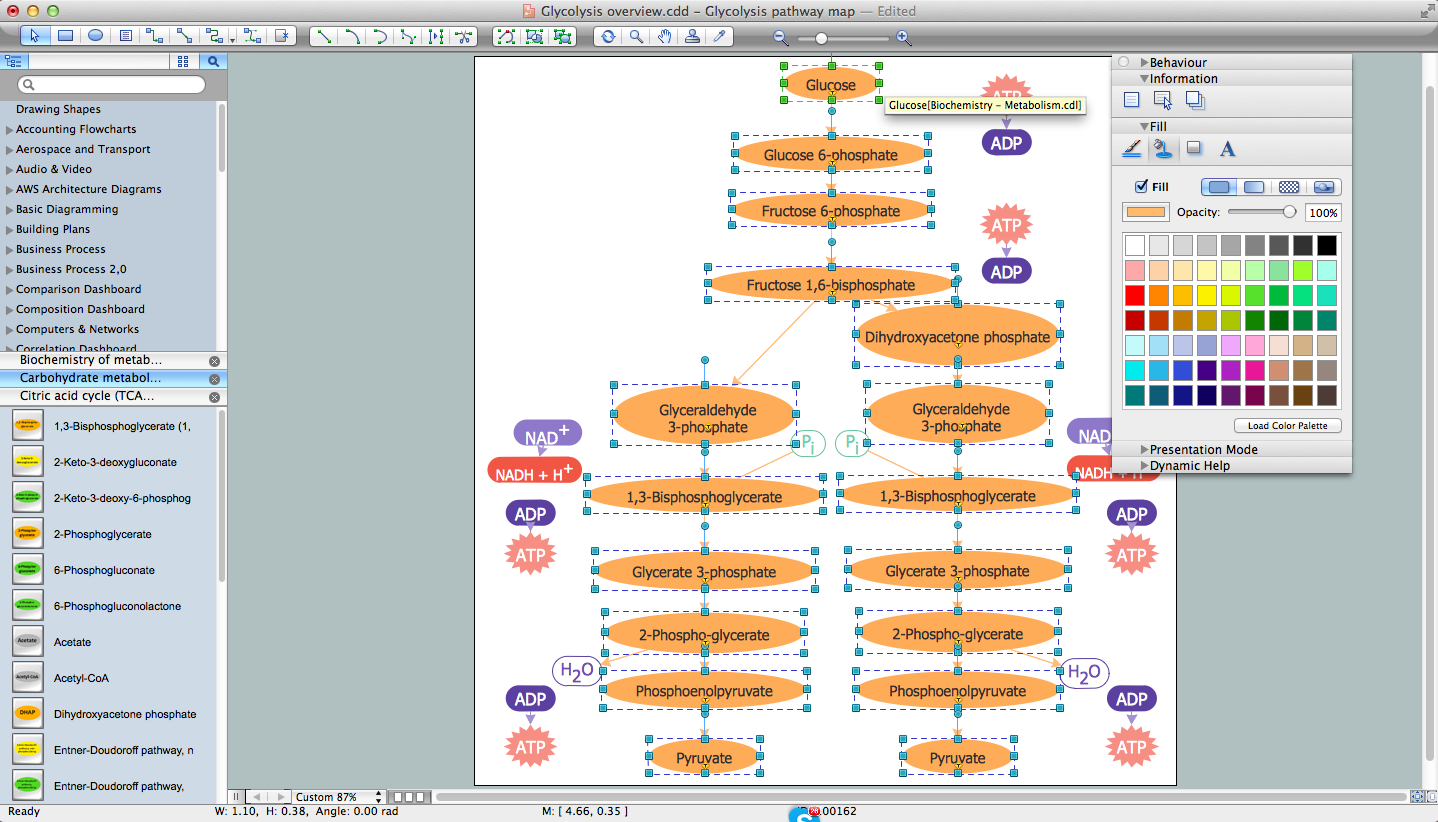
The vector clipart library Access and security contains 17 images of access control and security system equipment.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
The vector stencils library "Access and security" contains 17 clipart images of access control and security system equipment which you can easy use in your diagrams and illustrations.
