Network Security Devices
Assurance of network security is one of the most important moments for safe and correct working of the computer systems and networks. The network security includes assurance of the limited access to sensitive information, the protection from unauthorized access, risks and potential security threats, and enhancement of network performance. It is necessary to protect the network at all of its entry points, the most important factors in network security are encryption, reliable passwords, the use of antivirus software and modern advanced network security devices.
There are few types of network security devices:
- active devices - firewalls, antivirus scanning devices, content filtering devices, which block the surplus traffic;
- passive devices, such as intrusion detection appliances, which identify and report on unwanted traffic;
- preventative devices - penetration testing devices and vulnerability assessment appliances, which scan the networks and identify potential security problems;
- Unified Threat Management (UTM) devices, such as firewalls, content filtering, web caching, which serve as all-in-one security devices.
The most popular network security devices are firewalls - network security systems which establish a barrier between an internal network and the Internet, effectively manage and regulate the network traffic based on some protocols. Firewall can be software or hardware appliance, or include together hardware and software devices, most computers use software-based firewalls to secure their data from Internet threats, many routers also contain the firewall components.
Such network security devices as routers, crypto-capable routers, virtual private network gateways, secure modems and intrusion detection systems are also very popular. Intrusion detection systems are devices that monitor malicious activities in a network, log information about such activities and take active steps to stop them, and then report them.
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.

Example 1. Network Security Devices
The drawing tools of Network Security Diagrams Solution are very useful for network security design. This solution offers large collection of predesigned vector security clipart, icons, connectors and vector objects of network security devices developed by professional designers specially for ConceptDraw DIAGRAM users. All these 460 vector objects are grouped in 4 libraries:
- Cybersecurity Clipart
- Cybersecurity Round Icons
- Cybersecurity Shapes
- Cybersecurity Connectors

Example 2. Cybersecurity Clipart Library Design Elements
Each of these objects is ready-to-use. All that you need is simply double-click the icon at the library to add the chosen object in a moment to the middle of your document. Another way is to drag desired object from the library to the document page. Then you can arrange the objects, connect the objects in a desired way, add the text and make formatting changes.

Example 3. Network Security Diagram - Government Cloud Diagram
The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software and demonstrate network security schemes with using the network security devices. An experienced user spent 10 minutes creating each of these samples.
Use the Network Security Diagrams Solution for ConceptDraw DIAGRAM to create your own Network Security Diagrams quick, easy and effective.
All source documents are vector graphic documents. They are available for reviewing, modifying, or converting to a variety of formats (PDF file, MS PowerPoint, MS Visio, and many other graphic formats) from the ConceptDraw STORE. The Network Security Diagrams Solution is available for all ConceptDraw DIAGRAM users.
TEN RELATED HOW TO's:
An inductor, also called a coil or reactor, is a passive two-terminal electrical component which resists changes in electric current passing through it. It consists of a conductor such as a wire, usually wound into a coil. Energy is stored in a magnetic field in the coil as long as current flows. When the current flowing through an inductor changes, the time-varying magnetic field induces a voltage in the conductor, according to Faraday’s law of electromagnetic induction.
26 libraries of the Electrical Engineering Solution of ConceptDraw DIAGRAM make your electrical diagramming simple, efficient, and effective. You can simply and quickly drop the ready-to-use objects from libraries into your document to create the electrical diagram.
Picture: Electrical Symbols — Inductors
Related Solution:
ConceptDraw DIAGRAM is a world-class diagramming platform that lets you display, communicate, and present dynamically. It′s powerful enough to draw everything from basic flowcharts to complex engineering schematics.
Video tutorials on ConceptDraw products. Try it today!
