Active Directory Diagrams
Active Directory Diagrams
Active Directory Diagrams solution significantly extends the capabilities of ConceptDraw DIAGRAM software with special Active Directory samples, convenient template and libraries of Active Directory vector stencils, common icons of sites and services, icons of LDPA elements, which were developed to help you in planning and modelling network structures and network topologies, in designing excellently looking Active Directory diagrams, Active Directory Structure diagrams, and Active Directory Services diagram, which are perfect way to visualize detailed structures of Microsoft Windows networks, Active Directory Domain topology, Active Directory Site topology, Organizational Units (OU), and Exchange Server organization.
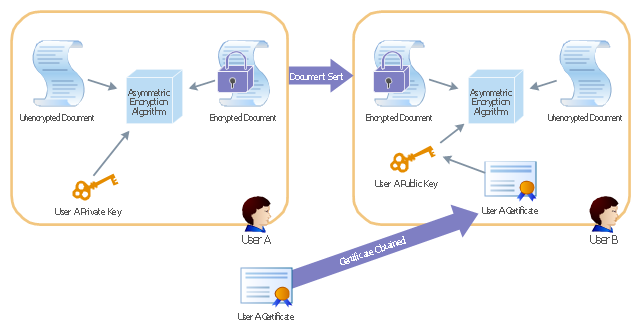
This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Software and Database Design with ConceptDraw DIAGRAM
Unified Modeling Language (abbr. UML) is a modeling language used by software developers and software engineers for developing diagrams, expressive modeling, visualization, construction, specification, and documentation an information about software-intensive systems. There are used many types of UML diagrams, joined in main groups, each of them has its own functional abilities and applications: Behaviour diagrams illustrate the functionality of software systems, Structuring diagrams depict a structure of objects at the systems, Interaction diagrams show the flow of control and data among the things in a modeling system. UML has a lot of practical applications in varied areas, among them software development, hardware design, banking and financial services, telecommunication, science, research, enterprise information system, distributed Web-based services, user interfaces for web applications, medical electronics, patient healthcare systems, etc. ConceptDraw DIAGRAM extended with Rapid UML solution is a perfect tool for UML diagramming.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
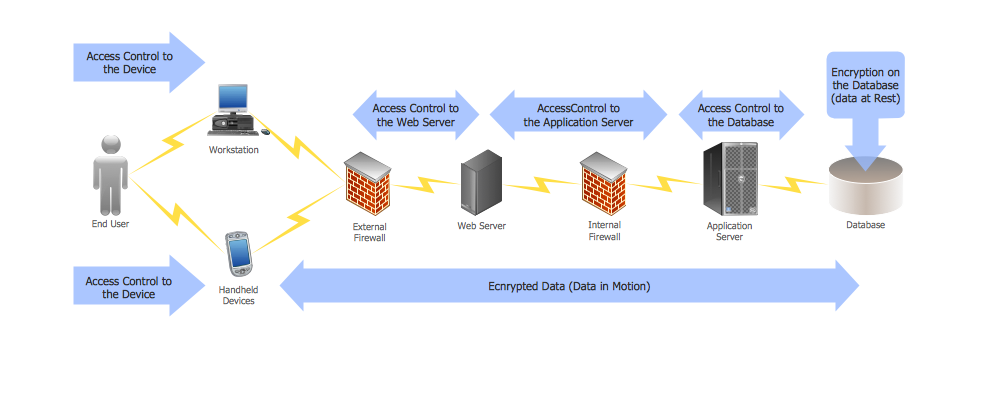
DES Network. Computer and Network Examples
29095The Data Encryption Standard (DES) is a symmetric-key algorithm for the encryption of the electronic data. This diagram was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park and shows how the encryption and access control work together to secure data.
