This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Australia Map
Australia Map
For graphic artists creating accurate maps of Australia. The Australia Map solution - allows designers to map Australia for their needs, offers a collection of scalable graphics representing the political geography of Australia, split into distinct state
This Active Directory network diagram example depicts types of groups and people assignment rules.
Architecture groups in a Windows Active Directory 2003:
(1) The arrow indicates "may be a member of."
(2) Dotted: Functionality limited to Windows 2003 (without the Windows 2000 compatibility).
(3) Red: Setting possible, but not recommended.
It was drawn on the base of Wikimedia Commons file: AD2003.JPG. [commons.wikimedia.org/ wiki/ File:AD2003.JPG]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The Active Directory network diagram example "Tree and Forest (Full Trust)" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Architecture groups in a Windows Active Directory 2003:
(1) The arrow indicates "may be a member of."
(2) Dotted: Functionality limited to Windows 2003 (without the Windows 2000 compatibility).
(3) Red: Setting possible, but not recommended.
It was drawn on the base of Wikimedia Commons file: AD2003.JPG. [commons.wikimedia.org/ wiki/ File:AD2003.JPG]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The Active Directory network diagram example "Tree and Forest (Full Trust)" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Fundraising Pyramid
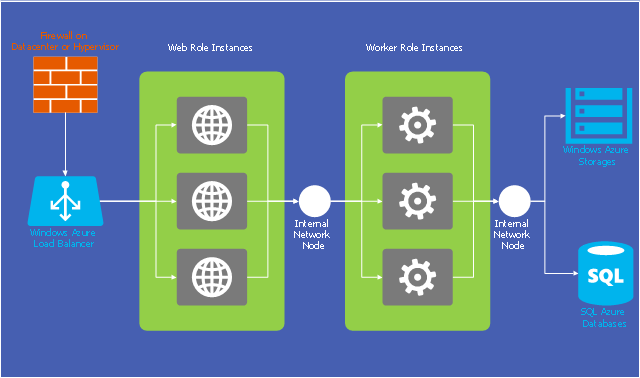
ConceptDraw Pyramid Diagram software allows drawing column charts using predesigned objects or drawing tool.This example of cloud computing system architecture diagram was redesigned from the Wikimedia Commons file: Windows Azure Network and Computes Architecture.png. [commons.wikimedia.org/ wiki/ File:Windows_ Azure_ Network_ and_ Computes_ Architecture.png]
This file is licensed under the Creative Commons Attribution-Share Alike 2.0 license. [creativecommons.org/ licenses/ by-sa/ 2.0/ ]
"Microsoft Azure (formerly Windows Azure before 25 March 2014) is a cloud computing platform and infrastructure, created by Microsoft, for building, deploying and managing applications and services through a global network of Microsoft-managed datacenters. It provides both PaaS and IaaS services and supports many different programming languages, tools and frameworks, including both Microsoft-specific and third-party software and systems." [Microsoft Azure. Wikipedia]
The diagram example "Microsoft Azure network and computes architecture" was created using ConceptDraw PRO diagramming and vector drawing software extended with the Azure Architecture solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 2.0 license. [creativecommons.org/ licenses/ by-sa/ 2.0/ ]
"Microsoft Azure (formerly Windows Azure before 25 March 2014) is a cloud computing platform and infrastructure, created by Microsoft, for building, deploying and managing applications and services through a global network of Microsoft-managed datacenters. It provides both PaaS and IaaS services and supports many different programming languages, tools and frameworks, including both Microsoft-specific and third-party software and systems." [Microsoft Azure. Wikipedia]
The diagram example "Microsoft Azure network and computes architecture" was created using ConceptDraw PRO diagramming and vector drawing software extended with the Azure Architecture solution from the Computer and Networks area of ConceptDraw Solution Park.