Picture: Business Process Mapping — How to Map a Work Process
Related Solutions:
You want design the Information Architecture and need a powerful software for this? ConceptDraw DIAGRAM extended with Enterprise Architecture Diagrams Solution from the Management Area is exactly what you need.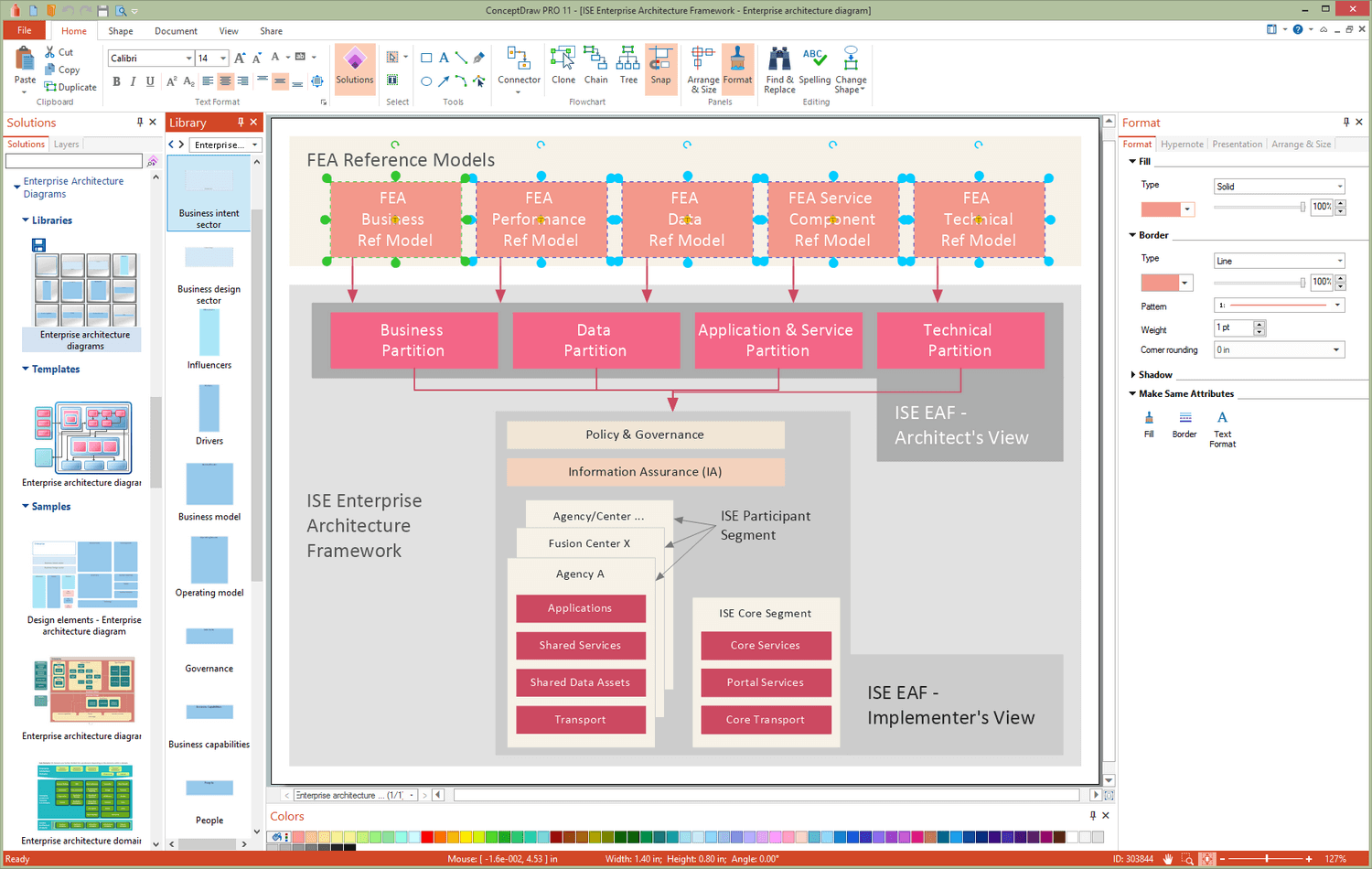
Picture: Information Architecture
Related Solution:
A concept map is a way of representing relationships between ideas, images, or words.
