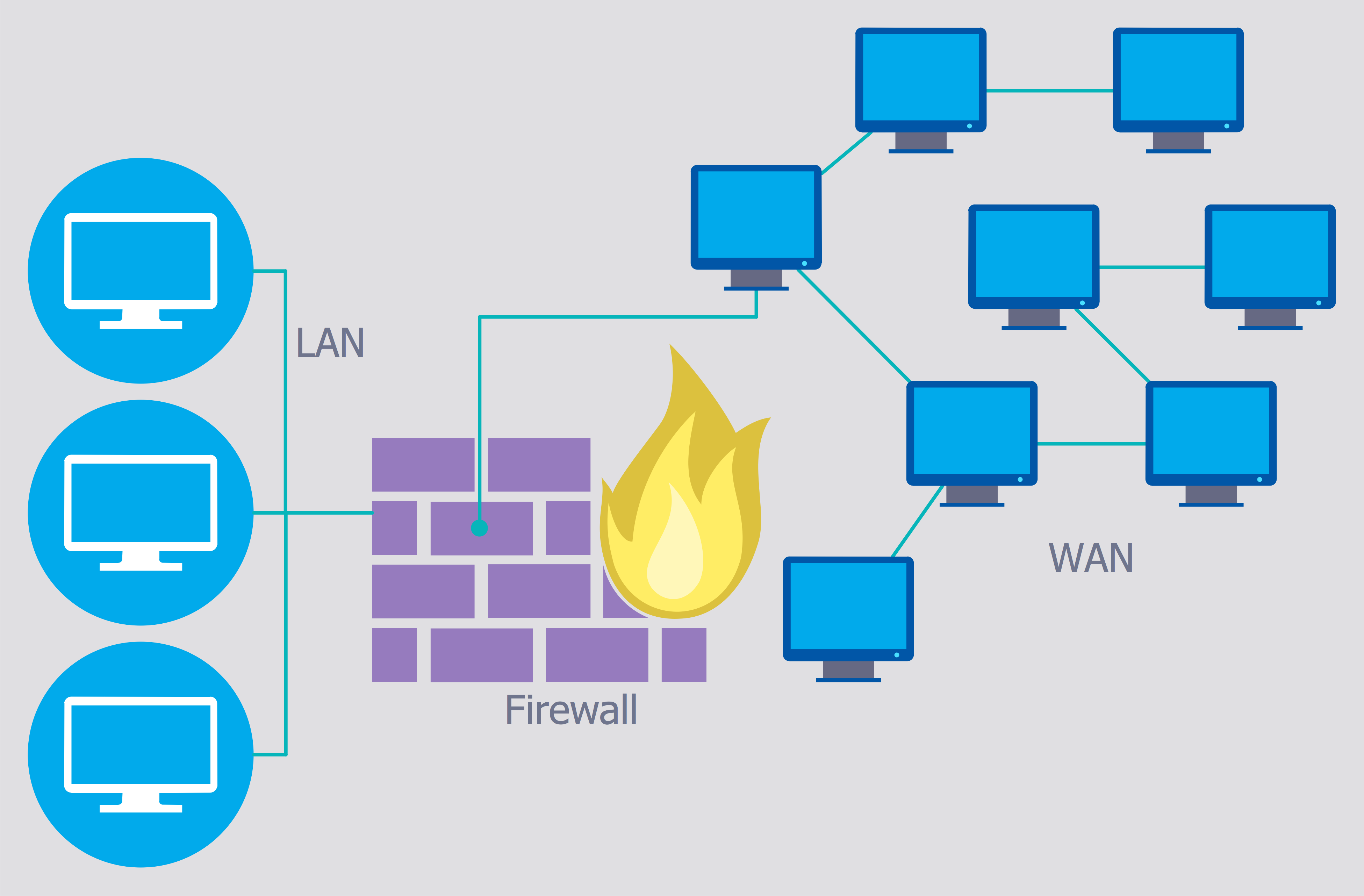
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Secure Wireless Network
Use the ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
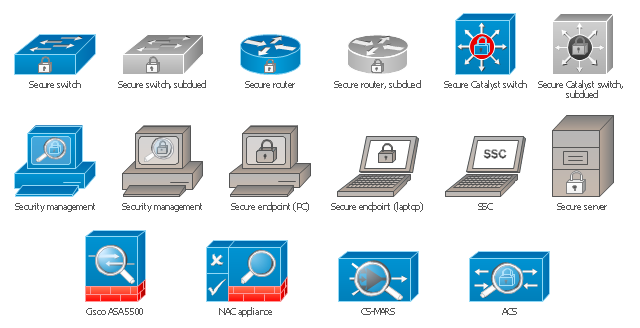
Cisco Security. Cisco icons, shapes, stencils and symbols
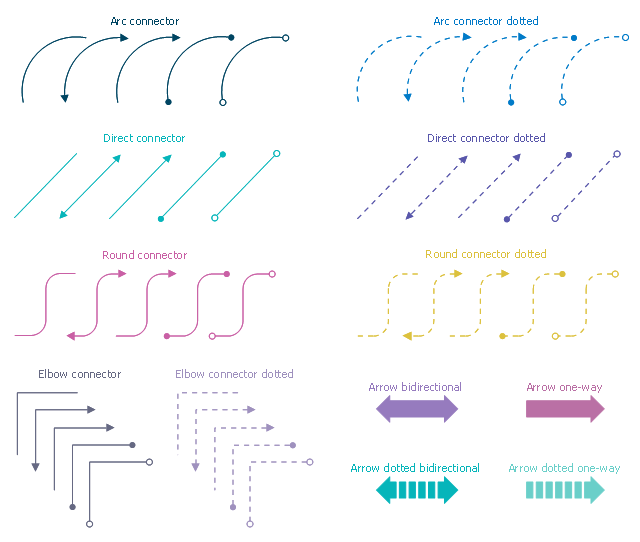
The ConceptDraw vector stencils library "Cisco Security" contains 16 symbols of security devices and equipment for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.The vector stencils library "Cybersecurity connectors" contains 44 network security diagram connection lines.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Network security consists of the policies adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access." [Network security. Wikipedia]
The icon set example "Design elements - Cybersecurity connectors" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Network security consists of the policies adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access." [Network security. Wikipedia]
The icon set example "Design elements - Cybersecurity connectors" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Cisco Network Design. Cisco icons, shapes, stencils, symbols and design elements
Cisco is the largest company, which specializes in the field of high technologies, develops and sells network equipment mainly for the large organizations and telecommunication companies. Cisco produces wide variety of devices and equipment, such as routers, switches, gateways, servers, network security devices (firewalls, VPN, IDs, etc.), ATM switches, cable modems and DSL equipment, access points Wi-Fi, products for IP telephony, etc. The first commercially successful multi-protocol router, which