Pyramid Diagram
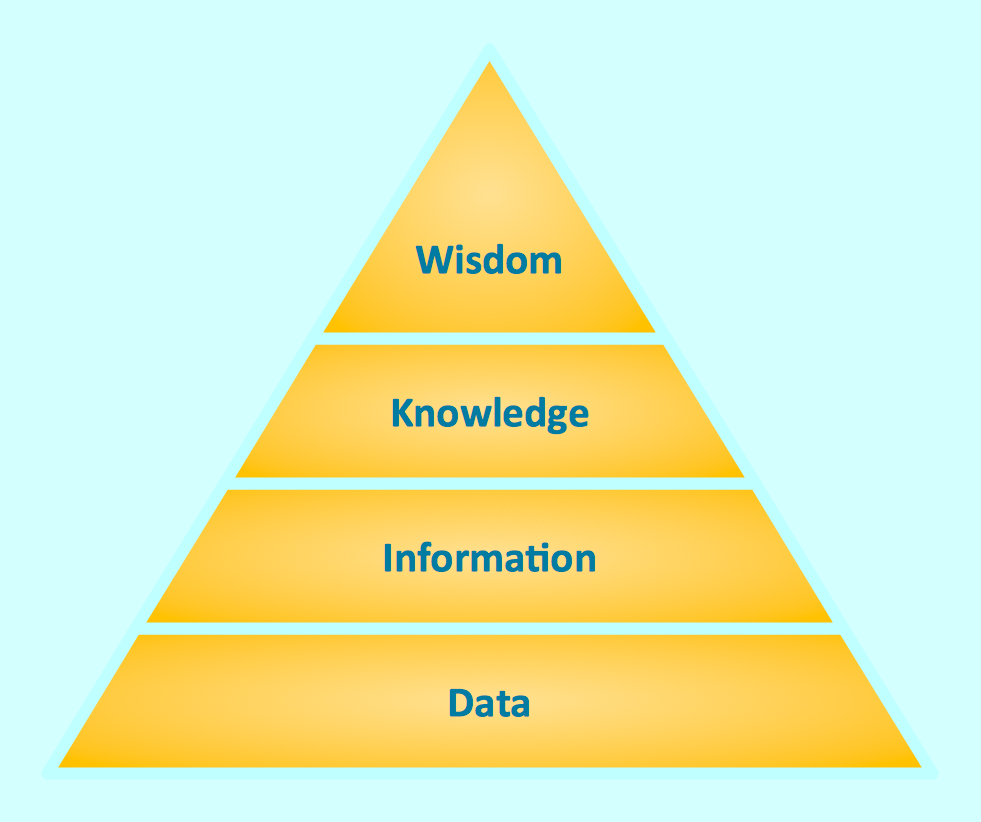
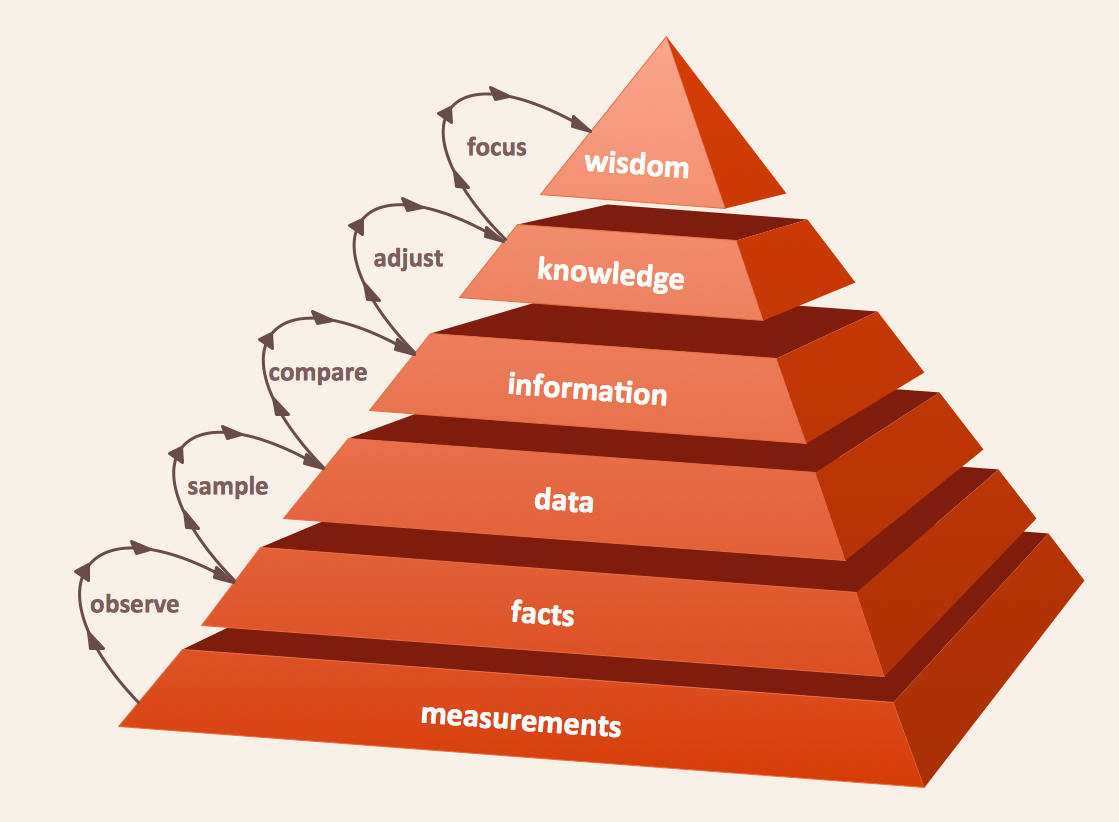
Triangle diagram example of DIKW pyramid has 4 levels: data, information, knowledge and wisdom.Pyramid Diagram
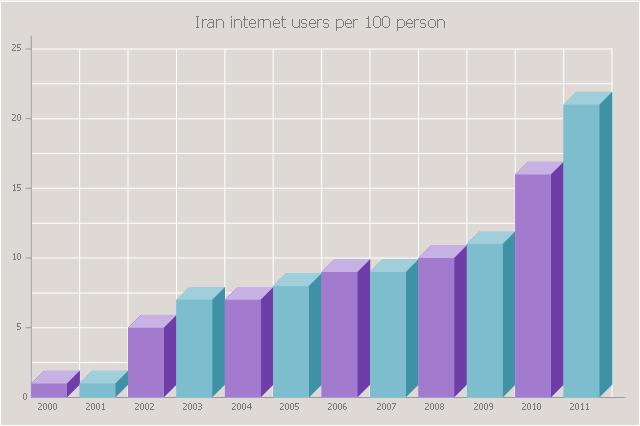
The DIKW Pyramid refers loosely to a class of models for representing purported structural and/or functional relationships between data, information, knowledge, and wisdom.The 3D Column chart example "Iran internet users per 100 person" was redesigned from the Commons Wikimedia file: Iran internet users per 100 person.png.
[commons.wikimedia.org/ wiki/ File:Iran_ internet_ users_ per_ 100_ person.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The data source is World Bank: [data.worldbank.org/ country/ iran-islamic-republic]
"In 1993 Iran became the second country in the Middle East to be connected to the Internet, and since then the government has made significant efforts to improve the nation's ICT infrastructure. Iran's national Internet connectivity infrastructure is based on two major networks: the public switched telephone network (PSTN) and the public data network. The PSTN provides a connection for end-users to Internet service providers (ISPs) over mostly digital lines and supports modem-based connections. The Data Communication Company of Iran (DCI), a subsidiary of TCI, operates the public data network." [Internet in Iran. Wikipedia]
