Network Security Model
The network security involves all tools, devices, strategies and activities which enterprises and organizations undertake to protect their networks, data and operations. An effective network security strategy must include the most effective set of tools for identification and reflection various threats and attacks. Creation of well thought-out network security model will effectively help you in realization your network's security. The network security model (NSM) is a scheme that reflects the general plan and the policy of ensuring the network security, and usually includes all or some of the following seven layers in different modifications according to the specific company's needs:
- Physical layer — involves organization of physical security against the access to the data on computer devices, this can be access control devices, cameras, alarm.
- VLAN layer — involves creation of Virtual Local Area Networks (VLANs) which join together common hosts for security purposes.
- ACL layer — supposes creation and maintenance of Access Control Lists (ACLs) which allow or deny the access between hosts on different networks.
Software layer — helps to protect the user layer and ensures the software's actuality.
- User layer — involves the user’s training of security on the network.
- Administrative layer — supposes the training of administrative users.
- IT department layer — this layer is the most important for network security, it contains all network security professionals and support specialists, network technicians and architects, which organize and maintain the work of the network and hosts.
Pay please your attention for the powerful ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park which lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.
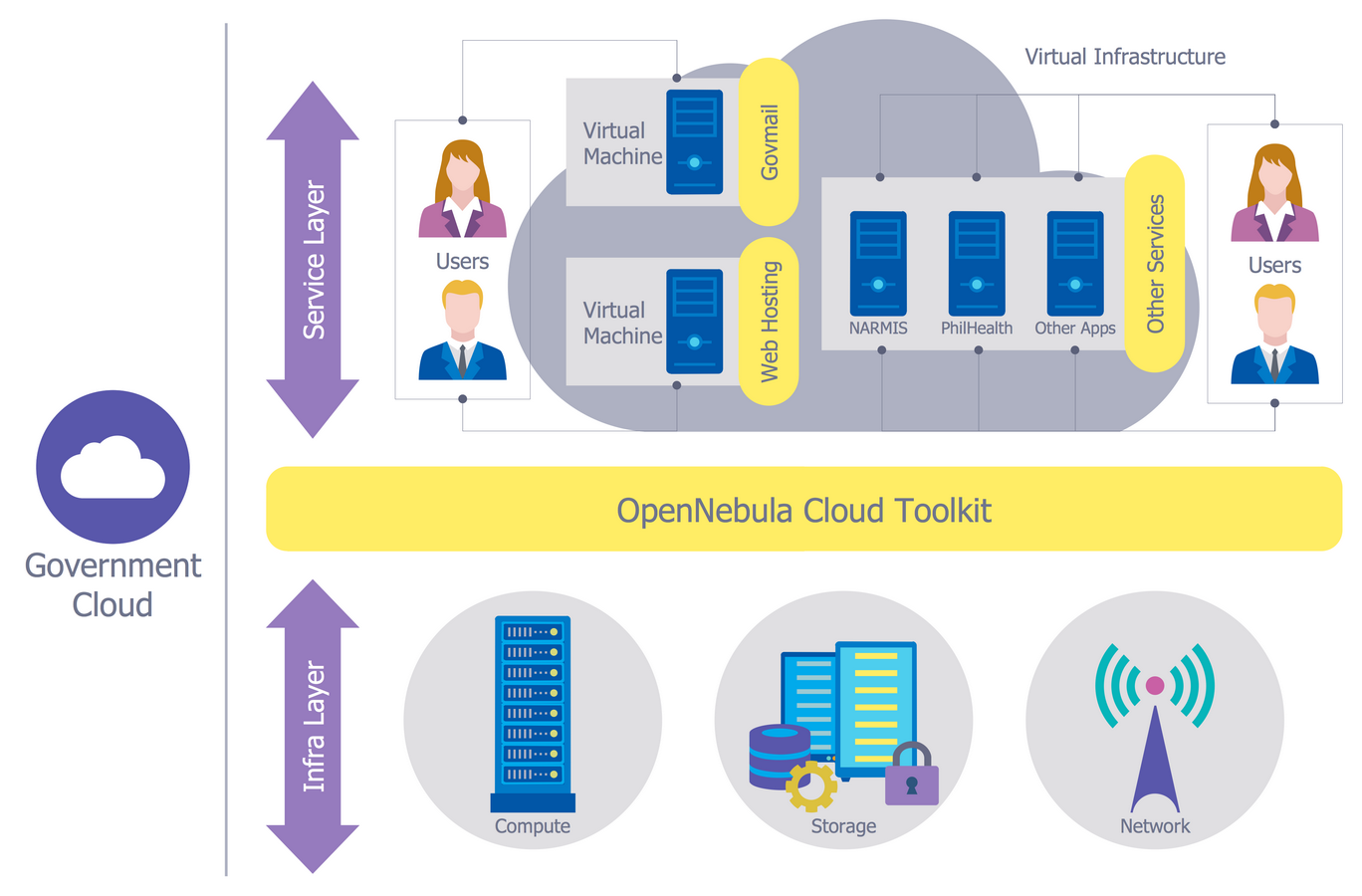
Example 1. Network Security Model
To design the Network Security Model, we recommend to use already ready-to-use 460 predesigned colorful vector objects offered by 4 libraries of the Network Security Diagrams Solution:
- Cybersecurity Clipart
- Cybersecurity Shapes
- Cybersecurity Connectors
- Cybersecurity Round Icons
Simply drag desired objects from the libraries to your document, arrange them, depict relationships between devices with help of connectors from the Cybersecurity Connectors library, type the text and make your diagram more attractive with help of bright colors applied for objects, connectors and background.
Example 2. Network Security Diagrams Solution in ConceptDraw STORE
One more useful way for inspiration and excellent start for drawing Network Security Diagrams and Network Security Model is collection of predesigned network security samples and examples offered by Network Security Diagrams Solution in ConceptDraw STORE.
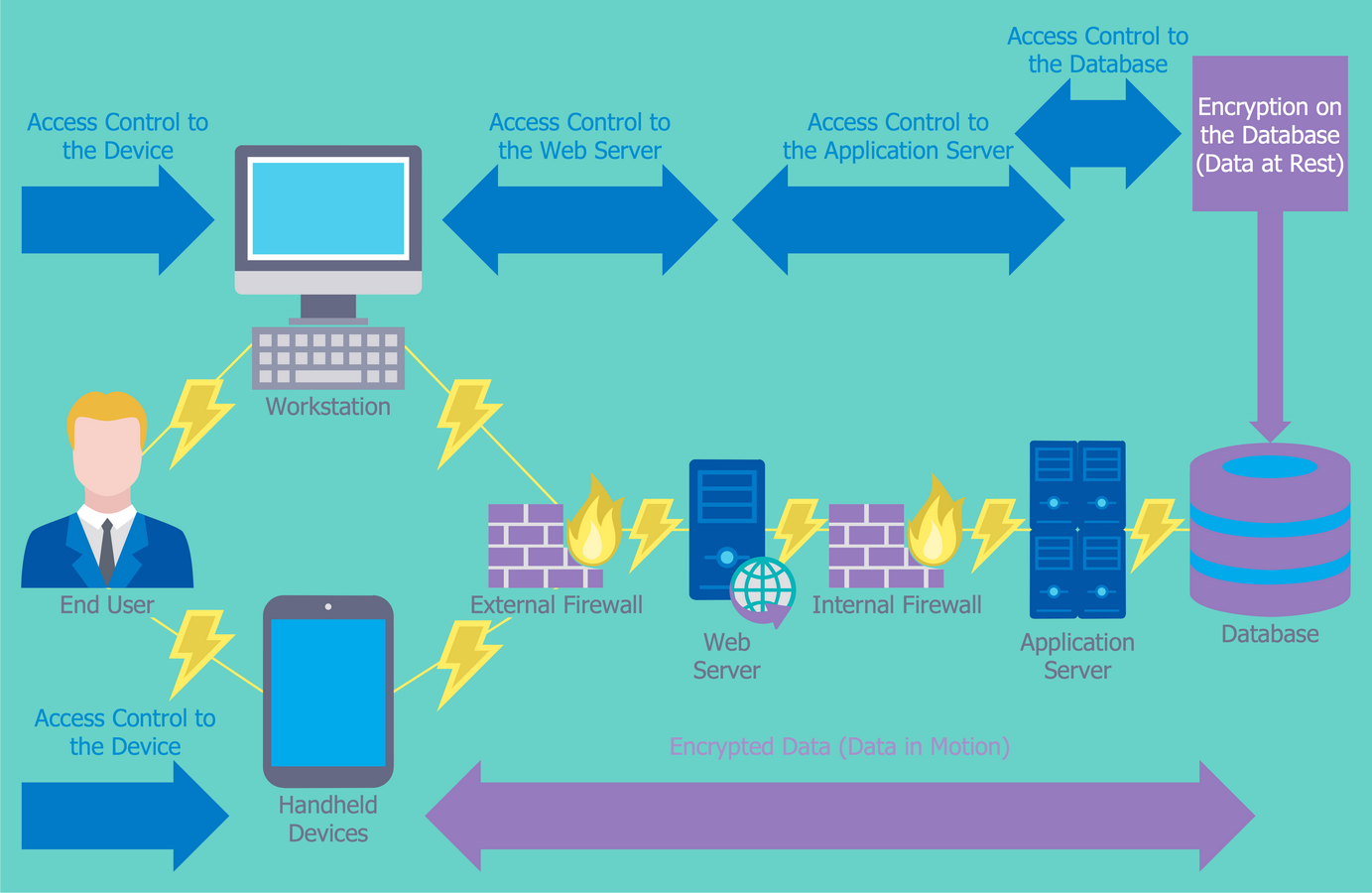
Example 3. Network Security Diagram — Access Control and Encryption
The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. An experienced user spent 10 minutes creating each of these samples.
