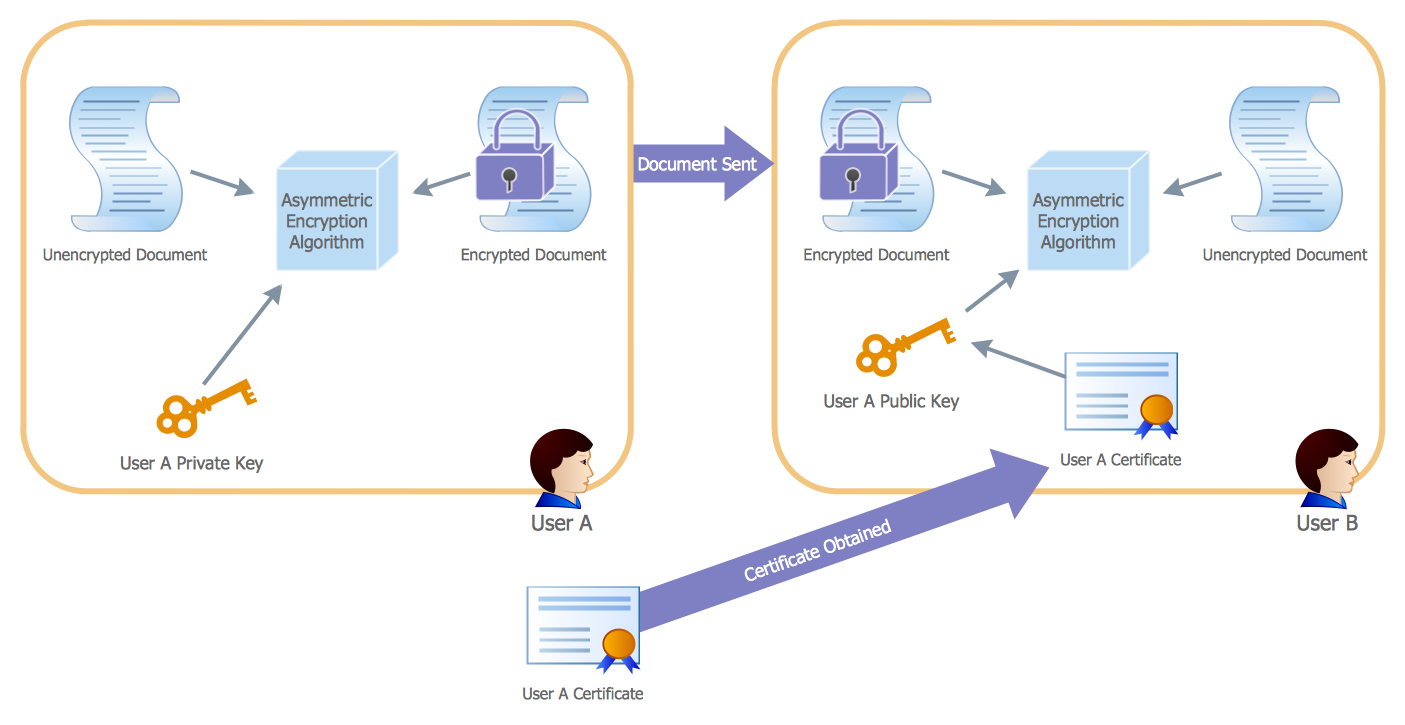
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
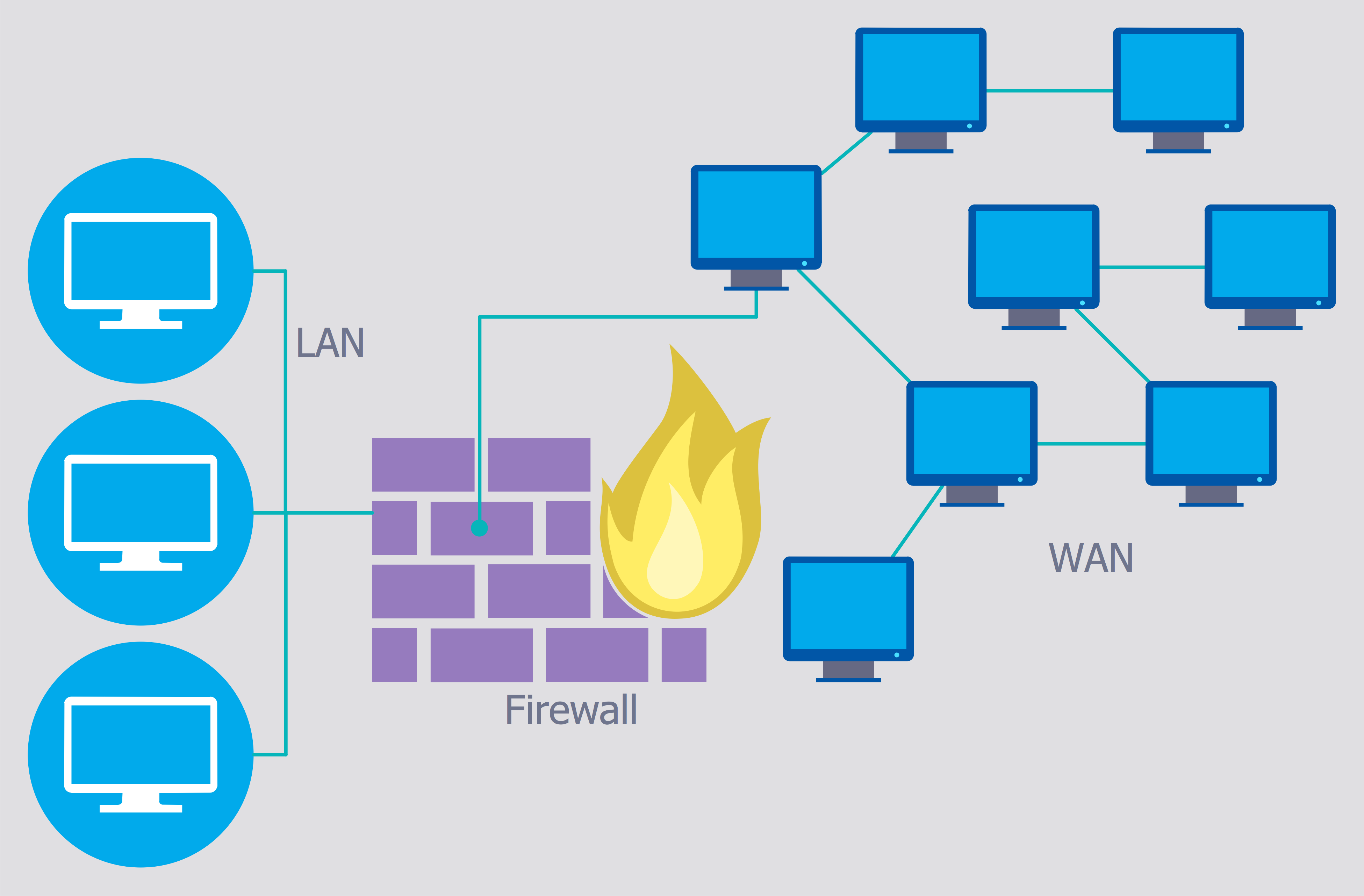
Network Security
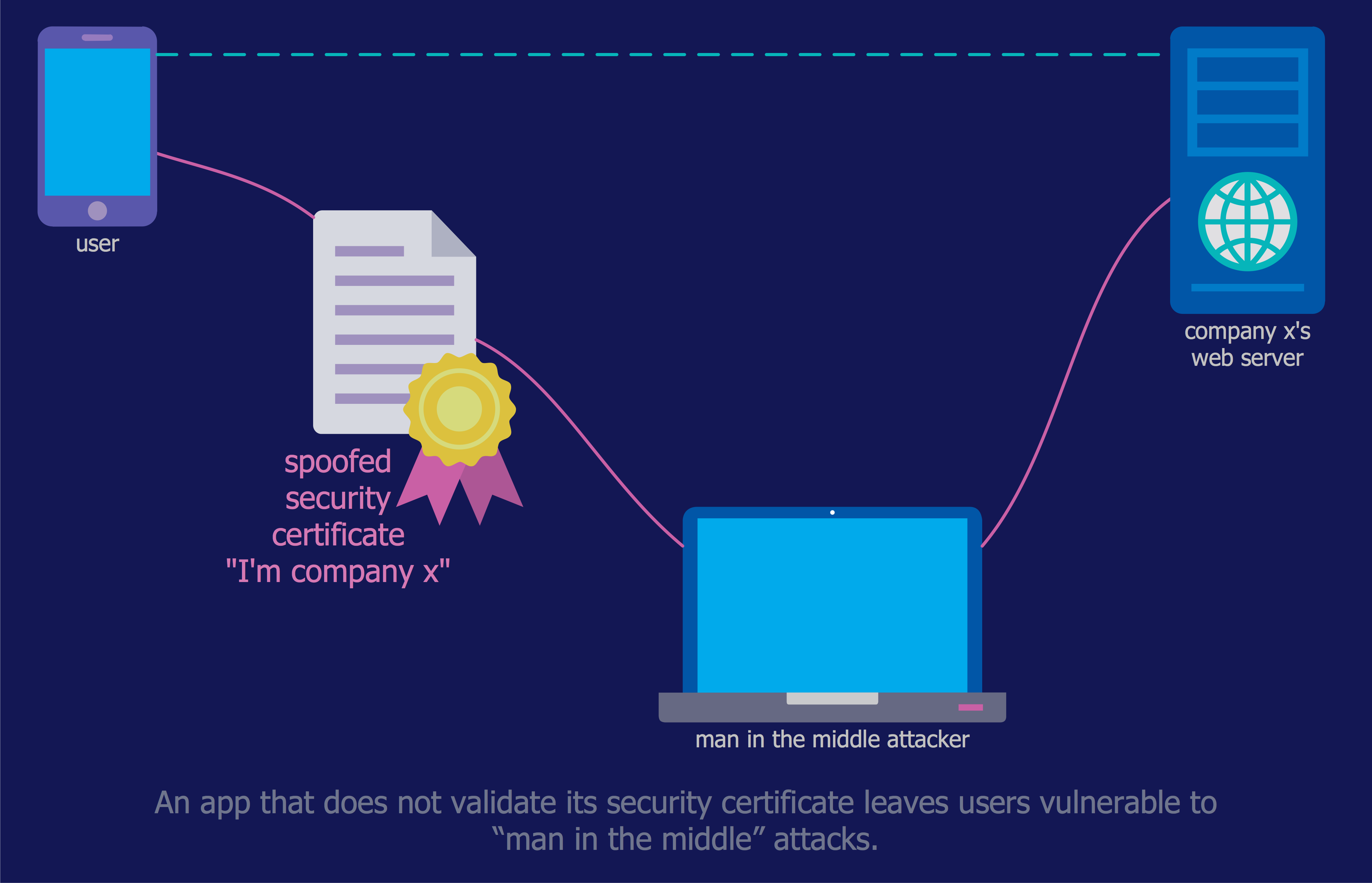
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
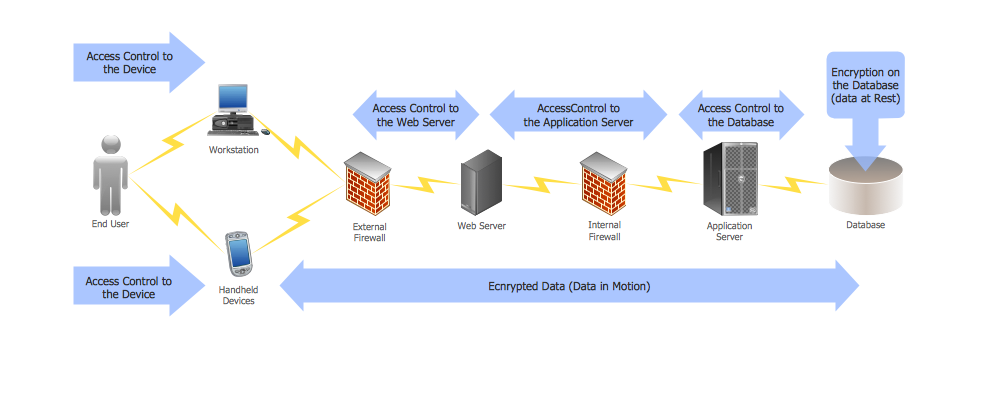
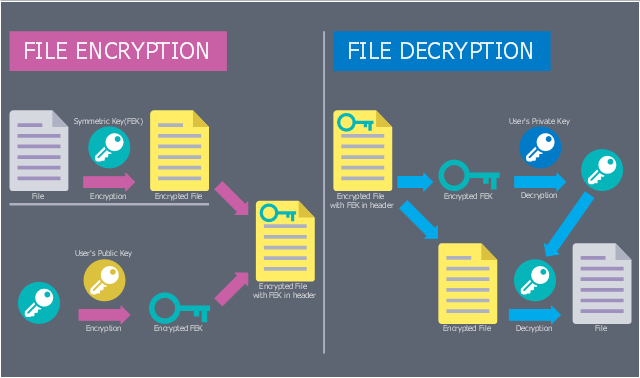
DES Network. Computer and Network Examples
29095The Data Encryption Standard (DES) is a symmetric-key algorithm for the encryption of the electronic data. This diagram was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park and shows how the encryption and access control work together to secure data.
