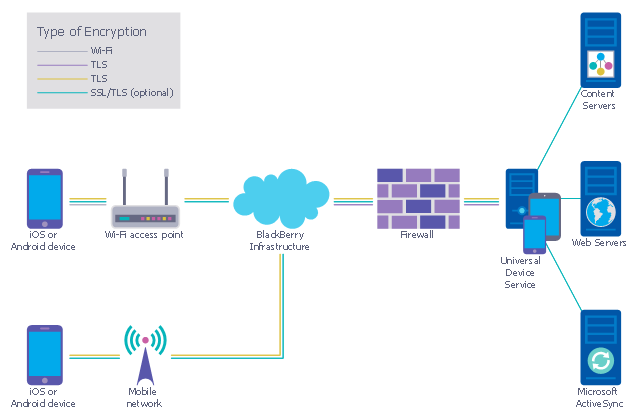
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
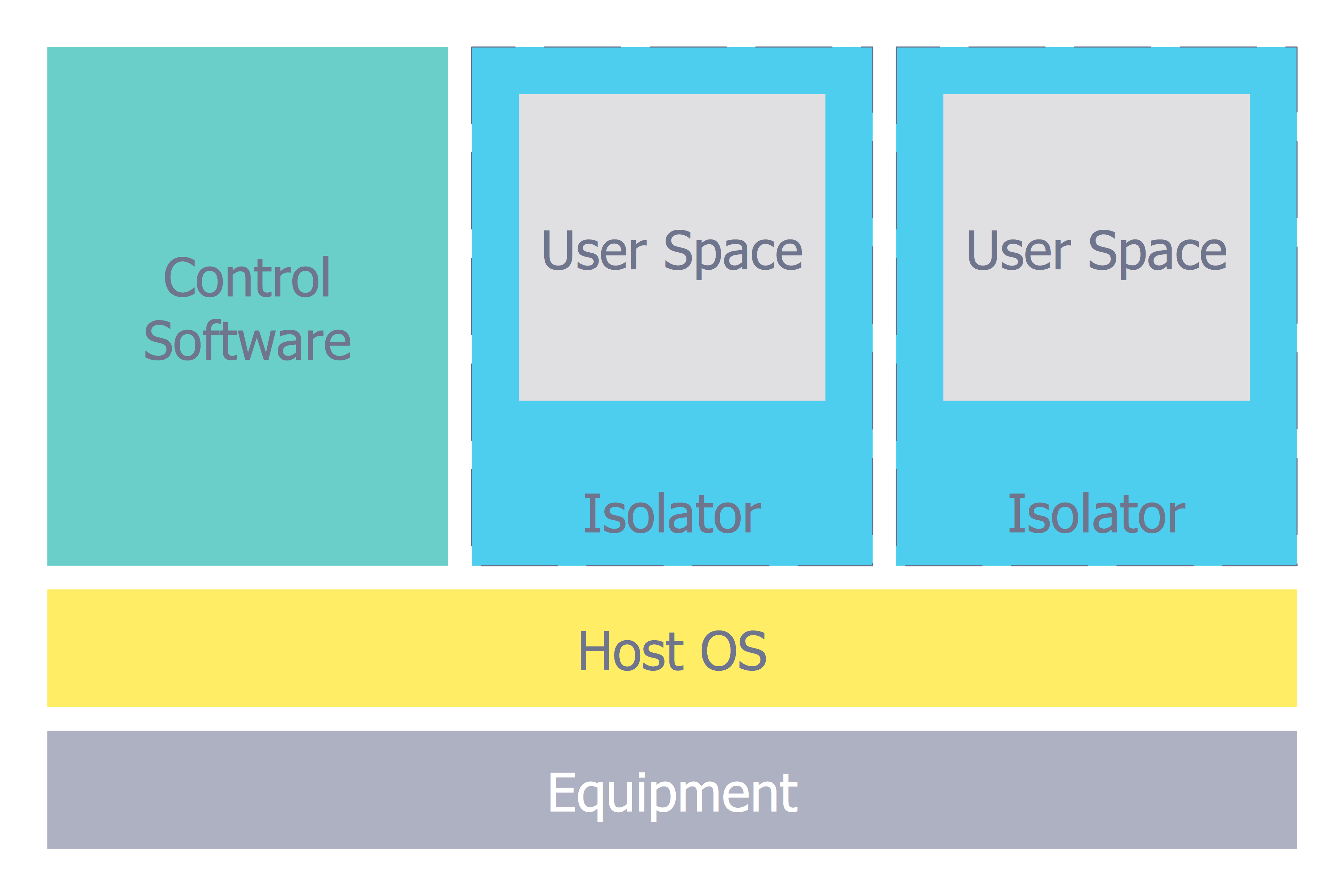
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Create Fishbone Diagrams
Common uses of the Fishbone (Ishikawa) diagrams are product design and quality defect prevention. They are effectively used to identify potential factors causing an overall effect for making possibility to solve a problem. To create Fishbone Diagrams, Cause-and-Effect Diagrams, Ishikawa Diagrams, we recommend to use a ConceptDraw PRO software enhanced with Fishbone Diagrams solution from the Management area of ConceptDraw Solution Park.What's the best ERD tool for the Mac?