Use the Network Security Diagrams Solution for ConceptDraw DIAGRAM to create your own Network Security Model and Network Security Diagrams quick, easy and effective.
All source documents are vector graphic documents. They are available for reviewing, modifying, or converting to a variety of formats (PDF file, MS PowerPoint, MS Visio, and many other graphic formats) from the ConceptDraw STORE. The Network Security Diagrams Solution is available for all ConceptDraw DIAGRAM users.
TEN RELATED HOW TO's:
ConceptDraw - Perfect Network Diagramming Software with abundant examples and templates. ConceptDraw Network Diagram is ideal for network engineers and network designers who need to draw Enterprise Private Network diagrams.
Picture: Network Diagram SoftwareEnterprise Private Network
Related Solution:
29095The Data Encryption Standard (DES) is a symmetric-key algorithm for the encryption of the electronic data.
This diagram was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park and shows how the encryption and access control work together to secure data.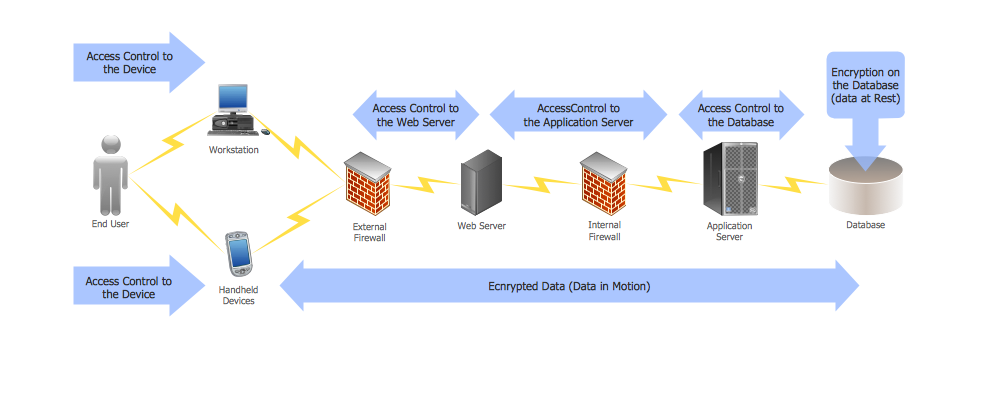
Picture: DES Network. Computer and Network Examples
Related Solution:
Of course it is possible to keep network records in text documents, but it is very difficult to use them later. A more sound way to keep such documentation is to create a network diagram that might represent either logical network structure or physical. These diagrams are easy to understand and you will thank yourself later.