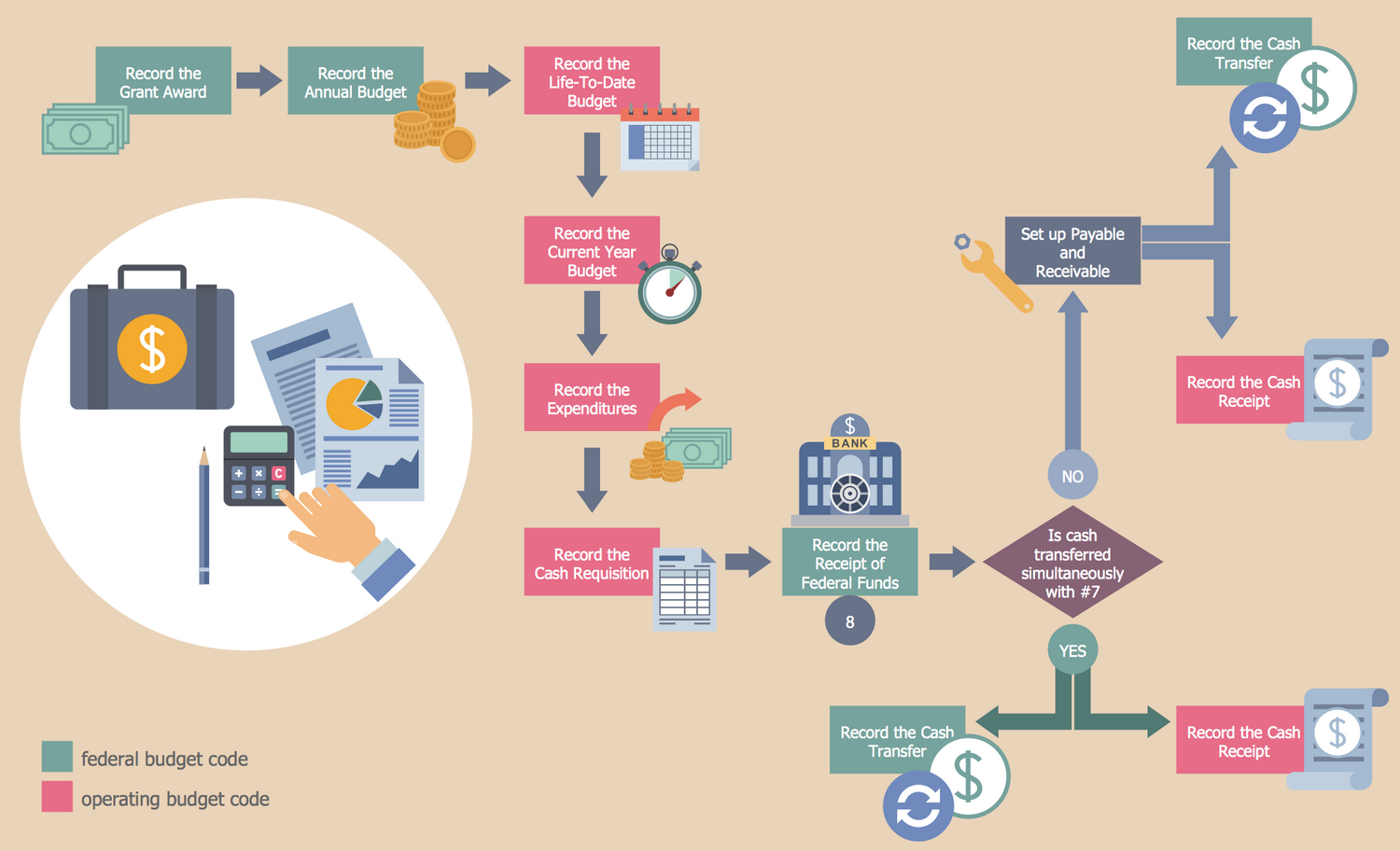
Business Process Flow Diagram
Business Process Flow Diagram is a graphical presentation of business processes and process flows. It is one of the main tool of business analysis and business process re-engineering that lets identify and easy understand process flows within organization. ConceptDraw DIAGRAM extended with Business Process Workflow Diagrams solution from the Business Processes area of ConceptDraw Solution Park is a powerful software which lets easy design Business Process Flow Diagram of any complexity.Using Remote Networking Diagrams
Remote Networking - We explain the method most people use to connect to the Internet.
House of Quality Matrix Software
House of Quality Matrix Software - Use the predesigned objects from the Involvement Matrix Objects Library from the Seven Management and Planning Tools Solution to create professional looking House of Quality Matrices in minutes.Process Flow Chart Symbol
Process Flow Charts are very popular and widely used in chemical and process engineering for representation a general flow of plant processes and equipment. If you need often draw them, the ConceptDraw DIAGRAM diagramming and vector drawing software extended with tools of Flowcharts Solution will be useful for you. The mostly used set of process flow chart symbols includes the following: Rectangle (box) process flow chart symbol, Rounded rectangle, Circle, Diamond.- Flowchart For Encryption Process
- Active Directory Diagrams | Asymmetric Encryption Flowchart
- Er Diagram For Image Encryption
- Network Security Diagrams | Network Security Model | IT Security ...
- Active Directory diagram - Asymmetric encryption | Design elements ...
- Entity-Relationship Diagram (ERD) | How to Help Customers be ...
- EFS Operation | Active Directory Diagrams | ConceptDraw Arrows10 ...
- How to Build Cloud Computing Diagram Principal Cloud ...
- AD LDS as a phone book service | Active Directory structure ...
- How To Create a MS Visio Business Process Diagram Using ...