How to draw a Concept Map quick, easy and effective? ConceptDraw DIAGRAM offers the unique Concept Maps Solution from the Diagrams Area that will help you!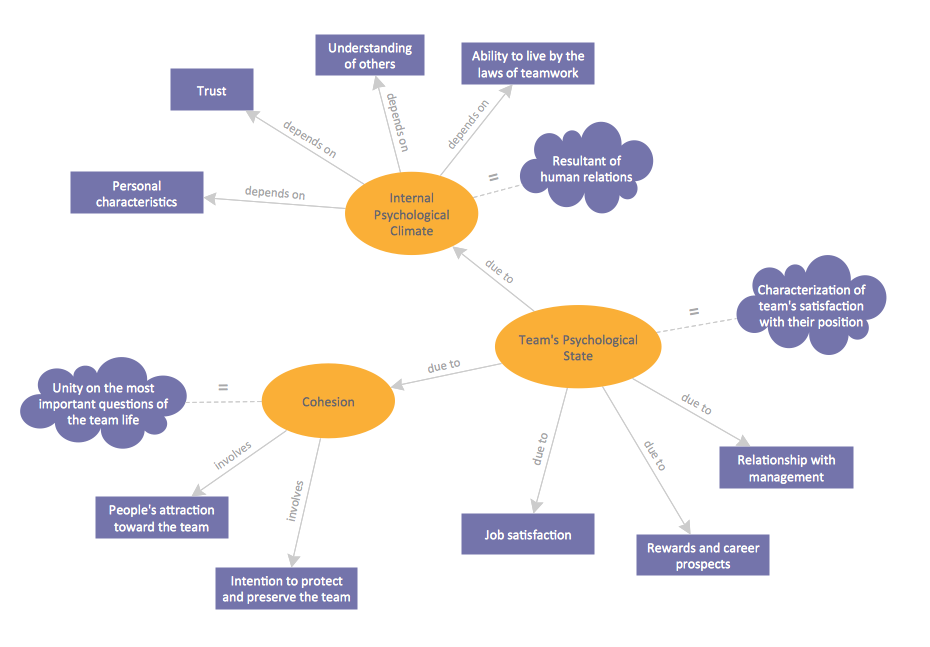
Picture: Concept Map
Related Solution:
ERD drawing becomes easier with predesigned entity relationship symbols, work flow shapes, entity relationship stencils. All variety of ERD symbols you may need for ERDs design is packed into libraries and templates from Entity-Relationship Diagram (ERD) Solution for ConceptDraw DIAGRAM diagramming and vector drawing software.
But anyone have an ERD symbols quick reference? Detailed reference information for them is represented at the tables.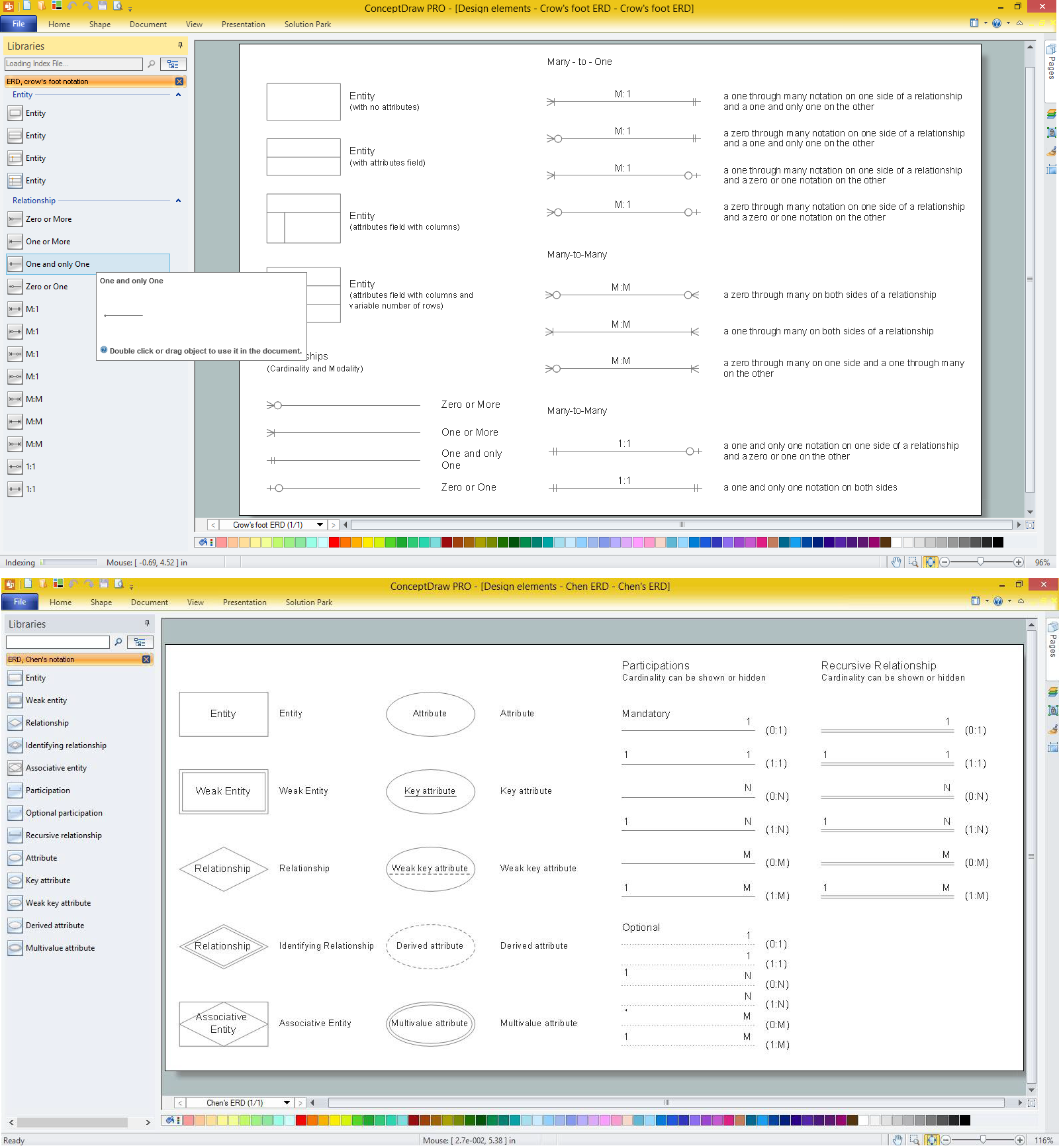
Picture: Anyone Have an ERD Symbols Quick Reference?