There is a physical network diagram. It is a tool to represent, maintain and analysis of network equipment and interconnections. Network diagram depicts the actual network information in the attractive clear graphic form. One can learn here the LAN cable length, telecommunication type and carrying capacity. The diagram depicts servers, IP address and domain name as well. Also it shows location of hubs, switches, modems, routers, and other network equipment. The sets of special symbols and images delivered with ConceptDraw Network Diagrams solution are used to show network components. Symbols have a standard view. Therefore, various specialists can read the network diagram without any discrepancies.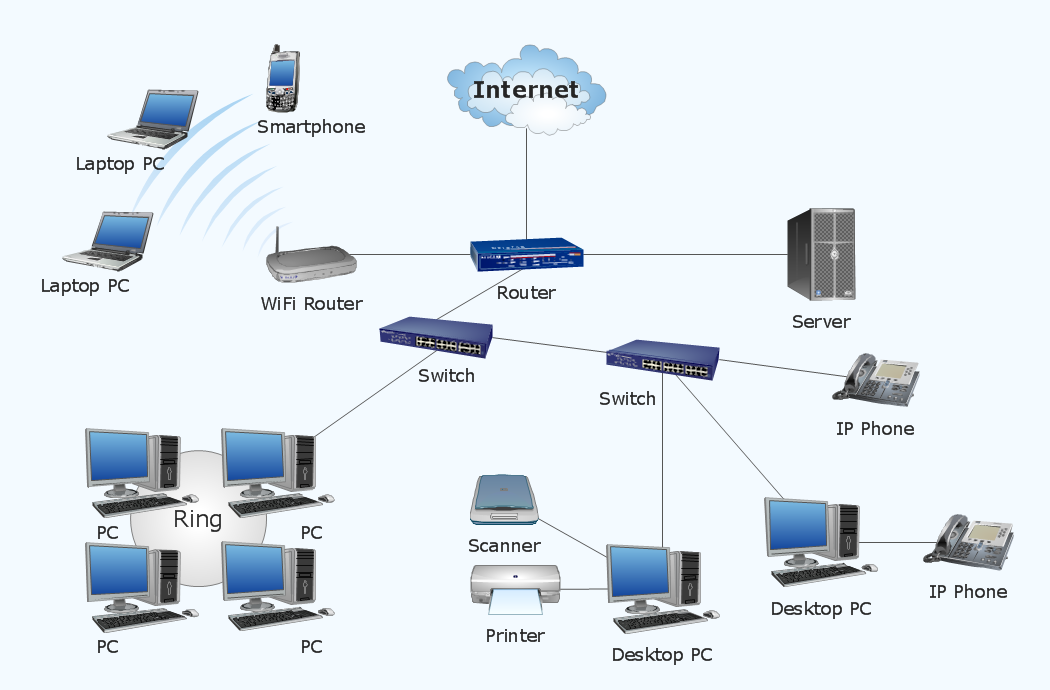
Picture: Network diagrams with ConceptDraw DIAGRAM
Related Solution:
ConceptDraw is a good means of visualization of information of any kind as it features powerful graphic capabilities. The conception of using ConceptDraw and open formats by the programs that work with Internet can be used for displaying any data and any structure in Internet.
Picture: Internet solutions with ConceptDraw DIAGRAM
The modern garden design is a full complex of works for design, decorating and gardening. Landscape design offers a large number of styles for the modern garden design, their origins go back centuries. But do not forget that the modern garden design is first of all an individual project for a specific landscape and specific owner of the land, and sometimes it is appropriate to apply the combination of styles.