The 3D Column chart example "Iran internet users per 100 person" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Bar Graphs solution from the Graphs and Charts area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ charts-bar-graphs
[commons.wikimedia.org/ wiki/ File:Iran_ internet_ users_ per_ 100_ person.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The data source is World Bank: [data.worldbank.org/ country/ iran-islamic-republic]
"In 1993 Iran became the second country in the Middle East to be connected to the Internet, and since then the government has made significant efforts to improve the nation's ICT infrastructure. Iran's national Internet connectivity infrastructure is based on two major networks: the public switched telephone network (PSTN) and the public data network. The PSTN provides a connection for end-users to Internet service providers (ISPs) over mostly digital lines and supports modem-based connections. The Data Communication Company of Iran (DCI), a subsidiary of TCI, operates the public data network." [Internet in Iran. Wikipedia]
The 3D Column chart example "Iran internet users per 100 person" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Bar Graphs solution from the Graphs and Charts area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ charts-bar-graphs
Business Processes
The most worked out and commonly used methodology of business processes description is IDEF methodology. Besides business processes it allows to describe functional blocks, for example production and marketing. ConceptDraw lets creation of business processes description using IDEF0 and IDEF2 methods.Pyramid Diagram
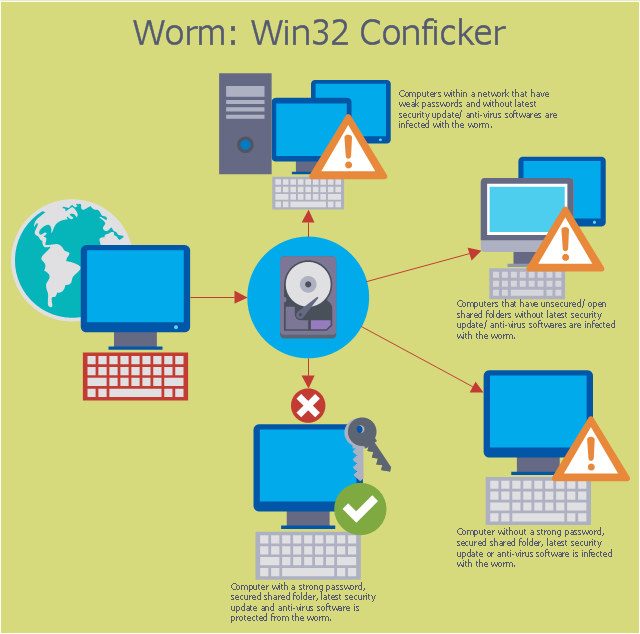
ConceptDraw Pyramid Diagram software allows drawing column charts using predesigned objects or drawing tools.This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
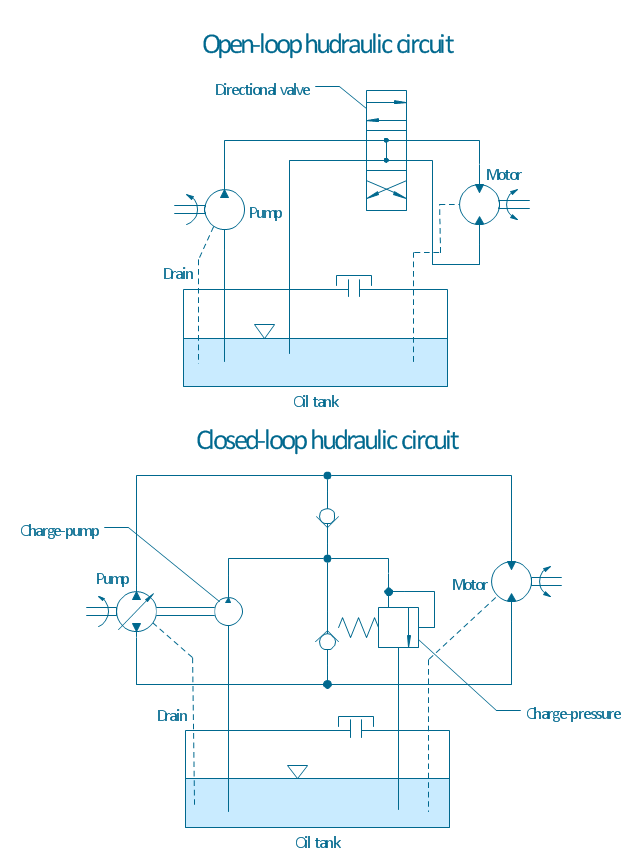
"A hydraulic circuit is a system comprising an interconnected set of discrete components that transport liquid. The purpose of this system may be to control where fluid flows (as in a network of tubes of coolant in a thermodynamic system) or to control fluid pressure (as in hydraulic amplifiers).
... hydraulic circuit theory works best when the elements (passive component such as pipes or transmission lines or active components such as power packs or pumps) are discrete and linear. This usually means that hydraulic circuit analysis works best for long, thin tubes with discrete pumps, as found in chemical process flow systems or microscale devices." [Hydraulic circuit. Wikipedia]
The engineering drawing example "Hydraulic circuits" was redrawn using ConceptDraw PRO diagramming and vector drawing software from the Wikimedia Commons file: Hydraulic circuits.png.