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
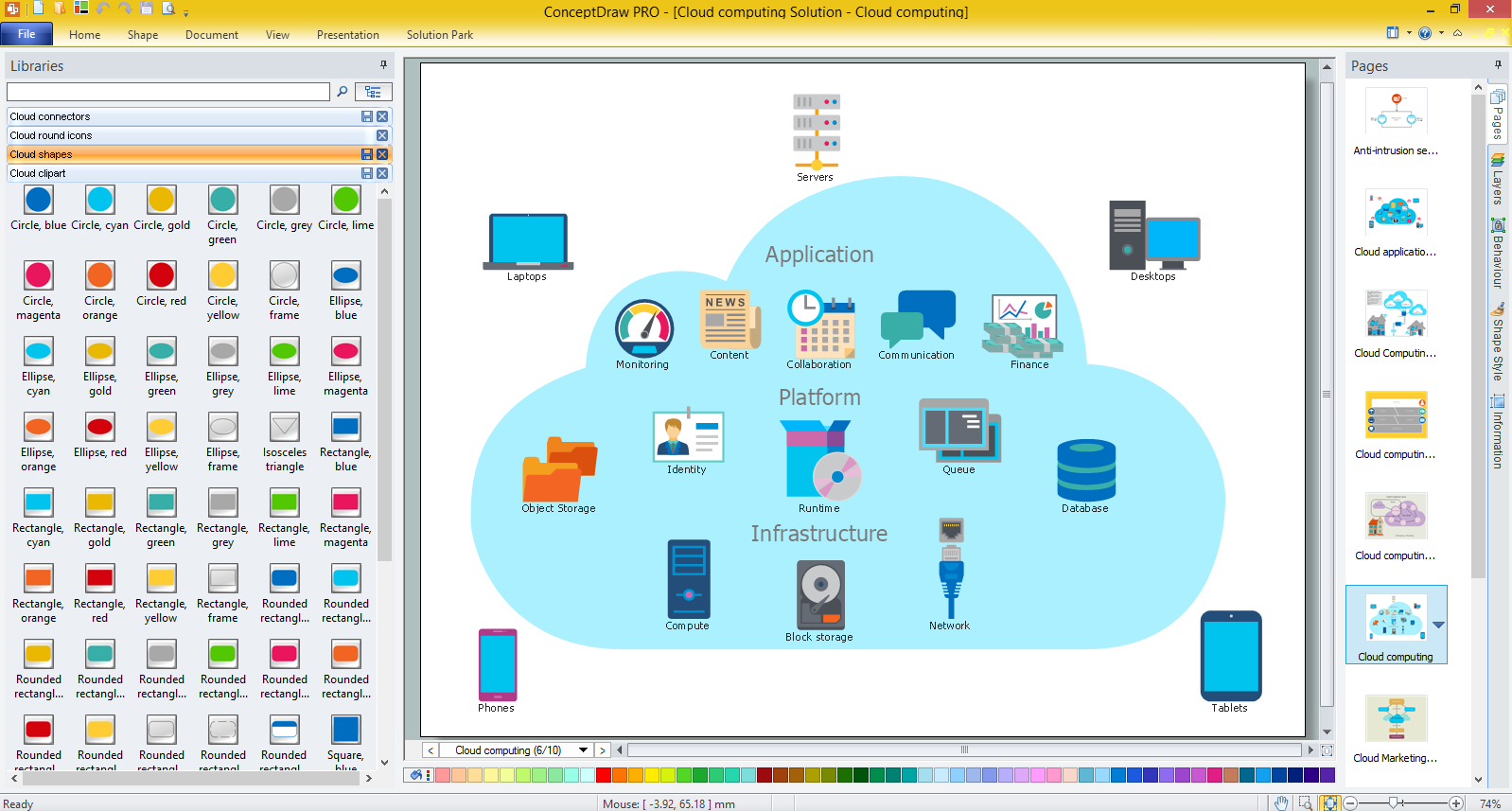
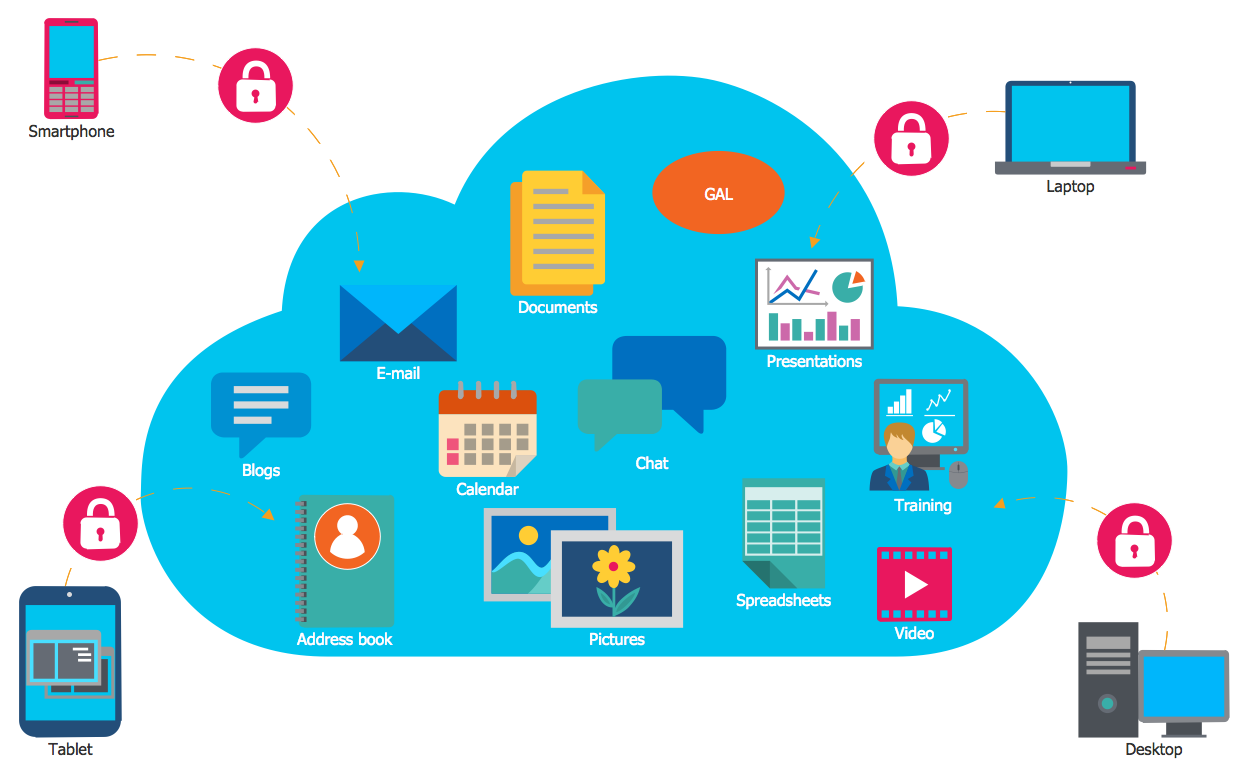
This vector stencils library contains 195 cloud computing icons.