ConceptDraw DIAGRAM diagramming and vector drawing software offers the unique Landscape & Garden Solution from the Building Plans area for effective development the modern garden design.
Picture: Modern Garden Design
Related Solution:
The following examples cctv network were created in ConceptDraw DIAGRAM diagramming and vector drawing software using the Audio, Video, Media Solution. Using this easily customizable cctv network template you can represent any existing cctv network.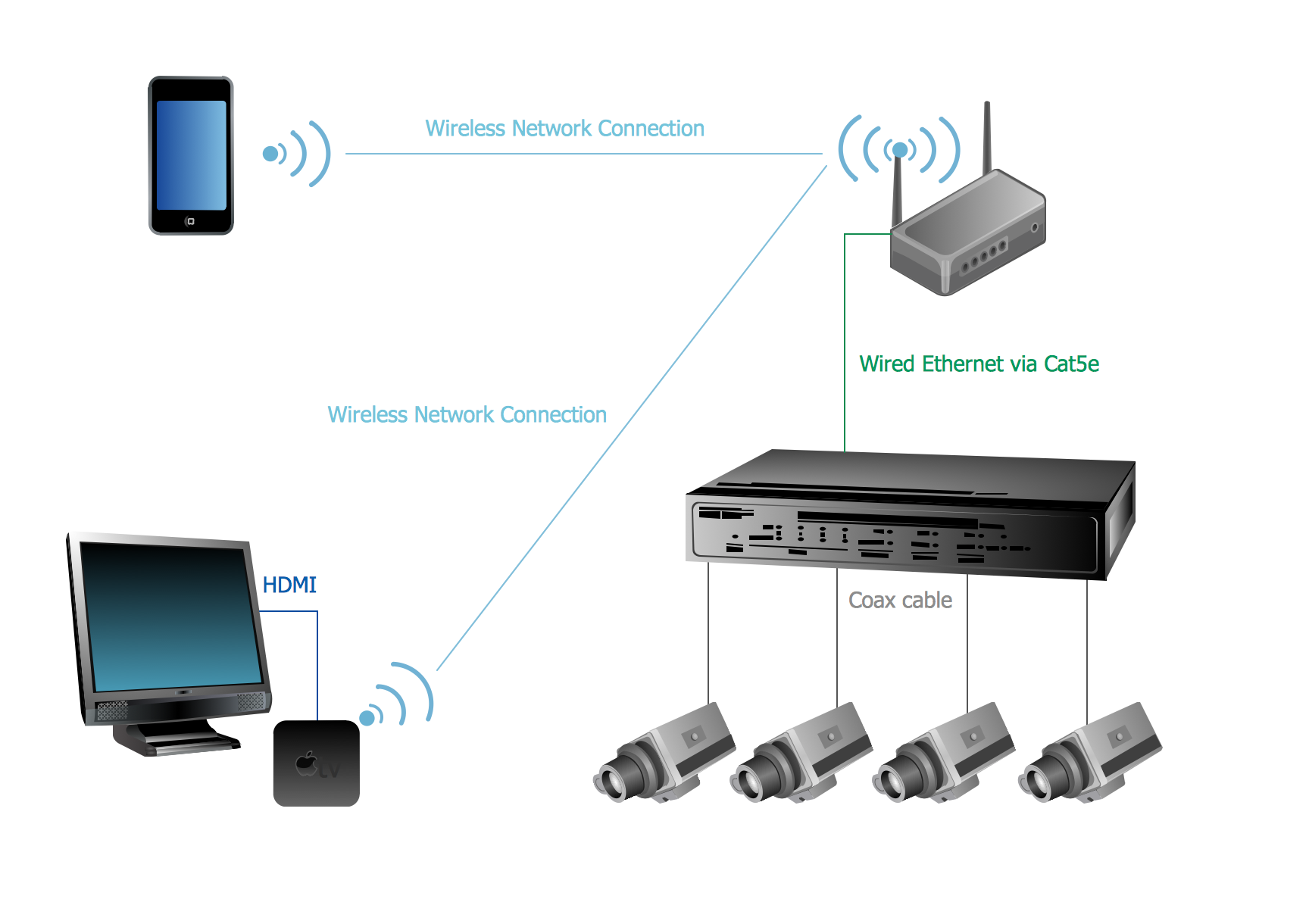
Picture: CCTV Network Example
Related Solutions:
ConceptDraw DIAGRAM diagramming and vector drawing software extended with Computer Network Diagrams Solution from the Computer and Networks Area offers a set of useful tools, collection of templates, samples, and libraries of various computer symbols, computer devices icons, computer network icon for fast and easy drawing network computer diagrams and illustrations.