What's the best ERD tool for the Mac? ConceptDraw PRO on Mac OS X supplied with Entity-Relationship Diagram (ERD) Solution from the Software Development Area for ConceptDraw Solution Park is the best ERD tool! This solution offers for ConceptDraw users so powerful drawing tools, libraries with numerous ERD objects, which will help design ER diagrams of any complexity and any design you want.How to Draw Workflow Diagram
To draw workflow diagram you should find a perfect software first. We recommend using ConceptDraw PRO software contains all features you may need to draw diagrams faster. ConceptDraw PRO software extended with the Workflow Diagrams solution gives you everything you need to draw workflow diagram.Network Security Diagram
ConceptDraw PRO diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model."Business process improvement (BPI) is a systematic approach to help an organization optimize its underlying processes to achieve more efficient results. ...
An organization is only as good as its processes. To be able to make the necessary changes in an organization, one needs to understand the key processes of the company. Rummler and Brache suggested a model for running a Process Improvement and Management project (PI&M), containing the following steps:
1. Identify the process to be improved (based on a critical business issue): The identification of key processes can be a formal or informal exercise. The management team might select processes by applying a set of criteria derived from strategic and tactical priorities, or process selection is based on obvious performance gaps. It is important is to select the process(es) which have the greatest impact on a competitive advantage or customer requirement.
2. Develop the objective(s) for the project based on the requirements of the process: The focus might be on quality improvement, productivity, cost, customer service or cycle time. The goal is however always the same; to get the key process under control.
3. Select the members of the cross-functional team: A horizontal (cross-functional) analysis is carried out by a team composed of representatives of all functions involved in the process. While a consultant or in-house staff person can do the job, the quality of the analysis and the commitment to change is far greater with a cross-functional team.
4. Document the current process by creating a flowchart or "organization map": Describe the process regarding the Organizational level, the Process level and the Job/ Performer level according to Rummler. Develop a cross-functional process map for the process.
5. Identify "disconnects" in the process: “Disconnections” are everything that inhibit the efficiency and effectiveness of the process. The identification should be categorized into the three levels: The Organizational level, the Process level and the Job/ Performer level.
6. Recommend changes (organizational, in the process or in its execution): Categorize and prioritize the main problems and possibilities, evaluate alternative solutions. Develop a cross-functional process map for the recommended process.
7. Establish process and sub-process measures: The process measures should reflect the objectives of the project.
8. Implement the improvements." [Business process improvement. Wikipedia]
The opportunity flow chart example "Replacing engine oil" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cross-Functional Flowcharts solution from the Business Processes area of ConceptDraw Solution Park.
An organization is only as good as its processes. To be able to make the necessary changes in an organization, one needs to understand the key processes of the company. Rummler and Brache suggested a model for running a Process Improvement and Management project (PI&M), containing the following steps:
1. Identify the process to be improved (based on a critical business issue): The identification of key processes can be a formal or informal exercise. The management team might select processes by applying a set of criteria derived from strategic and tactical priorities, or process selection is based on obvious performance gaps. It is important is to select the process(es) which have the greatest impact on a competitive advantage or customer requirement.
2. Develop the objective(s) for the project based on the requirements of the process: The focus might be on quality improvement, productivity, cost, customer service or cycle time. The goal is however always the same; to get the key process under control.
3. Select the members of the cross-functional team: A horizontal (cross-functional) analysis is carried out by a team composed of representatives of all functions involved in the process. While a consultant or in-house staff person can do the job, the quality of the analysis and the commitment to change is far greater with a cross-functional team.