Use it to design cloud computing infographic and diagrams with ConceptDraw PRO software.
"Cloud computing, also on-demand computing, is a kind of Internet-based computing that provides shared processing resources and data to computers and other devices on demand. It is a model for enabling ubiquitous, on-demand access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications and services), which can be rapidly provisioned and released with minimal management effort. Cloud computing and storage solutions provide users and enterprises with various capabilities to store and process their data in third-party data centers.
Cloud computing has become a highly demanded service or utility due to the advantages of high computing power, cheap cost of services, high performance, scalability, accessibility as well as availability." [Cloud computing. Wikipedia]
The vector stencils library "Cloud clipart" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design cloud computing infographic and diagrams with ConceptDraw PRO software.
"Cloud computing, also on-demand computing, is a kind of Internet-based computing that provides shared processing resources and data to computers and other devices on demand. It is a model for enabling ubiquitous, on-demand access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications and services), which can be rapidly provisioned and released with minimal management effort. Cloud computing and storage solutions provide users and enterprises with various capabilities to store and process their data in third-party data centers.
Cloud computing has become a highly demanded service or utility due to the advantages of high computing power, cheap cost of services, high performance, scalability, accessibility as well as availability." [Cloud computing. Wikipedia]
The vector stencils library "Cloud clipart" is included in the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity clipart" contains 197 computer security icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
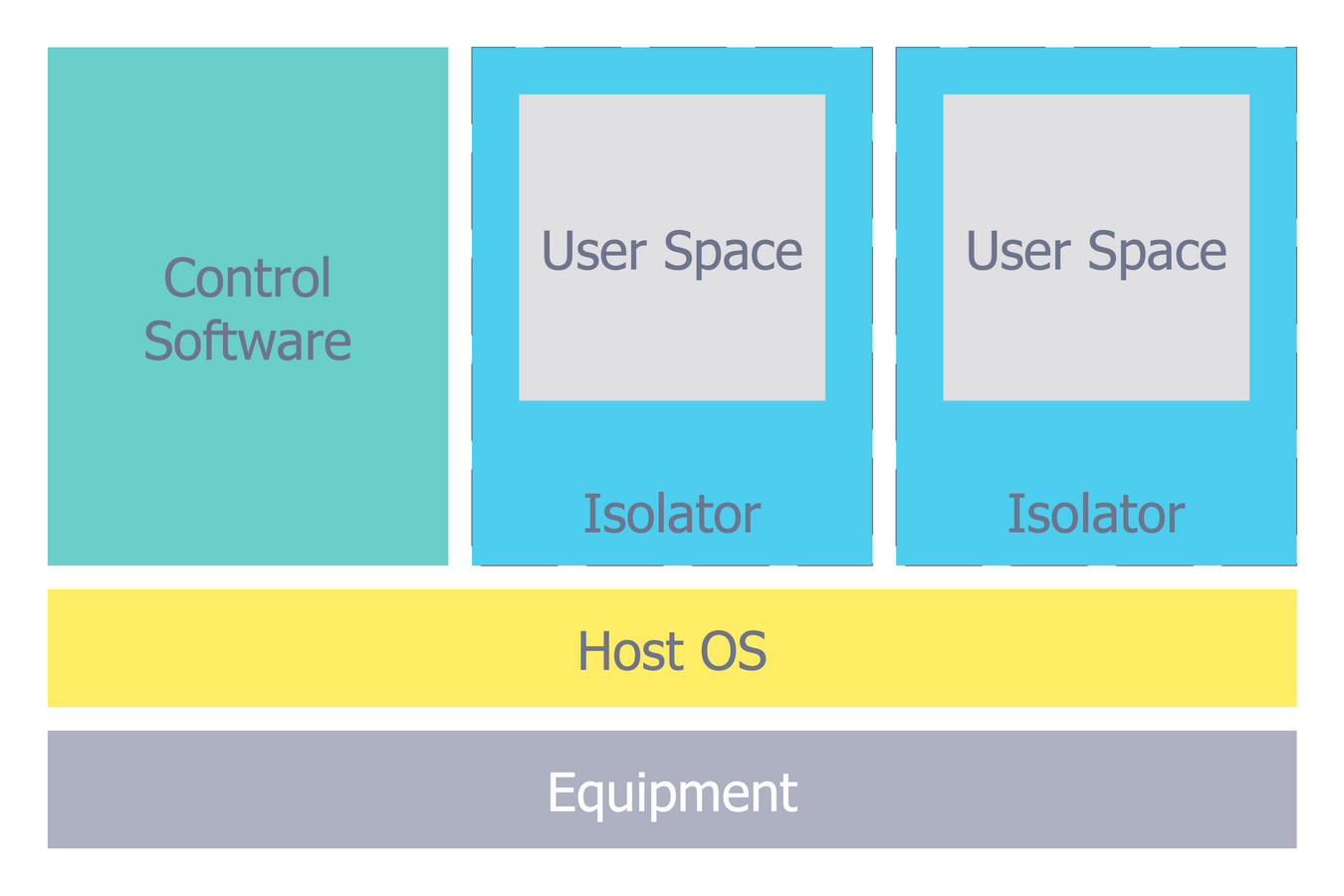
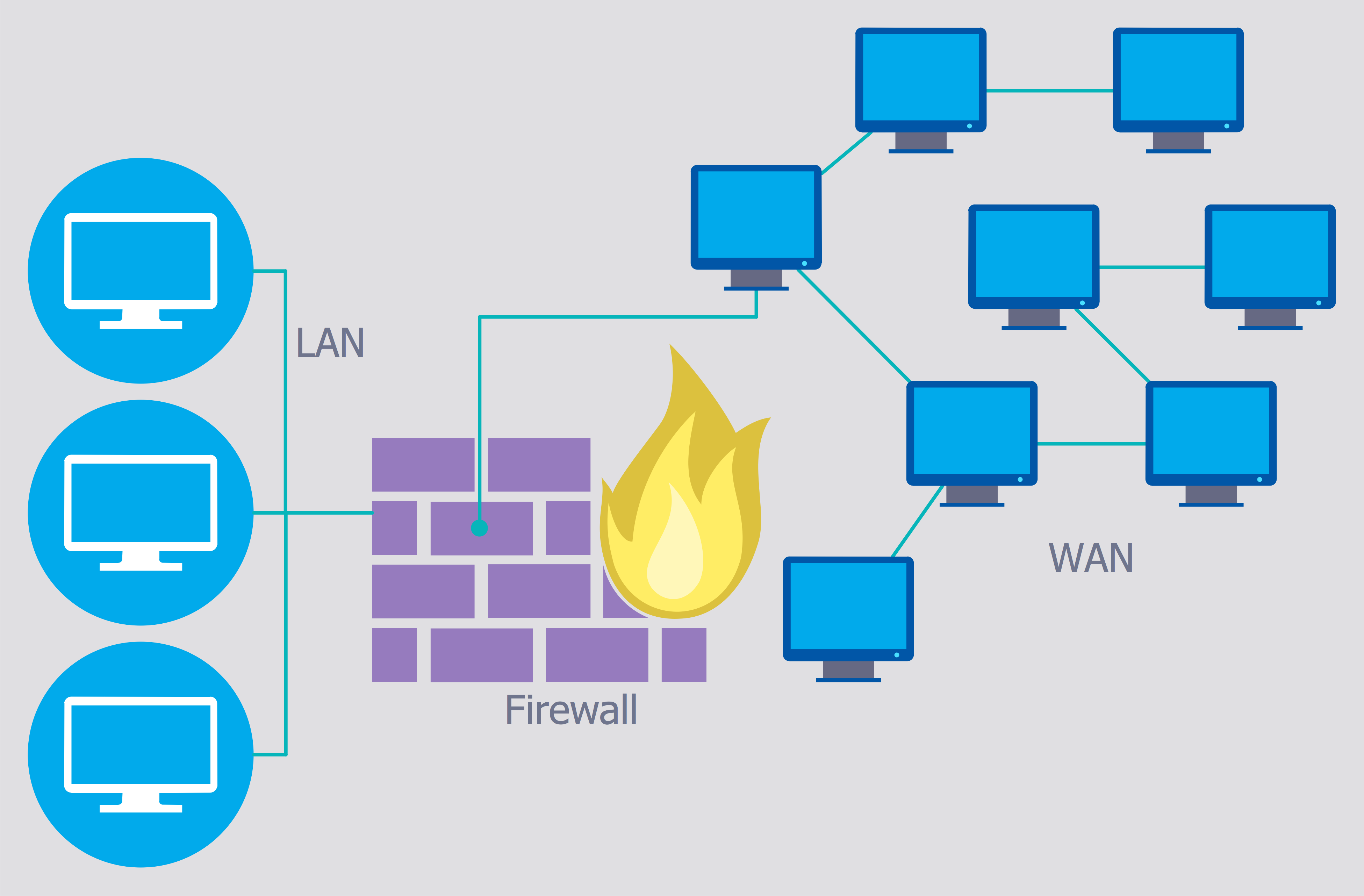
Network Security Architecture Diagram
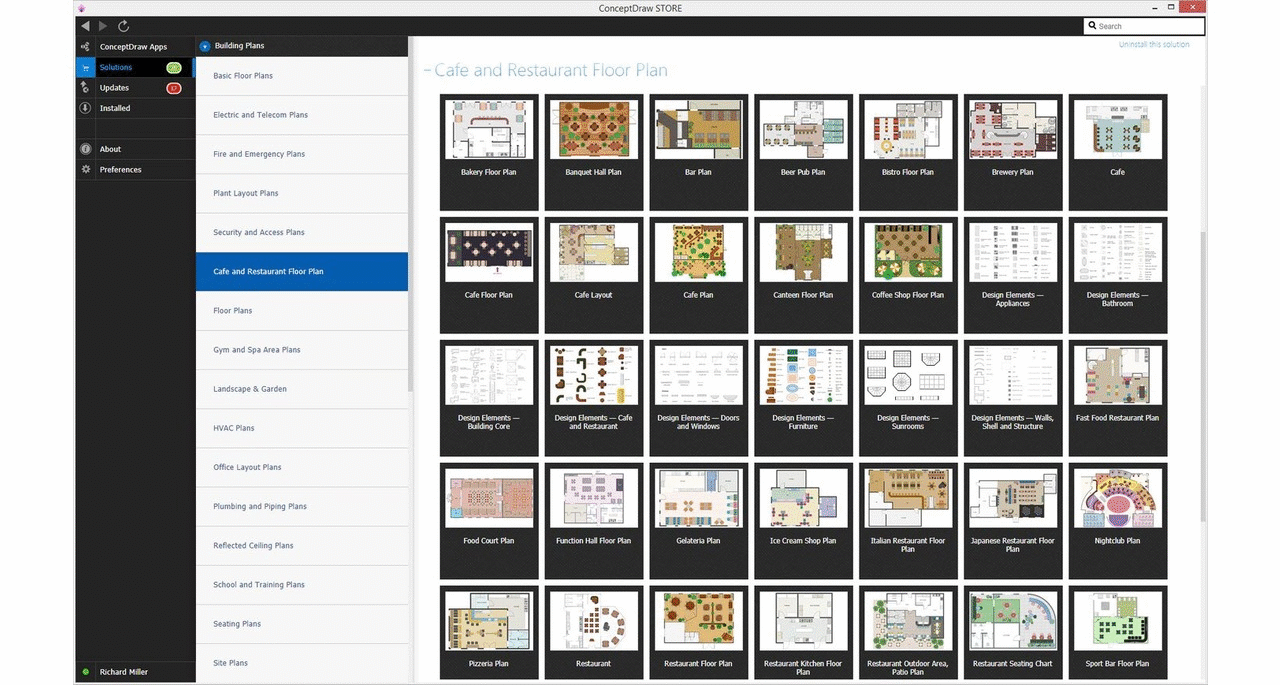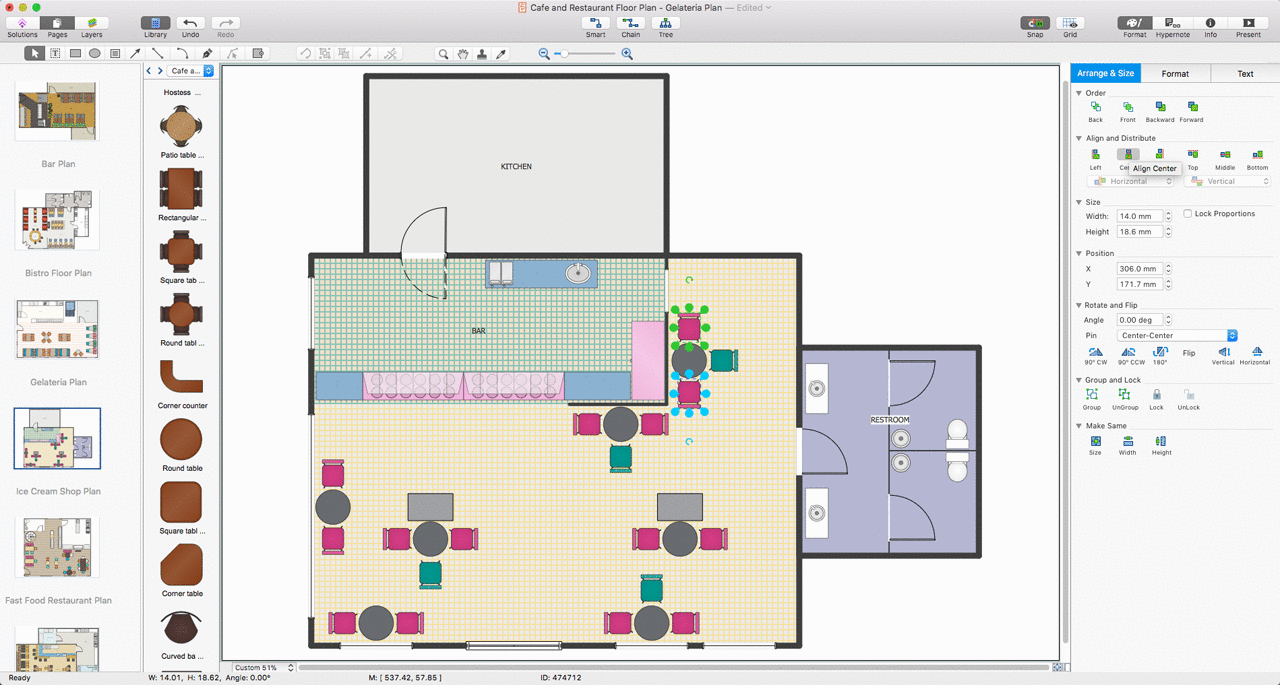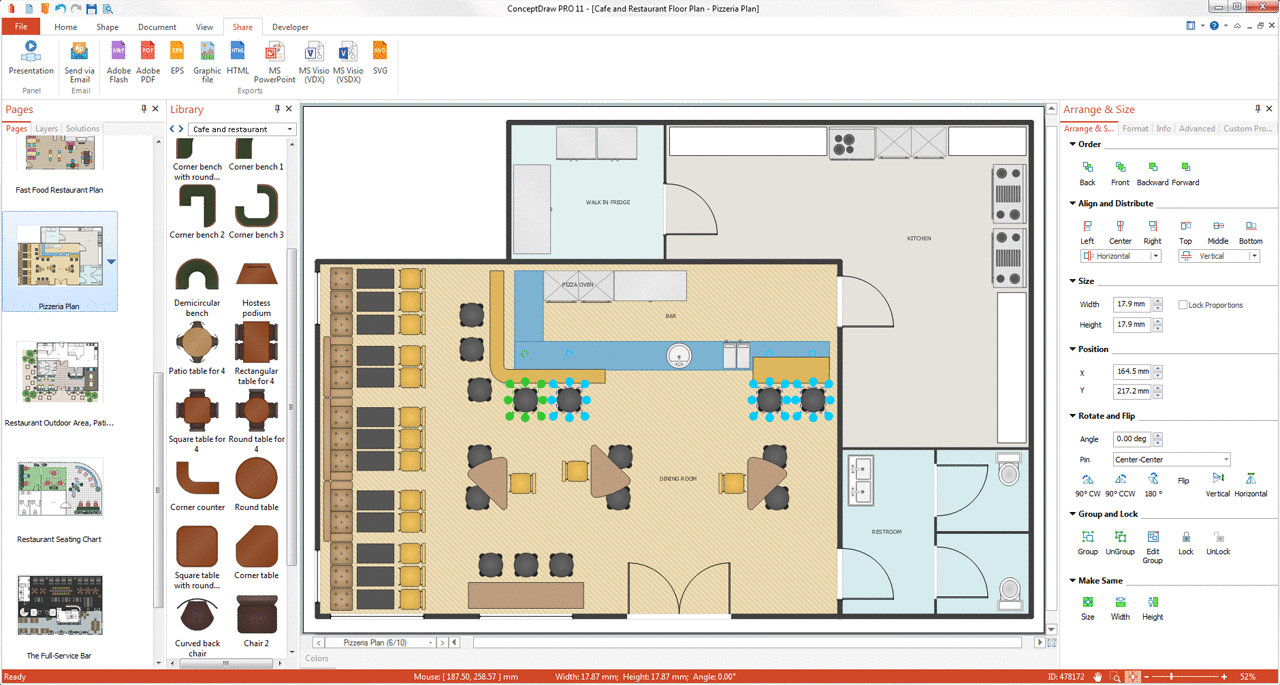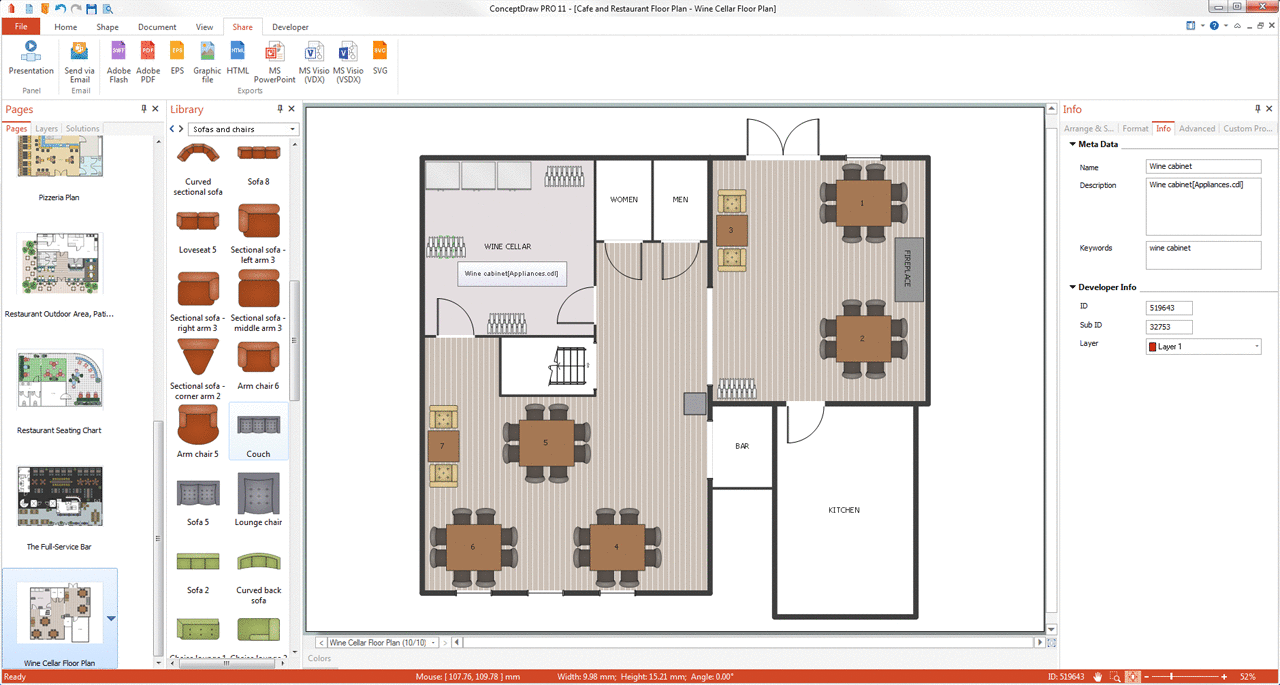
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Restaurant Floor Plans Software
In order to plan the way your future restaurant will look like, including all the furniture, walls, windows, doors, and other elements of interior, you need a ConceptDraw software which can be useful and helpful in creating such kind of plan.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Biology Drawing Software