Picture: Network Icon
Related Solution:
There are many ways to track the system in a critical situation. To model a system behavior, uml notation is widely used. Usually, an UML diagram consists of elements such as actor and a case.
This diagram represents the structure of UML notations. Unified Modeling Language (UML) is used in software engineering to depict graphically the software modeling process. UM Language uses graphic notations for developing models of object-oriented systems. These notations displays requirements, sub-systems, logical and physical elements, etc. We created this diagram using ConceptDraw DIAGRAM reinforced with Rapid UML solution. It can be helpful for students on software engineering, when learning UML.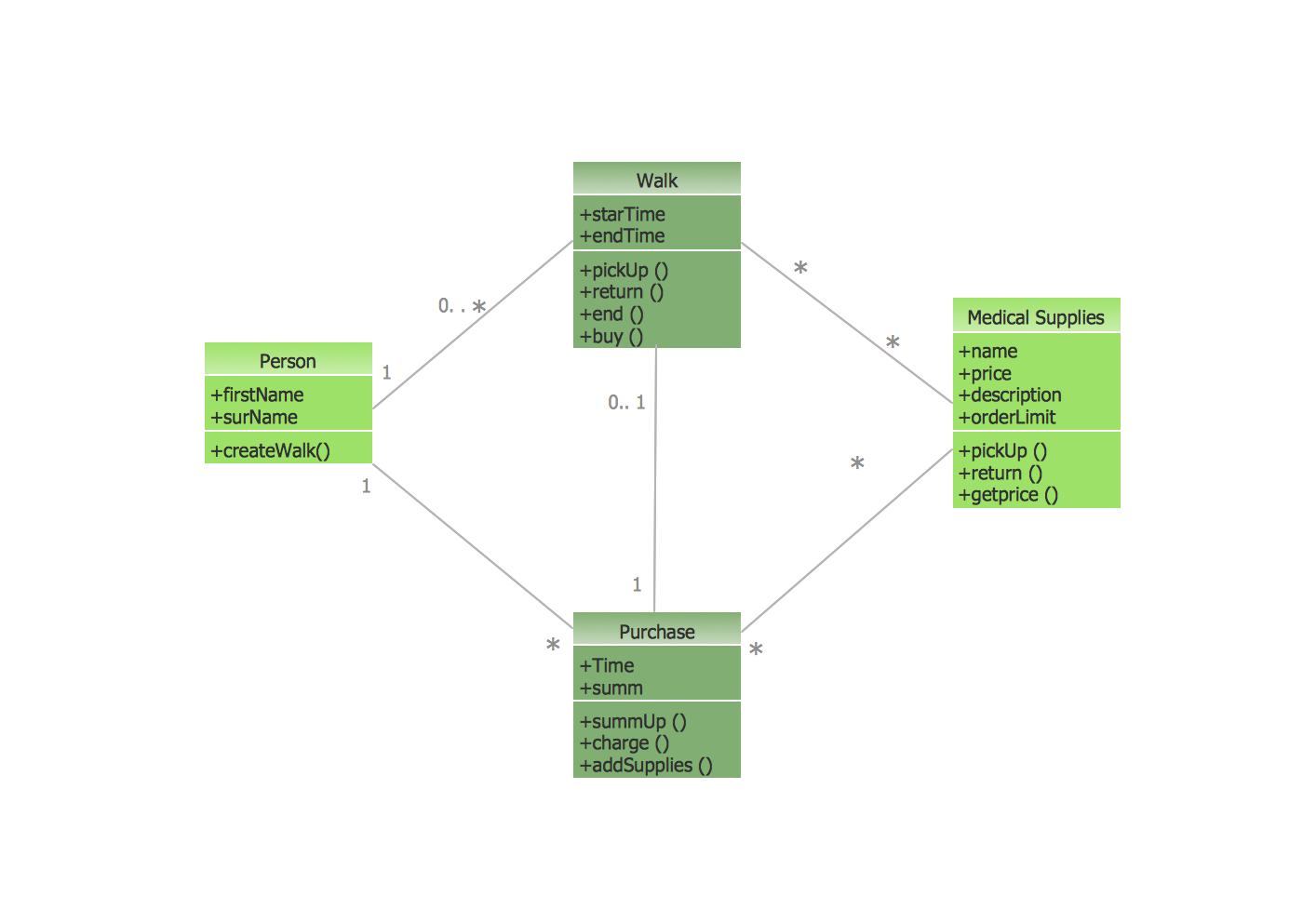