enabled for previously incompatible computers to communicate between themselves, is also developed by Cisco company. Cisco is a generally accepted standard, which uses globally recognized Cisco icons for all produced Cisco equipment. ConceptDraw DIAGRAM software extended with Cisco Network Diagrams solution from Computer and Network area contains a lot of predesigned Cisco network design elements for professional drawing Cisco network diagrams, visualization computer network topologies, equipment connections and arrangement.The vector stencils library "Cybersecurity clipart" contains 197 computer security icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
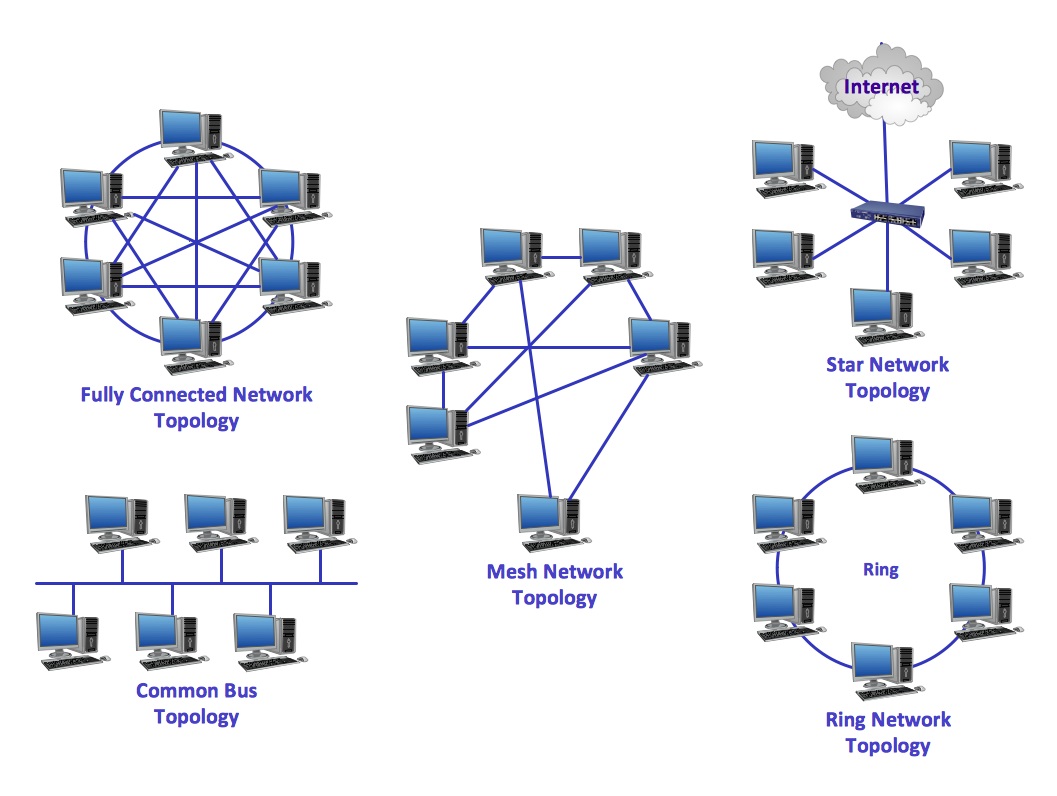
Network Topologies
Network topology is a topological structure of computer network, which can be physical or logical. The physical topology depicts location of different computer network elements such as computers, cables and other devices. The logical topology visually displays network dataflows from one device to another. Sometimes network logical and physical topologies can be the same. ConceptDraw DIAGRAM diagramming and vector drawing software is powerful for drawing network maps and network topologies diagrams of any kinds and complexity thanks to the Computer Network Diagrams solution from the Computer and Networks area. ConceptDraw STORE proposes collection of network icons libraries and a lot of Network Topology Diagram examples, samples and templates which were created at ConceptDraw DIAGRAM software specially for Computer Network Diagrams solution. There are six basic types of the network topologies: Bus, Star, Ring, Mesh, Tree, Fully Connected. You can fast and easy design professional-looking