[commons.wikimedia.org/ wiki/ File:Hydraulic_ circuits.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license.
[creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The engineering drawing example "Hydraulic circuits" is included in the Mechanical Engineering solution from the Engineering area of ConceptDraw Solution Park.
... hydraulic circuit theory works best when the elements (passive component such as pipes or transmission lines or active components such as power packs or pumps) are discrete and linear. This usually means that hydraulic circuit analysis works best for long, thin tubes with discrete pumps, as found in chemical process flow systems or microscale devices." [Hydraulic circuit. Wikipedia]
The engineering drawing example "Hydraulic circuits" was redrawn using ConceptDraw PRO diagramming and vector drawing software from the Wikimedia Commons file: Hydraulic circuits.png.
[commons.wikimedia.org/ wiki/ File:Hydraulic_ circuits.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license.
[creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
The engineering drawing example "Hydraulic circuits" is included in the Mechanical Engineering solution from the Engineering area of ConceptDraw Solution Park.
This exaple was resigned from the Wikimedia Commons file: Mobile Cloud Architecture.jpg. [commons.wikimedia.org/ wiki/ File:Mobile_ Cloud_ Architecture.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
This diagram describes general architecture of Mobile Cloud Computing.
Legend.
BTS: Base Transceiver Station.
AAA: Network Authentication, Authorization, and Accounting.
HA: Home Agent.
"Mobile/ cloud computing is the combination of cloud computing and mobile networks to bring benefits for mobile users, network operators, as well as cloud computing providers. The ultimate goal of MCC (mean of MCC is Mobile/ Cloud Computing) is to enable execution of rich mobile applications on a plethora of mobile devices, with a rich user experience. MCC provides business opportunities for mobile network operators as well as cloud providers." [Mobile cloud computing. Wikipedia]
The example "Mobile cloud architecture diagram" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
This diagram describes general architecture of Mobile Cloud Computing.
Legend.
BTS: Base Transceiver Station.
AAA: Network Authentication, Authorization, and Accounting.
HA: Home Agent.
"Mobile/ cloud computing is the combination of cloud computing and mobile networks to bring benefits for mobile users, network operators, as well as cloud computing providers. The ultimate goal of MCC (mean of MCC is Mobile/ Cloud Computing) is to enable execution of rich mobile applications on a plethora of mobile devices, with a rich user experience. MCC provides business opportunities for mobile network operators as well as cloud providers." [Mobile cloud computing. Wikipedia]
The example "Mobile cloud architecture diagram" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Enhancing maps using ConceptDraw MINDMAP′s Theme Gallery
Video tutorials on ConceptDraw products. Try it today!- Tree Network Topology Diagram | Local network area . Computer ...
- How to Convert a Mind Map into MS Word Document | Local area ...
- Tree Network Topology Diagram | Fully Connected Network ...
- Roaming wireless local area network diagram | Call center network ...
- Roaming wireless local area network diagram | Unified ...
- Entity-Relationship Diagram (ERD) | Personal area (PAN) networks ...
- Hotel Network Topology Diagram | Hotel Plan. Hotel Plan Examples ...
- Hotel Network Topology Diagram | Firewall between LAN and WAN ...
- Internet Connectivity. Computer and Network Examples ...
- Network Diagram Software LAN Network Diagrams & Diagrams for ...
- Storage area networks (SAN). Computer and Network Examples ...
- Internet Connectivity. Computer and Network Examples ...
- Architecture Of Network
- Personal area (PAN) networks. Computer and Network Examples ...
- Network Architecture | Internet Connectivity. Computer and Network ...
- Process Flowchart | Cisco Network Diagrams | Circuit diagram - EL ...
- Firewall between LAN and WAN | Hotel Network Topology Diagram ...
- Internet Connectivity. Computer and Network Examples ...
- Architecture Network
- Wireless broadband network diagram | Internet Connectivity ...

---active-directory-network-diagram.png--diagram-flowchart-example.png)