Picture: UML Notation
Related Solution:
UML Diagrams Social Networking Sites Project. This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the UML Use Case Diagram library of the Rapid UML Solution from the Software Development area of ConceptDraw Solution Park.
This sample shows the Facebook Socio-health system and is used at the projection and creating of the social networking sites.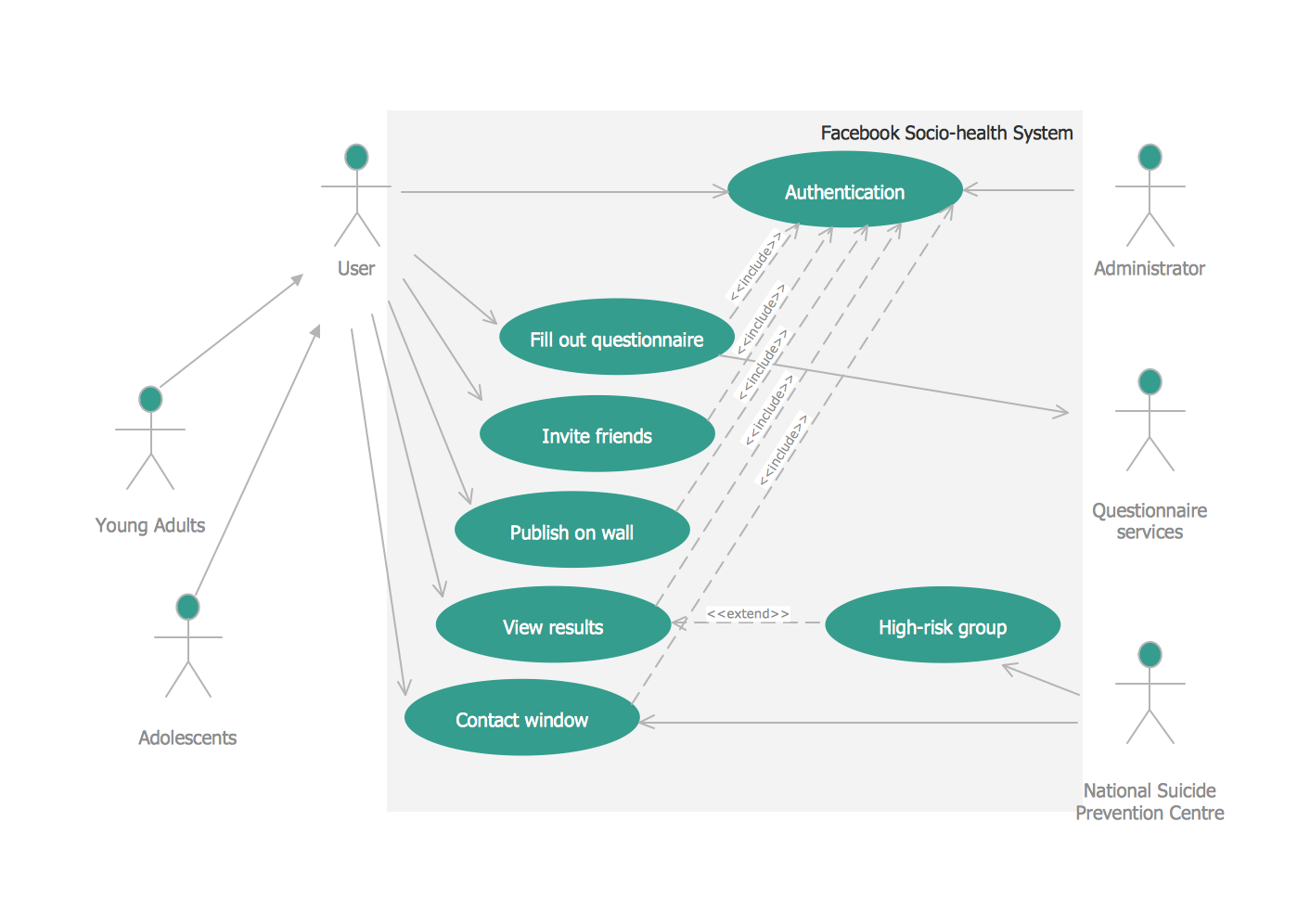
Picture: UML Use Case Diagram Example. Social Networking Sites Project
Related Solution:
It’s not easy to plan all the details of your landscape at once. Therefore, you can use a bubble diagram to create a draft of the future project. You can develop any bubble diagrams and use them in your landscape design project with ConceptDraw DIAGRAM and it’s predesigned templates.