Related Solution:
Activity Network Diagram - This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the Seven Management and Planning Tools solution from the Management area of ConceptDraw Solution Park.
This sample shows the PERT (Program Evaluation Review Technique) chart of the request on proposal. A request for proposal (RFP) is a request of the company or the organization to potential suppliers to submit the business proposals for service or goods that it is interested to purchase. The RFP is represented on the initial procurement stage and allows to define the risks and benefits.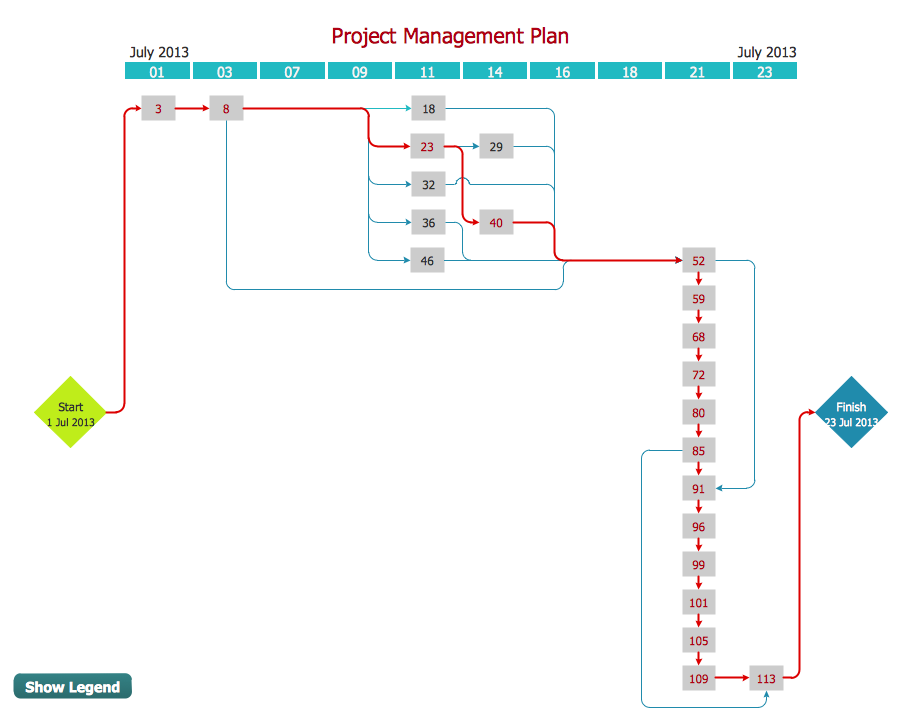
Picture: Activity Network Diagram Method
Related Solution:
A Wireless network is a type of the computer network that uses the wireless connections for connecting network nodes for data transfer. The wireless networks are very useful, inexpensive, popular and widely used. They are easy setup and do not require the cables installation.
