Network Security Devices
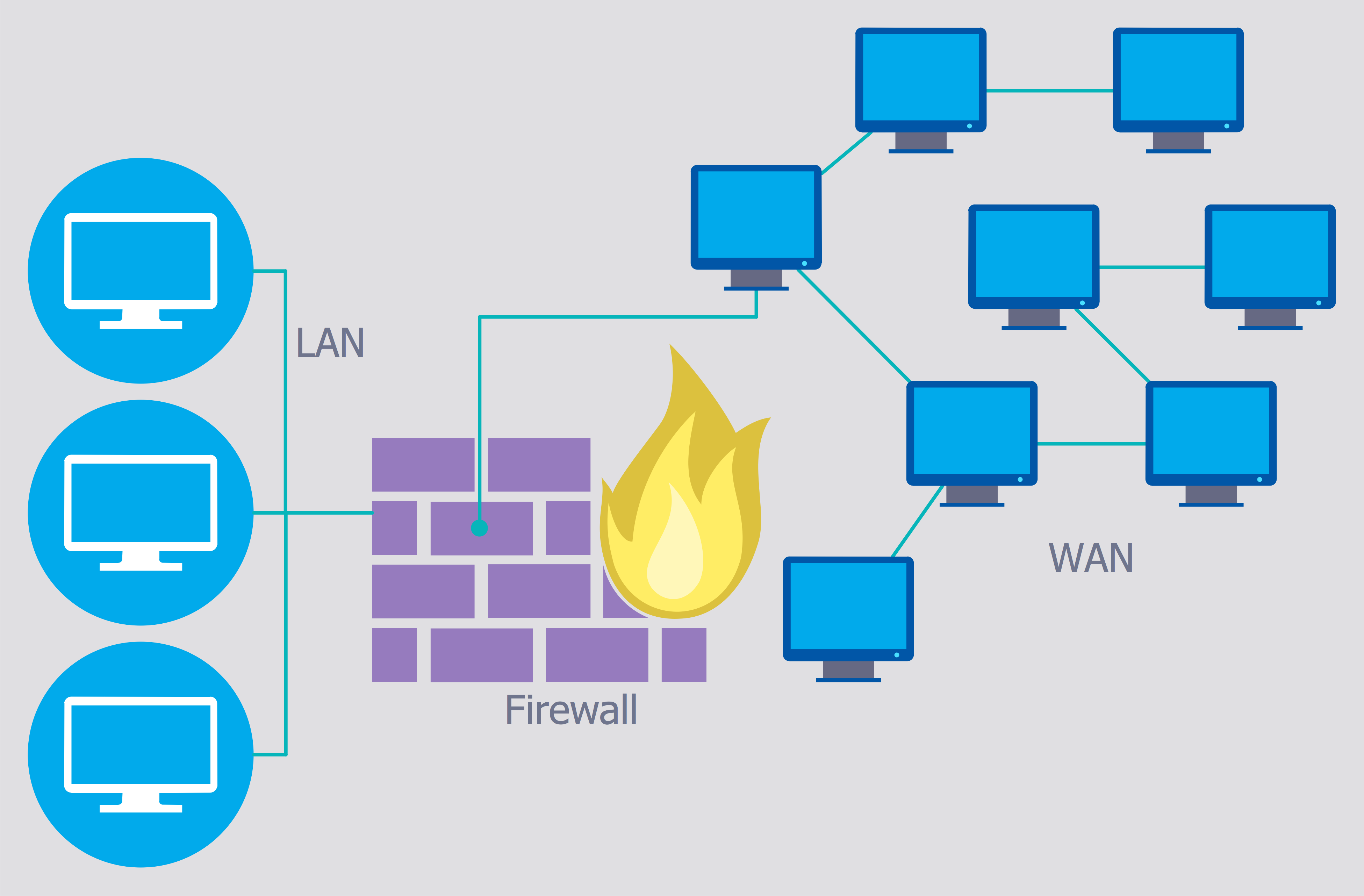
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Secure Wireless Network
Use the ConceptDraw PRO diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Cyber Security Degrees
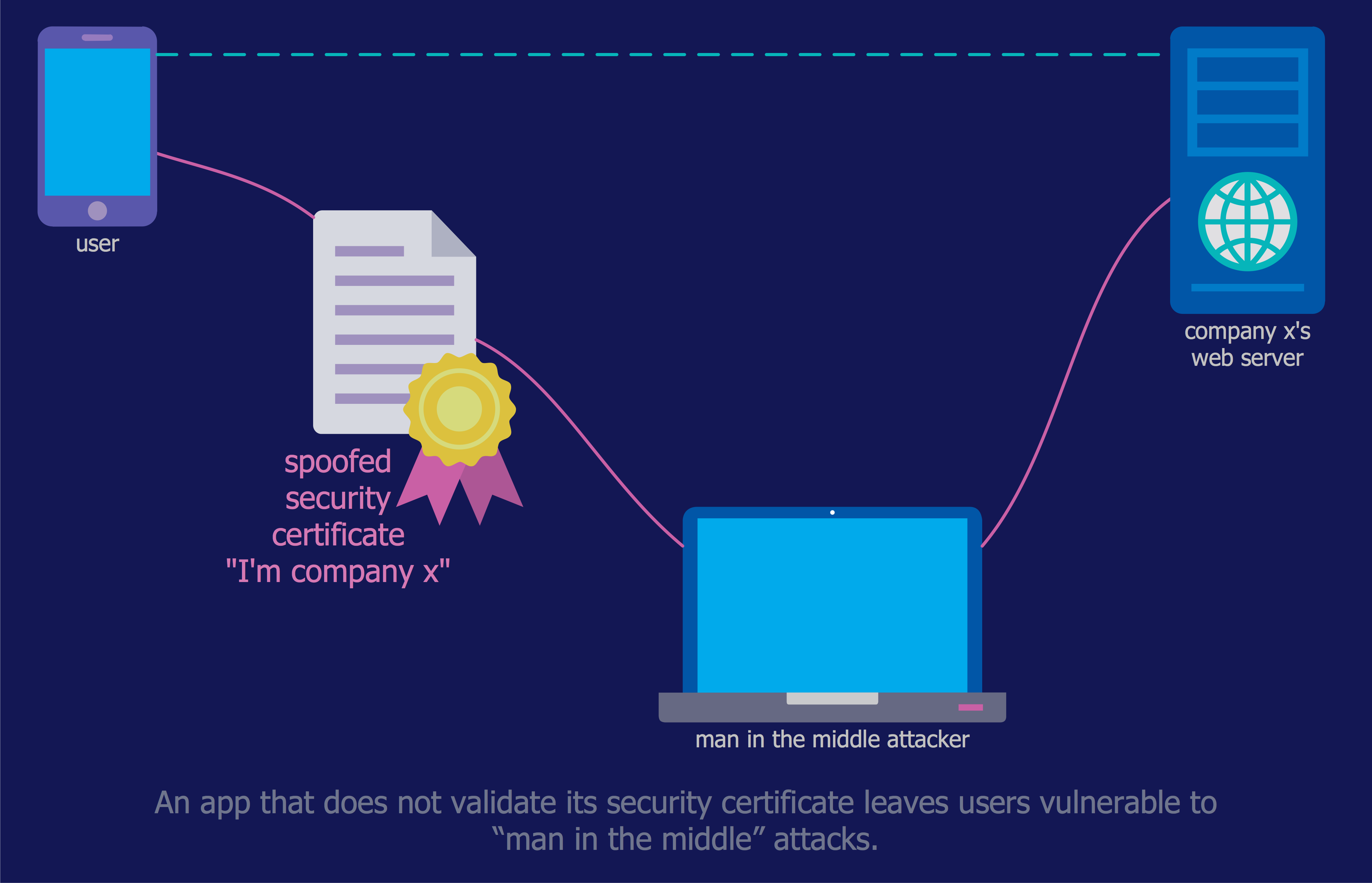
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.This example was designed on the base of the cybersecurity infographic from the website gov.uk. (Open Government Licence v3.0. nationalarchives.gov.uk/ doc/ open-government-licence/ version/ 3/ )
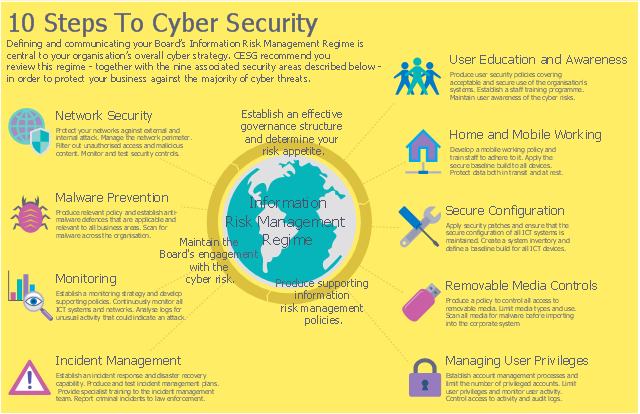
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Used Solutions
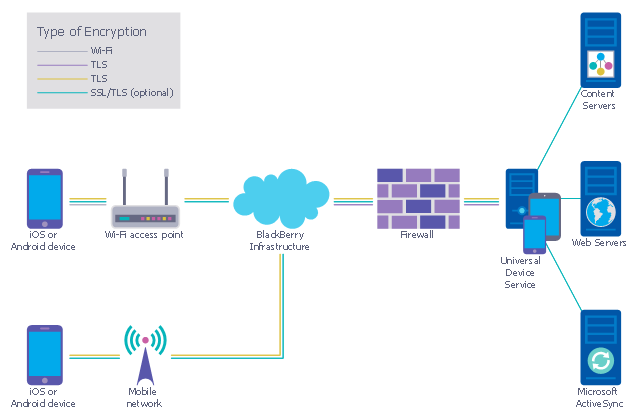
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
 Seven Management and Planning Tools
Seven Management and Planning Tools
Seven Management and Planning Tools solution extends ConceptDraw PRO and ConceptDraw MINDMAP with features, templates, samples and libraries of vector stencils for drawing management mind maps and diagrams.
 Management Area
Management Area