This bubble diagram can be applied while initiating the development of garden and landscape design. The bubble diagrams used for this purpose are different from the classic bubble diagrams. Being used in landscape and garden design, they obtain the quite another understanding. Bubbles in this diagram visualize some captured areas, which define the general spaces of a future garden: lawn, flower garden, pool, built-up area, lighting, etc. The bubble diagram represents the landscape project without any special expenses on its creation. It is better to make such simple sketch before you drill down into detailed project and cost estimates.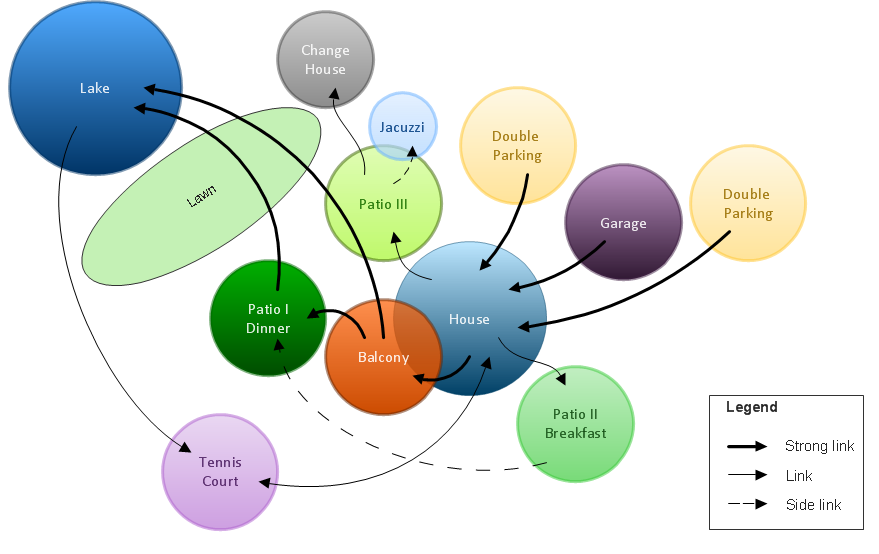
Picture: Bubble diagrams in Landscape Design with ConceptDraw DIAGRAM