4. Document the current process by creating a flowchart or "organization map": Describe the process regarding the Organizational level, the Process level and the Job/ Performer level according to Rummler. Develop a cross-functional process map for the process.
5. Identify "disconnects" in the process: “Disconnections” are everything that inhibit the efficiency and effectiveness of the process. The identification should be categorized into the three levels: The Organizational level, the Process level and the Job/ Performer level.
6. Recommend changes (organizational, in the process or in its execution): Categorize and prioritize the main problems and possibilities, evaluate alternative solutions. Develop a cross-functional process map for the recommended process.
7. Establish process and sub-process measures: The process measures should reflect the objectives of the project.
8. Implement the improvements." [Business process improvement. Wikipedia]
The opportunity flow chart example "Replacing engine oil" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cross-Functional Flowcharts solution from the Business Processes area of ConceptDraw Solution Park.
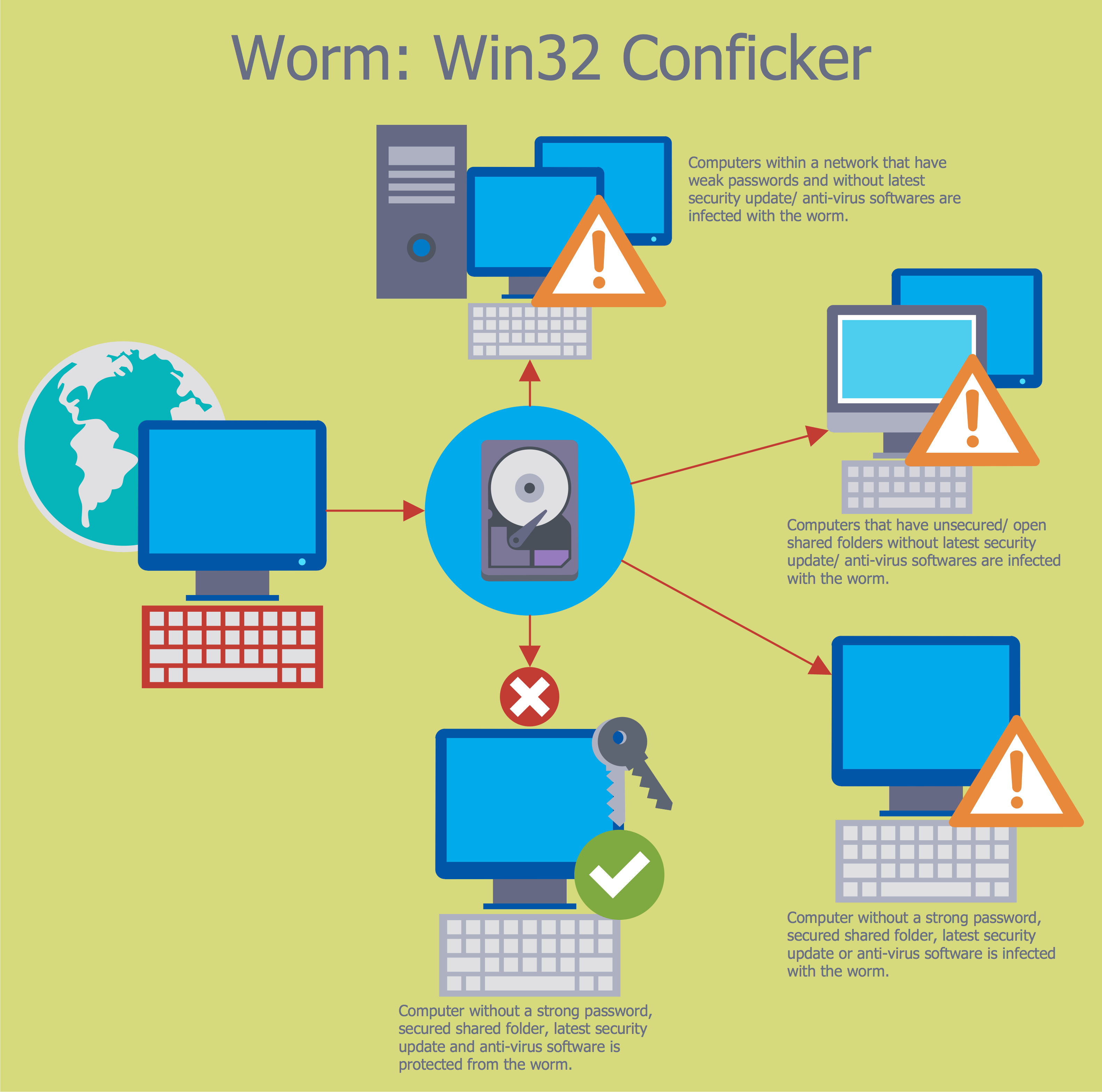
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.HelpDesk
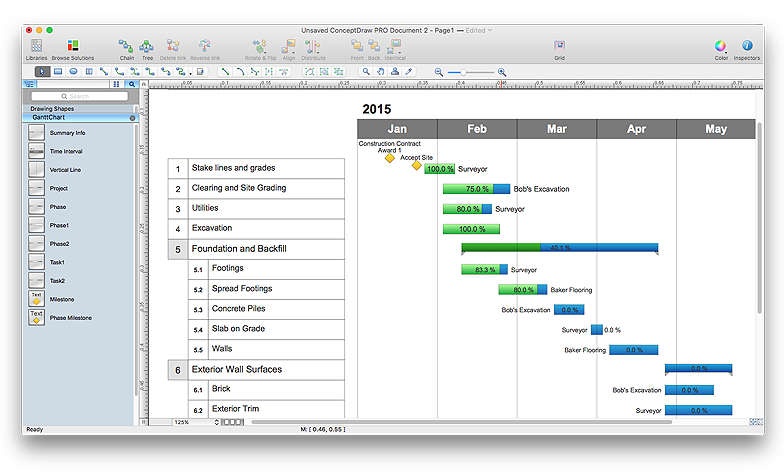
How to Draw a Gantt Chart Using ConceptDraw PRO
A Gantt chart is intended to provide a visualization of a project schedule. It is developed to help planning, coordinating, and tracking on project tasks implementation. One of the most critical resources for a project implementation is a time resources. Gantt chart - is one of the most convenient and popular way of graphical representation of a project tasks progress in conjunction with the corresponding time consumption. Gantt chart's function is to show project tasks completion in a progress, and to make a project manager sure that project tasks were completed on time. ConceptDraw Office is a clear and easy-to-use tool for project management. It is a very handy visual tool that helps make a project processing clear.HelpDesk