Biology is incredibly interesting and useful natural science which studies all living things on the earth (people, animals, plants), structure, functions, interactions, evolution of living organisms. Biologists of the whole world use actively illustrations and drawings in your science and education activity. To facilitate their task of biology drawing, ConceptDraw DIAGRAM diagramming and vector drawing software was extended with Biology solution from the Science and Education area. Now, ConceptDraw DIAGRAM is a powerful biology drawing software.Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.How to Build Cloud Computing Diagram Principal Cloud Manufacturing
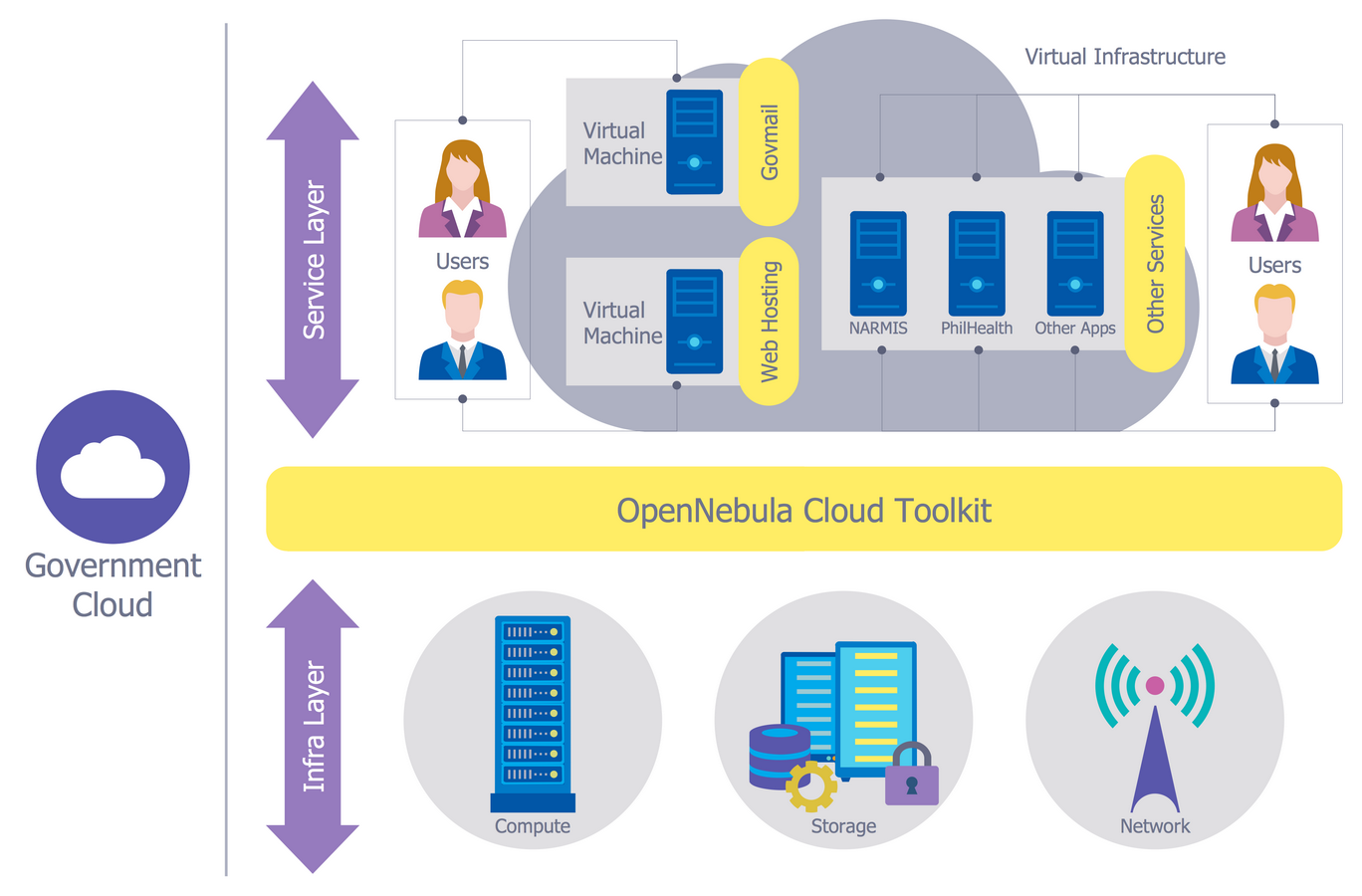
The term “cloud” is very popular and widely used now, it is a server, data processing centre, or a network which lets to store the data and software, provides access to them, allows to run applications without installation and gives the possibility to process data hosted remotely via the Internet connection.For documenting the Cloud Computing Architecture with a goal to facilitate the communication between stakeholders are successfully used the Cloud Computing Architecture diagrams. It is convenient and easy to draw various Cloud Computing Architecture diagrams in ConceptDraw DIAGRAM software with help of tools of the Cloud Computing Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