diagram for each of them using the ConceptDraw DIAGRAM tools. There are plenty of web Visio-like diagramming software available. Web based diagrams software can be powerful, but sometimes it is essential to have desktop software. One of the most advanced diagrams tools like Visio for Mac OS is ConceptDraw DIAGRAM app.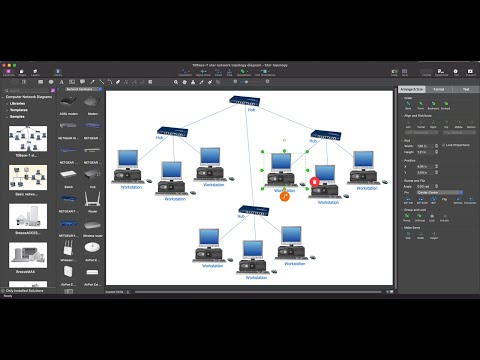
The vector stencils library "Cybersecurity round icons" contains 150 network security diagram icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"A computer network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or, more generally, any telecommunications network. ...
Readily identifiable icons are used to depict common network appliances e.g. Router, and the style of lines between them indicate the type of connection. Clouds are used to represent networks external to the one pictured for the purposes of depicting connections between internal and external devices, without indicating the specifics of the outside network." [Computer network diagram. Wikipedia]
The pictograms example "Design elements - Cybersecurity round icons" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
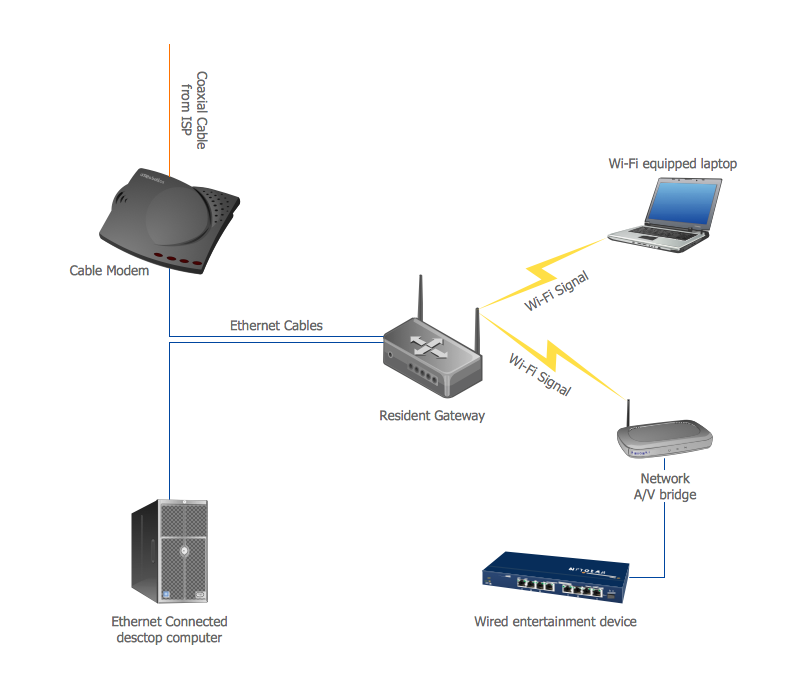
Home area networks (HAN). Computer and Network Examples
A Home Area Networks (HAN) is a type of local area network that is used in an individual home. The home computers can be connected together by twisted pair or by a wireless network. HAN facilitates the communication and interoperability among digital devices at the home, allows to easier access to the entertainments and increase the productivity, organize the home security. This example was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park and shows the home network diagram.