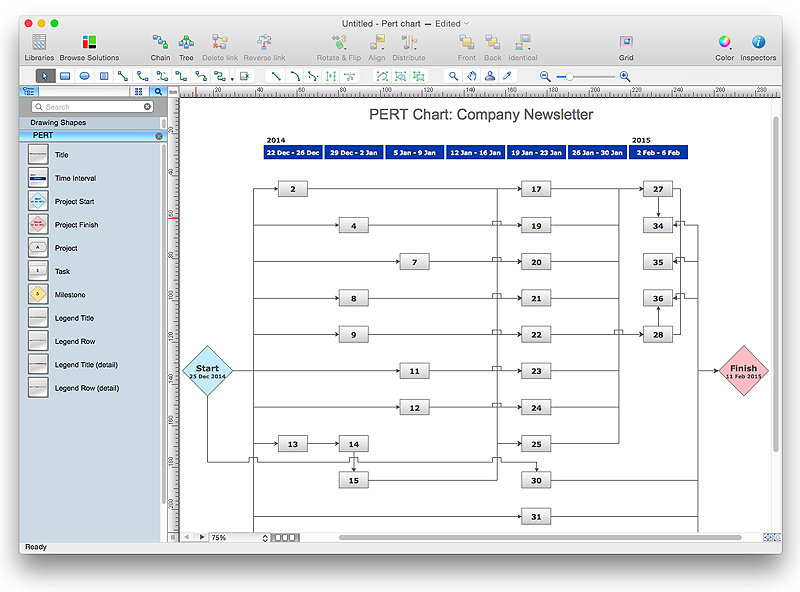
How To Create a PERT Chart
Project Evaluation and Review Technique (PERT) is a method of project tasks evaluation and analysis. PERT - is a method of analyzing the tasks required to complete the project. It includes analysis of the time required to complete each task, as well as the determination of the time required to carry out the whole project. PERT was developed to facilitate the planning of huge and complex projects. PERT is used for very large, complex, and non-standard projects. Technology implies the presence of uncertainty, making it possible to develop a schedule of the project without a precise information on details and time required for all of its components. The most popular part of PERT is a method of the critical path, based on the construction of the network schedule (PERT network diagram). ConceptDraw Office delivers you the best way to create PERT chart for your project using compatibility between ConceptDraw PROJECT and ConceptDraw PRO.HelpDesk
How to Create the New Library in ConceptDraw PRO
Sometimes, when creating a diagram, you need to use a large set of elements from different libraries. If you are using ConceptDraw , in such case, we recommend you to create a new library, which consists of vector library objects from other ConceptDraw libraries. You also can add some custom unique objects into such library. Each object that contains in a new library can be provided with a unique description and keyword list. Thus, the new library and its objects will be indexed to be searched and used in the further diagrams.Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw PRO extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.HelpDesk
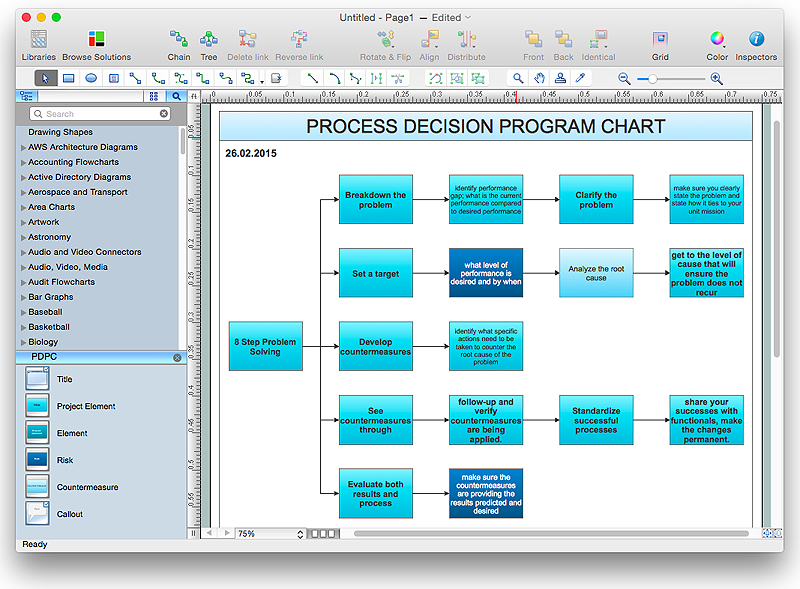
How To Create Risk Diagram (PDPC)
Article on how to identify possible risks when carrying out corrective actions, and define preventive actions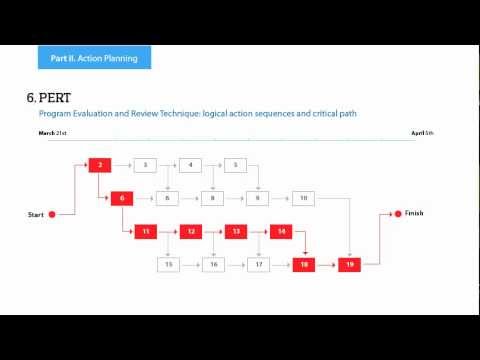
Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw PRO diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.- Recommend And Suggest Strategies They Can Use To Benefit From ...
- Recommend And Suggest Strategies They Can Use To Benefit From ...
- Process Flowchart | Recommend And Suggest Strategies They Can ...
- Plant Layout Plans | Type Of Floor Plan To Recommend For Storing ...
- Process Flowchart | Recommend And Suggest Strategies From ...
- Special Media Might Change Their Relationship And Behavior ...
- Recommended network architecture for BlackBerry SWS | Network ...
- How To Draw Basketball Court Recommend Byfiba
- Cloud Computing Diagrams | Introduction to Cloud Computing ...
- Cloud Computing Architecture Diagrams | Introduction to Cloud ...
- How to Design a Good Workflow | Work Flow Process Chart ...
- Cloud Computing Architecture Diagrams | Active Directory Diagram ...
- Cloud Computing Architecture Diagrams | Network Security ...
- How To use House Electrical Plan Software | Building Drawing ...
- Business Process Optimization | Optimize a Workflow | Business ...
- Opportunity flowchart - Template | Replacing engine oil - Opportunity ...
- Work Flow Process Chart | Create Workflow Diagram | Drawing ...
- Floor Plan | Make Your Own Floor Plans | Rail transport - Design ...
- Service 8 Ps fishbone diagram - Template | Fishbone Diagram | How ...
- Download and Install ConceptDraw Office on Mac | Downloading ...