Using the solutions of the Computer and Networks Area for ConceptDraw DIAGRAM you can design the wireless network diagrams of any complexity quick and easy.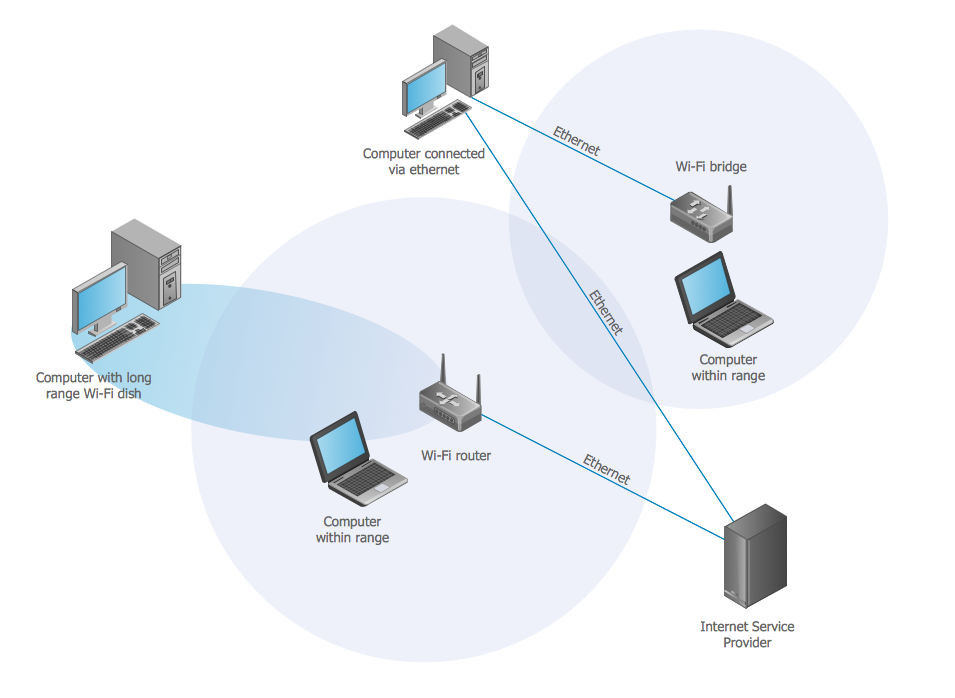
Picture: Wireless network. Computer and Network Examples
Related Solution:
A block diagram is a diagram of a system in which the principal parts or functions are represented by blocks connected by lines that show the relationships of the blocks. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Block Diagrams Solution from the Diagrams Area is a powerful Block Diagram Creator.
Picture: Block Diagram Creator
Related Solution:
ConceptDraw DIAGRAM diagramming and vector drawing software extended with Wireless Networks Solution gives the ability to its users to create professional looking WLAN schemes and diagrams quick and easy.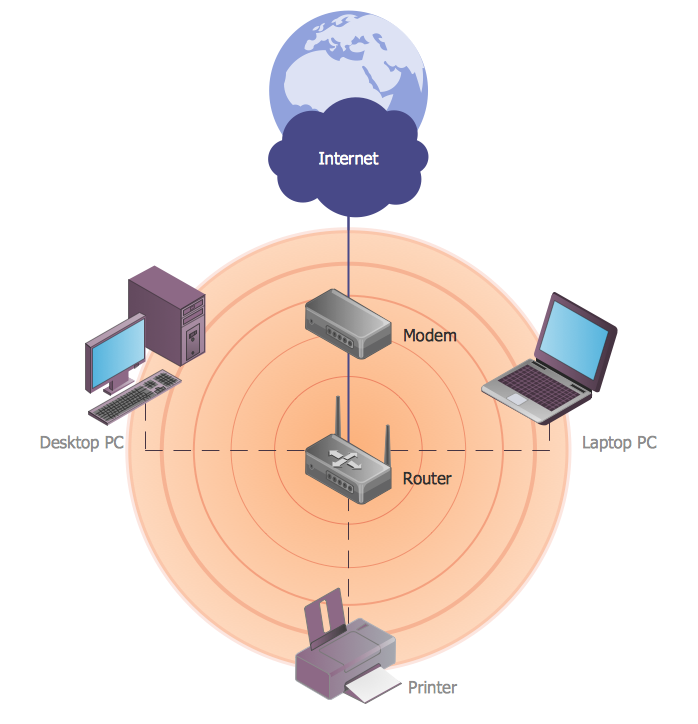
Picture: WLAN
Related Solution:
Learn about Virtual Private Networks (VPNs), and how they work, exploring VPN Networks with diagrams. ✔️ How to create VPN flowcharts using the ConceptDraw DIAGRAM software?
Picture:
What is a Virtual Private Network?
VPN Diagram Examples
Related Solution:












