This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
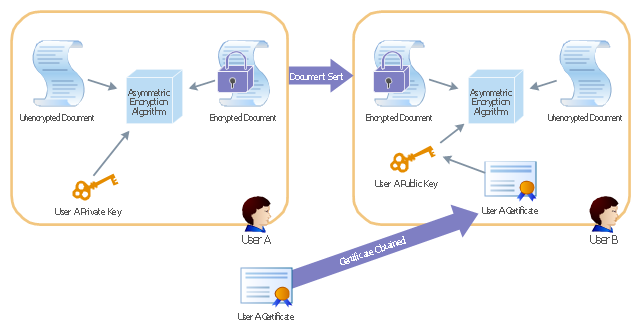
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
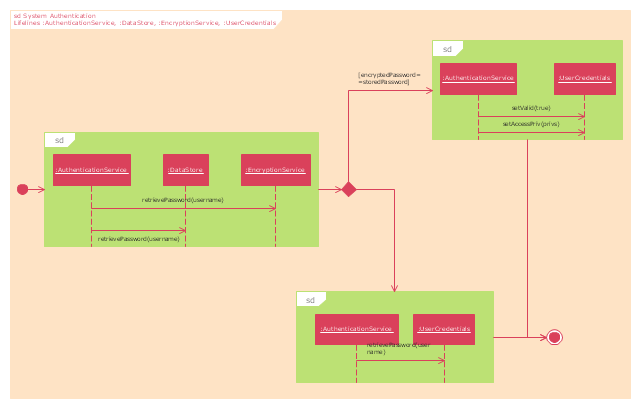
"Authentication ... is the act of confirming the truth of an attribute of a single piece of data (datum) or entity. In contrast with Identification which refers to the act of stating or otherwise indicating a claim purportedly attesting to a person or thing's identity, Authentication is the process of actually confirming that identity. It might involve confirming the identity of a person by validating their identity documents, verifying the validity of a website with a digital certificate, tracing the age of an artifact by carbon dating, or ensuring that a product is what its packaging and labeling claim to be. In other words, Authentication often involves verifying the validity of at least one form of identification." [Authentication. Wikipedia]
The UML interaction overview diagram example "System authentication" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
The UML interaction overview diagram example "System authentication" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
This example was designed on the base of the diagram from the article "How secure is that mobile app?" by N.V. Fleming on the website of the U.S. Federal Trade Commission (FTC).
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
The vector stencils library "LDAP" contains 20 symbols of Lightweight Directory Access Protocol (LDAP) elements for drawing the LDAP Directory Services network structure diagrams.
"The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Directory services play an important role in developing intranet and Internet applications by allowing the sharing of information about users, systems, networks, services, and applications throughout the network. As examples, directory services may provide any organized set of records, often with a hierarchical structure, such as a corporate email directory. Similarly, a telephone directory is a list of subscribers with an address and a phone number.
LDAP is specified in a series of Internet Engineering Task Force (IETF) Standard Track publications called Request for Comments (RFCs), using the description language ASN.1. The latest specification is Version 3, published as RFC 4511. ...
A common usage of LDAP is to provide a "single sign on" where one password for a user is shared between many services, such as applying a company login code to web pages (so that staff log in only once to company computers, and then are automatically logged into the company intranet).
LDAP is based on a simpler subset of the standards contained within the X.500 standard. Because of this relationship, LDAP is sometimes called X.500-lite." [Lightweight Directory Access Protocol. Wikipedia]
The symbols example "LDAP - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Directory services play an important role in developing intranet and Internet applications by allowing the sharing of information about users, systems, networks, services, and applications throughout the network. As examples, directory services may provide any organized set of records, often with a hierarchical structure, such as a corporate email directory. Similarly, a telephone directory is a list of subscribers with an address and a phone number.
LDAP is specified in a series of Internet Engineering Task Force (IETF) Standard Track publications called Request for Comments (RFCs), using the description language ASN.1. The latest specification is Version 3, published as RFC 4511. ...
A common usage of LDAP is to provide a "single sign on" where one password for a user is shared between many services, such as applying a company login code to web pages (so that staff log in only once to company computers, and then are automatically logged into the company intranet).
LDAP is based on a simpler subset of the standards contained within the X.500 standard. Because of this relationship, LDAP is sometimes called X.500-lite." [Lightweight Directory Access Protocol. Wikipedia]
The symbols example "LDAP - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
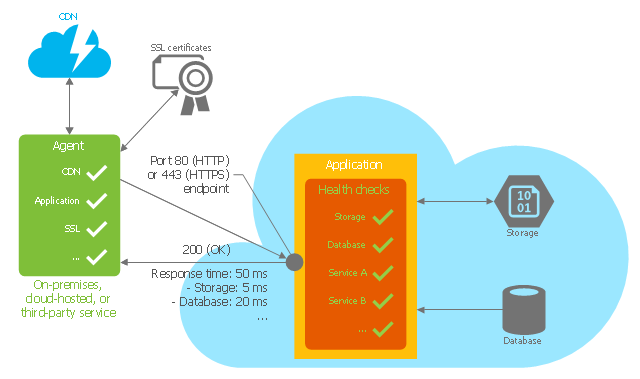
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Health Endpoint Monitoring Pattern" from the Microsoft Developer Network (MSDN) website.
"Health Endpoint Monitoring Pattern.
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly. ...
It is good practice—and often a business requirement—to monitor web applications, and middle-tier and shared services, to ensure that they are available and performing correctly. However, it is more difficult to monitor services running in the cloud than it is to monitor on-premises services. ...
Implement health monitoring by sending requests to an endpoint on the application. The application should perform the necessary checks, and return an indication of its status.
A health monitoring check typically combines two factors: the checks (if any) performed by the application or service in response to the request to the health verification endpoint, and analysis of the result by the tool or framework that is performing the health verification check. The response code indicates the status of the application and, optionally, any components or services it uses. The latency or response time check is performed by the monitoring tool or framework." [msdn.microsoft.com/ ru-RU/ library/ dn589789.aspx]
The Azure cloud system architecture diagram template "Health endpoint monitoring pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Health Endpoint Monitoring Pattern.
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly. ...
It is good practice—and often a business requirement—to monitor web applications, and middle-tier and shared services, to ensure that they are available and performing correctly. However, it is more difficult to monitor services running in the cloud than it is to monitor on-premises services. ...
Implement health monitoring by sending requests to an endpoint on the application. The application should perform the necessary checks, and return an indication of its status.
A health monitoring check typically combines two factors: the checks (if any) performed by the application or service in response to the request to the health verification endpoint, and analysis of the result by the tool or framework that is performing the health verification check. The response code indicates the status of the application and, optionally, any components or services it uses. The latency or response time check is performed by the monitoring tool or framework." [msdn.microsoft.com/ ru-RU/ library/ dn589789.aspx]
The Azure cloud system architecture diagram template "Health endpoint monitoring pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Active Directory" contains 20 symbols of Active Directory objects for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"Objects.
An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The shapes example "Design elements - Active Directory" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Objects.
An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The shapes example "Design elements - Active Directory" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Azure architecture - Deprecated" contains 10 deprecated Microsoft Azure architecture symbols.
Use this cloud computing icon set to design your Azure architecture diagrams with ConceptDraw PRO diagramming and vector drawing software.
The symbols example "Design elements - Azure architecture - Deprecated" is included in the Azure Architecture solution from the Computer and Networks area of ConceptDraw Solution Park.
Use this cloud computing icon set to design your Azure architecture diagrams with ConceptDraw PRO diagramming and vector drawing software.
The symbols example "Design elements - Azure architecture - Deprecated" is included in the Azure Architecture solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector clipart library Aircraft contains 19 images of aerial vehicles and aviation objects. Use the vector stencils library Aircraft to draw aviation illustrations, presentation slides, infographics and diagrams using the ConceptDraw PRO diagramming and vector drawing software. "Civil aviation is one of two major categories of flying, representing all non-military aviation, both private and commercial. Most of the countries in the world are members of the International Civil Aviation Organization (ICAO) and work together to establish common standards and recommended practices for civil aviation through that agency. Civil aviation includes two major categories: - Scheduled air transport, including all passenger and cargo flights operating on regularly scheduled routes; and - General aviation (GA), including all other civil flights, private or commercial. ... Some countries also make a regulatory distinction based on whether aircraft are flown for hire like: - Commercial aviation includes most or all flying done for hire, particularly scheduled service on airlines; and - Private aviation includes pilots flying for their own purposes (recreation, business meetings, etc.) without receiving any kind of remuneration. All scheduled air transport is commercial, but general aviation can be either commercial or private. Normally, the pilot, aircraft, and operator must all be authorized to perform commercial operations through separate commercial licensing, registration, and operation certificates." [Civil aviation. Wikipedia] The design elements library Aircraft is included in the Aerospace and Transport solution from the Illustration area of ConceptDraw Solution Park.
- Work Flow Process Chart | Dfd Diagrams For Transfer Certificate ...
- | Active Directory - Vector stencils library | | Network Security Certificate
- Create Flow Chart on Mac | Entity Relationship Software | Sign ...
- Certificate Template
- Sign Making Software | Create Flow Chart on Mac | Free Certificate ...
- Certificate Design
- Entity Relationship Software | Create Flow Chart on Mac | Sign ...
- Make Your Own Certificate
- Certificate Templates
- Make A Certificate
- Certificates Design
- Certificate Design Software
- Example Of An Tracing Diagram
- UML interaction overview diagram - System authentication ...
- Active Directory - Vector stencils library | Network Glossary Definition ...
- Campus Area Networks (CAN). Computer and Network Examples ...
- | ConceptDraw Arrows10 Technology | Flow chart Example ...
- Active Directory Domain Services | Active Directory Diagram | Single ...
- Active Directory Domain Services | Active Directory Diagram | Active ...