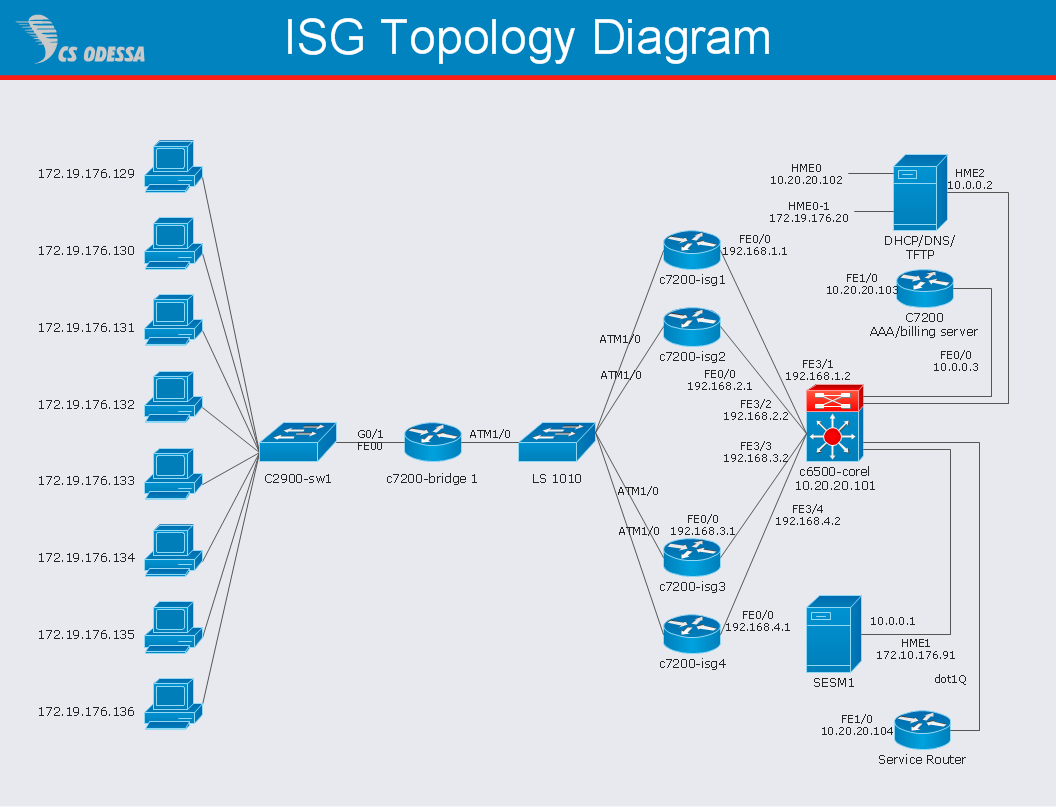
Network Diagram Software ISG Network Diagram
Drawing ISG Network Diagram using ConceptDraw DIAGRAM stencils
 Computer Network Diagrams
Computer Network Diagrams
Computer Network Diagrams solution extends ConceptDraw DIAGRAM software with samples, templates and libraries of vector icons and objects of computer network devices and network components to help you create professional-looking Computer Network Diagrams, to plan simple home networks and complex computer network configurations for large buildings, to represent their schemes in a comprehensible graphical view, to document computer networks configurations, to depict the interactions between network's components, the used protocols and topologies, to represent physical and logical network structures, to compare visually different topologies and to depict their combinations, to represent in details the network structure with help of schemes, to study and analyze the network configurations, to communicate effectively to engineers, stakeholders and end-users, to track network working and troubleshoot, if necessary.