What is Cloud Computing
What is Cloud Computing? The Cloud computing is a widely used and highly demanded utility in the modern world thanks to its high computing power, performance, scalability and accessibility, and at the same time low cost of services. The ConceptDraw DIAGRAM diagramming and vector drawing software provides an easy and effective Cloud Computing Diagrams solution from the Computers and Network area of ConceptDraw Solution Park for making professional looking Cloud Computing and Cloud Computing Architecture Diagrams.CCTV Network Diagram Software
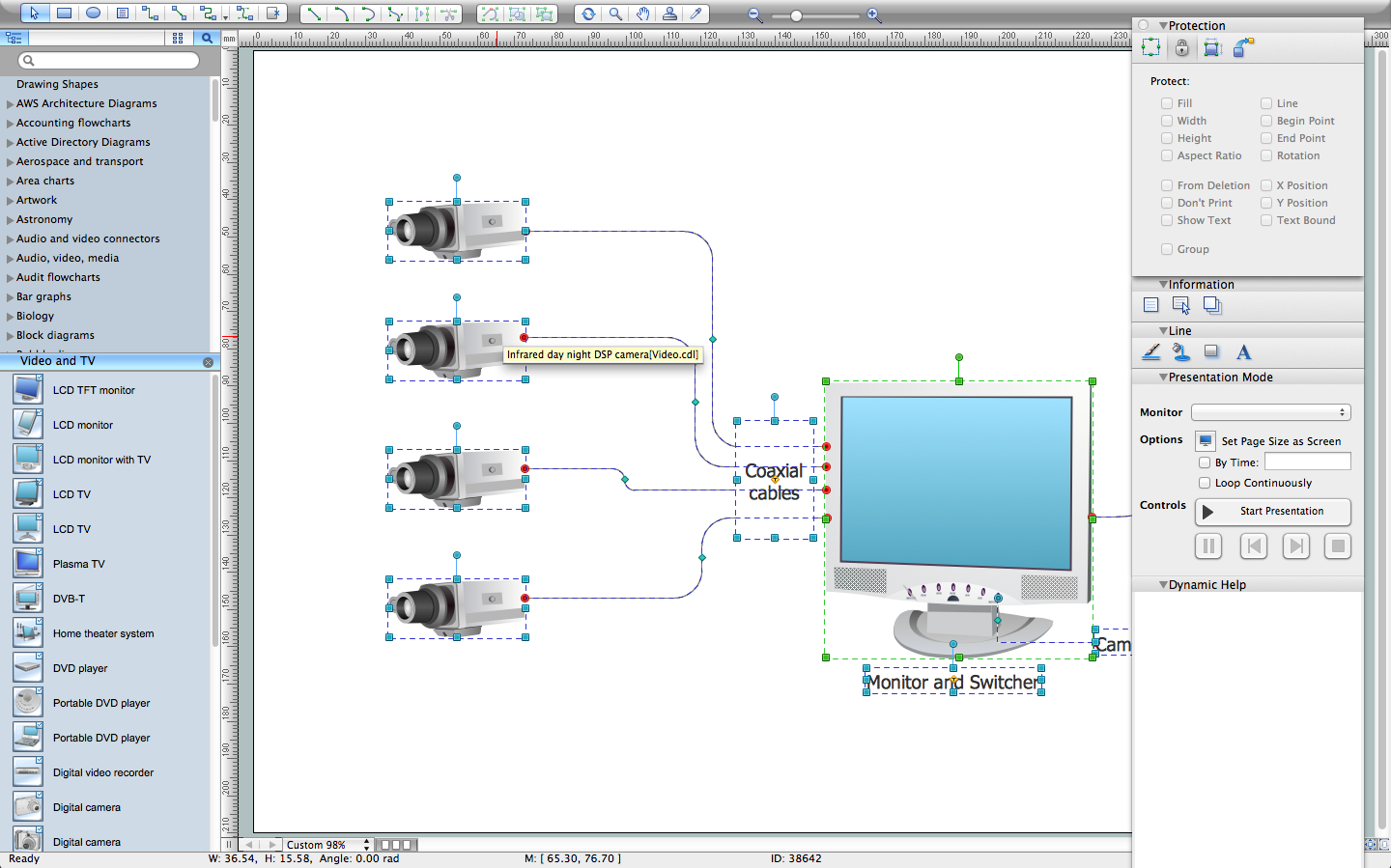
The CCTV is the process that carried out using the video cameras for transmitting the signal to the specific location, on the limited set of monitors. We are talking about the video cameras that are used for monitoring on such guarded objects as airports, banks, stores, military objects, etc. CCTV equipment is also used in the industrial installations, for surveillance in the public places, for recording the video on the digital video recorders.Cloud Computing
The Cloud Computing is the use of the software and hardware that includes the great number of computers connected over the communication network such as the Internet. The Cloud name comes from the usage the cloud symbol on the system diagrams as