The solutions from Management area of ConceptDraw Solution Park collect templates, samples and libraries of vector stencils for drawing the management diagrams and mind maps.
 Stakeholder Onion Diagrams
Stakeholder Onion Diagrams
The Stakeholder Onion Diagram is often used as a way to view the relationships of stakeholders to a project goal. A basic Onion Diagram contains a rich information. It shows significance of stakeholders that will have has influence to the success achieve
 Concept Maps
Concept Maps
The technique of concept mapping was developed as a constructive way of representing knowledge in science and increasing the meaningfulness of learning. Now, the creation of a concept map is extremely helpful when used in education as learning and teaching techniques that assist memorization. Concept maps are also used for idea generation in brainstorming sessions, and for detailing the structure of complex ideas.
- Cyber Security Degrees | IT Security Solutions | Network Security ...
- Network Security Devices | Cyber Security Degrees | ConceptDraw ...
- | Cyber Security Degrees | | Computer Security Risk
- Cyber Security Degrees | IT Security Solutions | | Cyber Security Risks
- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- Recommended network architecture for BlackBerry SWS | Network ...
- Business Productivity Area | Management pictograms - Vector ...
- Security Plans | Physical Security Plan | Security and Access Plans ...
- Cisco Switches and Hubs. Cisco icons, shapes, stencils and symbols
- Cisco Multimedia, Voice, Phone. Cisco icons, shapes, stencils and ...
- Security and Access Plans | How to Create a CCTV Diagram in ...
- Risk Management Tools Examples
- Cisco Switches and Hubs. Cisco icons, shapes, stencils and symbols
- Network Printer | Physical LAN topology diagram | Home wireless ...
- 4 Level pyramid model diagram - Information systems types | 5 Level ...
- CCTV Network Example | CCTV Network Diagram Software ...
- Value Stream Mapping | Risk management - Concept map ...
- Memory Assistant | Professional & Powerful Mind Mapping Software ...
- Network Diagramming Software for Design Cisco Network Diagrams ...