This computer security diagram example was designed on the base of Wikimedia Commons file: EFSOperation.svg.
"Flowchart for the operation of Encrypting File System (EFS)" [commons.wikimedia.org/ wiki/ File:EFSOperation.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
EFS is available in all versions of Windows developed for business environments from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis. Some EFS settings can also be mandated via Group Policy in Windows domain environments." [Encrypting File System. Wikipedia]
The cybersecurity diagram example "EFS Operation" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Flowchart for the operation of Encrypting File System (EFS)" [commons.wikimedia.org/ wiki/ File:EFSOperation.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
EFS is available in all versions of Windows developed for business environments from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis. Some EFS settings can also be mandated via Group Policy in Windows domain environments." [Encrypting File System. Wikipedia]
The cybersecurity diagram example "EFS Operation" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Active Directory Diagrams
Active Directory Diagrams
Active Directory Diagrams solution extends ConceptDraw PRO software with samples, templates and libraries of vector stencils for drawing the AD diagrams to visualize the detail structures of the Microsoft Windows networks.
Active Directory
The Active Directory Diagrams solution from ConceptDraw Solution Park extends ConceptDraw PRO diagramming and vector drawing software to help network engineers, designers and administrators efficiently design and create various active directory diagrams.Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services security, identity and compliance icons.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Using Remote Networking Diagrams
Remote Networking - We explain the method most people use to connect to the Internet.
The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services icons: AWS Directory Service, AWS Config, AWS CloudTrail, AWS Trusted Advisor, Amazon CloudWatch, Alarm. Use it to draw AWS architecture diagrams of your cloud infrastructure services.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Virtual private networks (VPN). Computer and Network Examples
A Virtual Private Network (VPN) is a network that allows the private networks at a remote location securely connect to the public Internet and provide access only to the intended recipients for transmitting data. VPN is built by creating the virtual point-to-point connection using the dedicated connections, traffic encryption or virtual tunneling protocols. This example was created in ConceptDraw PRO using the Computer and Networks Area of ConceptDraw Solution Park and shows the Virtual Private Network (VPN) diagram.
Secure Wireless Network
Use the ConceptDraw PRO diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.- Active Directory diagram - Asymmetric encryption | Active Directory ...
- Active Directory diagram - Asymmetric encryption | Access control ...
- Website launch - Flowchart | Active Directory Diagrams | Network ...
- Active Directory diagram - Asymmetric encryption | Active Directory ...
- Create Flow Chart on Mac | Active Directory diagram - Asymmetric ...
- Draw The Diagram Of Encryption
- Access control and encryption | Network Security Model | Network ...
- How to Build Cloud Computing Diagram Principal Cloud ...
- Active Directory Diagram | Active Directory Domain | Active Directory ...
- EFS Operation | Network Security Diagrams | Network Security ...
- Access Control Diagram
- EFS Operation | Active Directory Diagrams | Active Directory ...
- Network Diagram Software Enterprise Private Network | Network ...
- Hotel Network Topology Diagram . Hotel Guesthouse WiFi Network ...
- Active Directory Diagrams
- Active Directory Diagram
- AWS Architecture Diagrams | AWS Security, Identity and ...
- ConceptDraw Solution Park | Comparing ConceptDraw PRO to ...
- ConceptDraw PRO Network Diagram Tool | Metropolitan area ...
- AD LDS as a phone book service | Active Directory structure ...












-aws-security,-identity-and-compliance---vector-stencils-library.png--diagram-flowchart-example.png)