the abstraction for the complex network infrastructure. This term is used as a marketing metaphor for the Internet.This example was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park and shows the Cloud Computing.
 Presentation Clipart
Presentation Clipart
Presentation design elements solution extends ConceptDraw DIAGRAM software with slide samples, templates and vector stencils libraries with design elements of presentation symbols, arrows, callouts, backgrounds, borders and frames, title blocks.
Secure Wireless Network
Use the ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.- Access and security - Vector stencils library | Holiday | Safety and ...
- Safety and Security | Design elements - Access and security ...
- Truck vehicle clipart | Road Transport - Design Elements ...
- Project management - Design Elements | Presentation Clipart ...
- Design elements - Fire safety equipment | Presentation Clipart ...
- Aerospace - Design Elements | Design elements - Access and ...
- How to Draw a Security and Access Floor Plan | Physical Security ...
- Safety and Security | Office - Design Elements | Design elements ...
- Access and security - Vector stencils library | Design elements ...
- Safety and Security | Security and Access Plans | ConceptDraw ...
- Network Security Diagrams | Safety and Security | Security and ...
- Design elements - Alarm and access control | Cloud clipart - Vector ...
- Security and Access Plans | Gantt chart examples | How to Create a ...
- Network hardware - Vector stencils library | Presentation Clipart ...
- Security Network Clipart Png
- Internet symbols - Vector stencils library | Access and security ...
- Computer Hardware And Software Cliparts
- Design elements - Fire safety equipment | Safety and Security | Fire ...
- CCTV Network Diagram Software | CCTV Network Example | CCTV ...
- Gym Equipment Clipart
- ERD | Entity Relationship Diagrams, ERD Software for Mac and Win
- Flowchart | Basic Flowchart Symbols and Meaning
- Flowchart | Flowchart Design - Symbols, Shapes, Stencils and Icons
- Flowchart | Flow Chart Symbols
- Electrical | Electrical Drawing - Wiring and Circuits Schematics
- Flowchart | Common Flowchart Symbols
- Flowchart | Common Flowchart Symbols






















-cloud-clipart---vector-stencils-library.png--diagram-flowchart-example.png)
-cloud-clipart---vector-stencils-library.png--diagram-flowchart-example.png)





































































-cloud-clipart---vector-stencils-library.png--diagram-flowchart-example.png)










-cloud-clipart---vector-stencils-library.png--diagram-flowchart-example.png)
-cloud-clipart---vector-stencils-library.png--diagram-flowchart-example.png)