HelpDesk
How to Create a Network Security Diagram
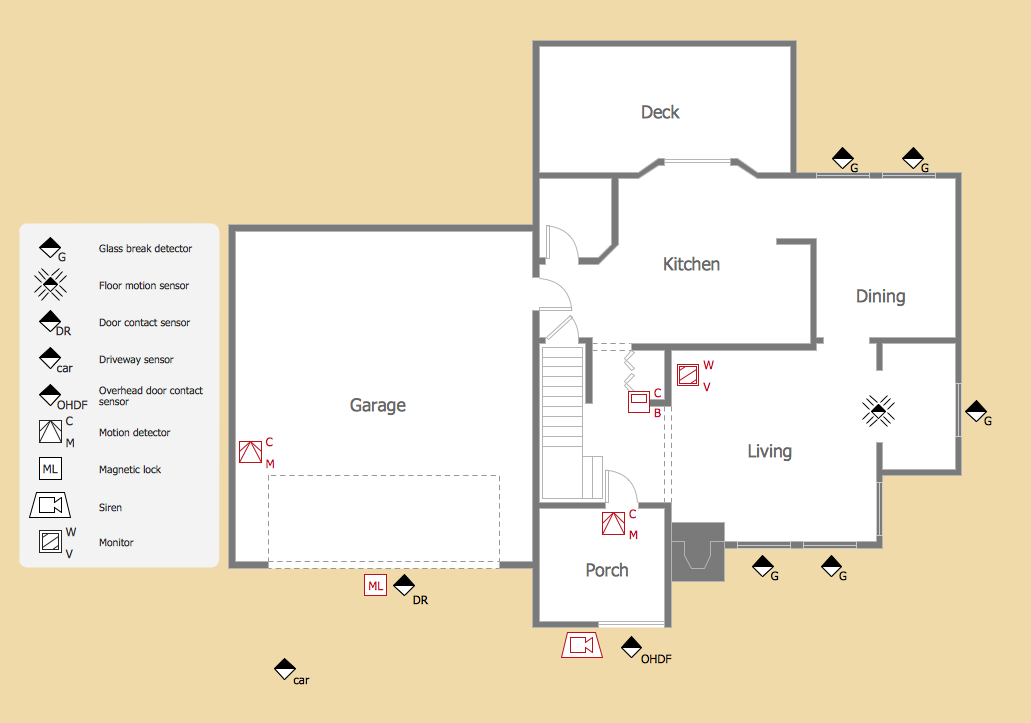
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns a piece of information, considered to be valuable. The enforcement of network security, whether it be local network security, or wireless network security is the core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. The network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of a security system can be presented in the form of a Network Security diagram. ConceptDraw DIAGRAM provides the toolkit for network security system visualization with its Network Security Diagram solution.Physical Security Plan
ConceptDraw DIAGRAM diagramming and vector drawing software extended with Security and Access Plans Solution from the Building Plans Area of ConceptDraw Solution Park is a powerful software for fast and easy drawing professional looking Physical Security Plan.- Design elements - Cybersecurity round icons | Cyber Security ...
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- Design elements - Cybersecurity connectors | Cyber Security ...
- Design elements - Access and security | Network Security ...
- Design elements - Cybersecurity clipart | Network Security Devices ...
- Network Security Diagrams | Cyber Security Degrees | Design ...
- ConceptDraw Solution Park | Design elements - Access and security ...
- UML Deployment Diagram. Design Elements | Computer Network ...
- Design elements - Access and security | Network Security Devices ...
- Network Security Devices | Cisco Network Design. Cisco icons ...
- Cisco security - Vector stencils library | Design elements - Cisco ...
- Design elements - Cybersecurity clipart | Design elements ...
- Spread of Conficker worm | Network Security Diagrams | Design ...
- Design elements - Presentation symbols | Introduction to Cloud ...
- Design elements - Alarm and access control | Camera layout ...
- Security system plan | Security Plans | Network Security Devices ...
- How to Create a Network Security Diagram Using ConceptDraw PRO
- Cisco Security . Cisco icons, shapes, stencils and symbols | Office ...
- Design elements - Network layout floorplan | Mesh Network ...
- Network Security Devices | Network Security | Hotel Network ...