Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Network Security Architecture Diagram
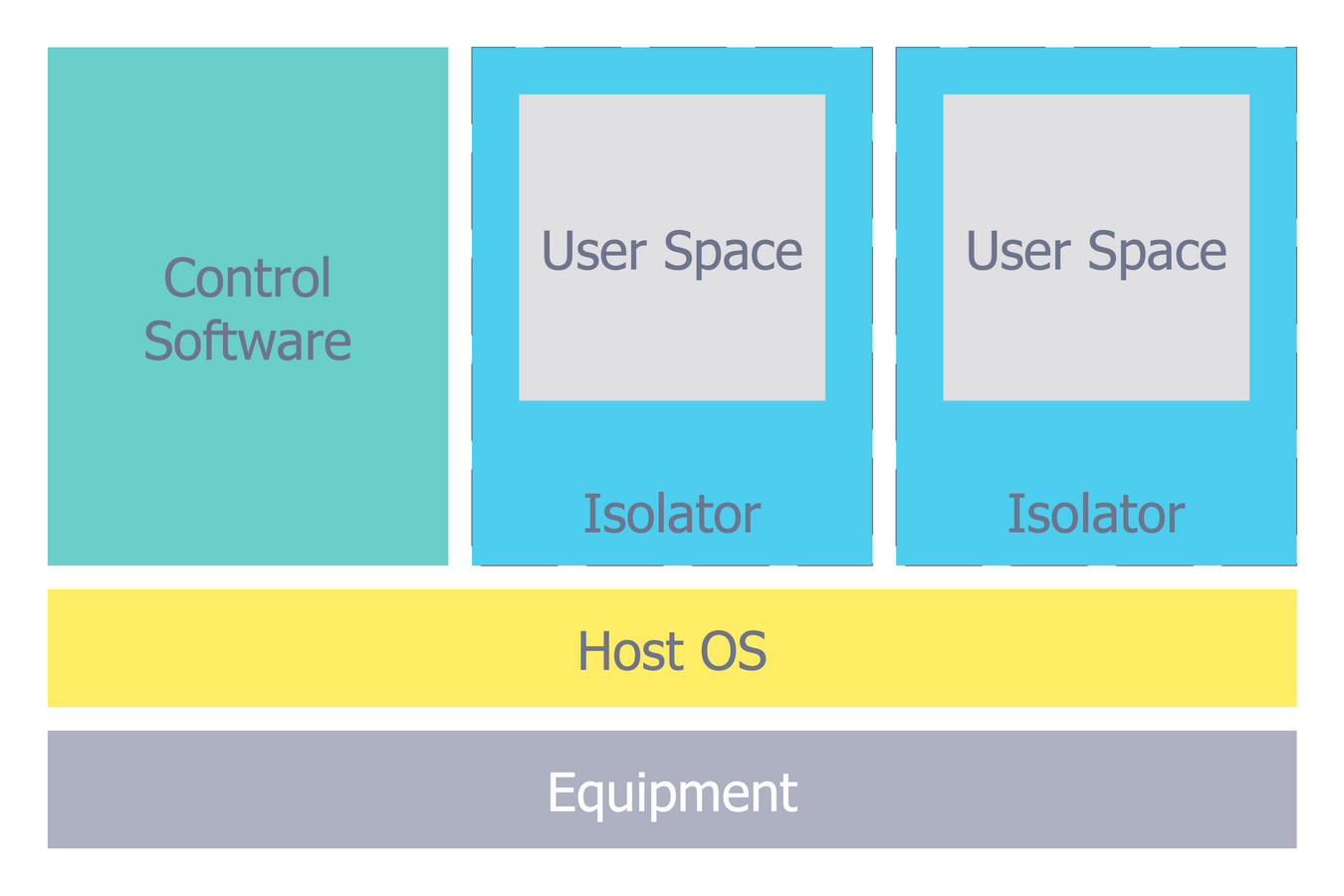
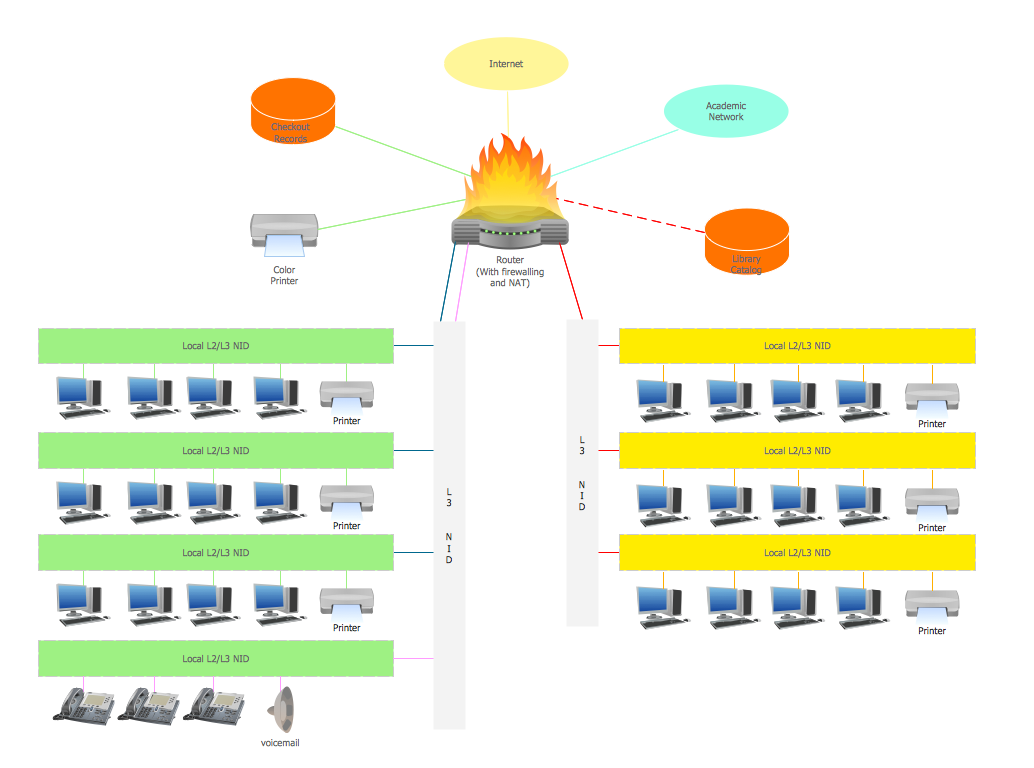
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw DIAGRAM extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Network Security
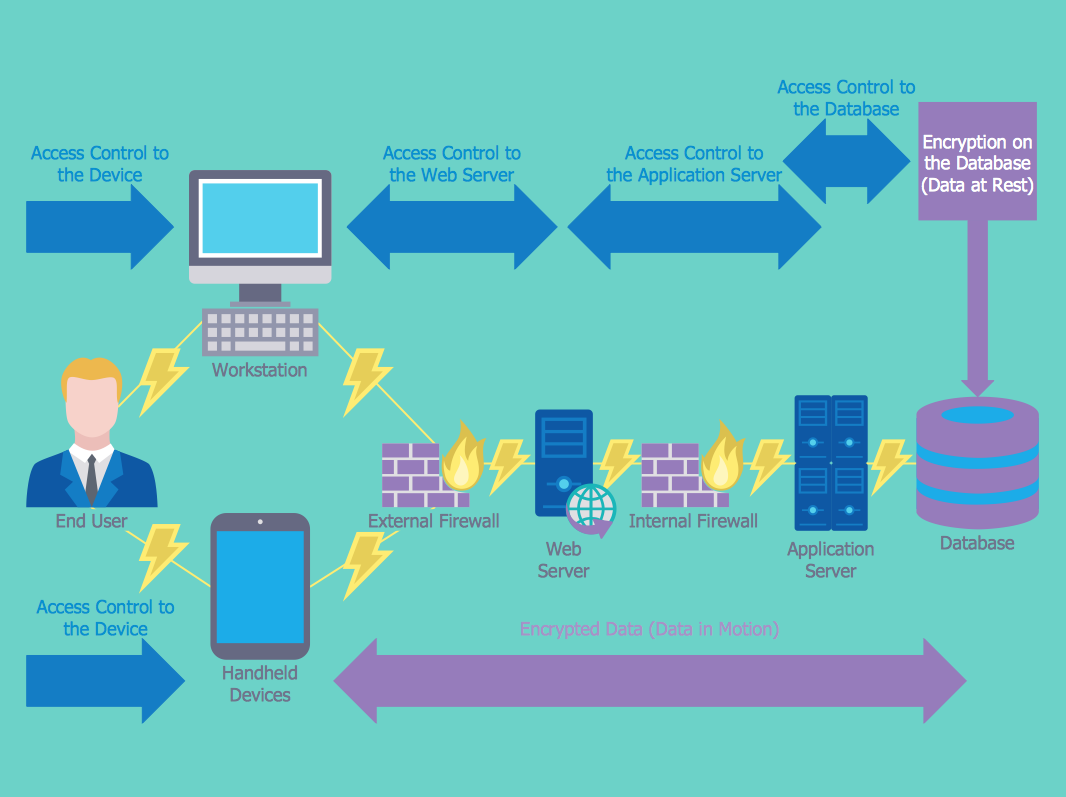
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices.Network Topologies
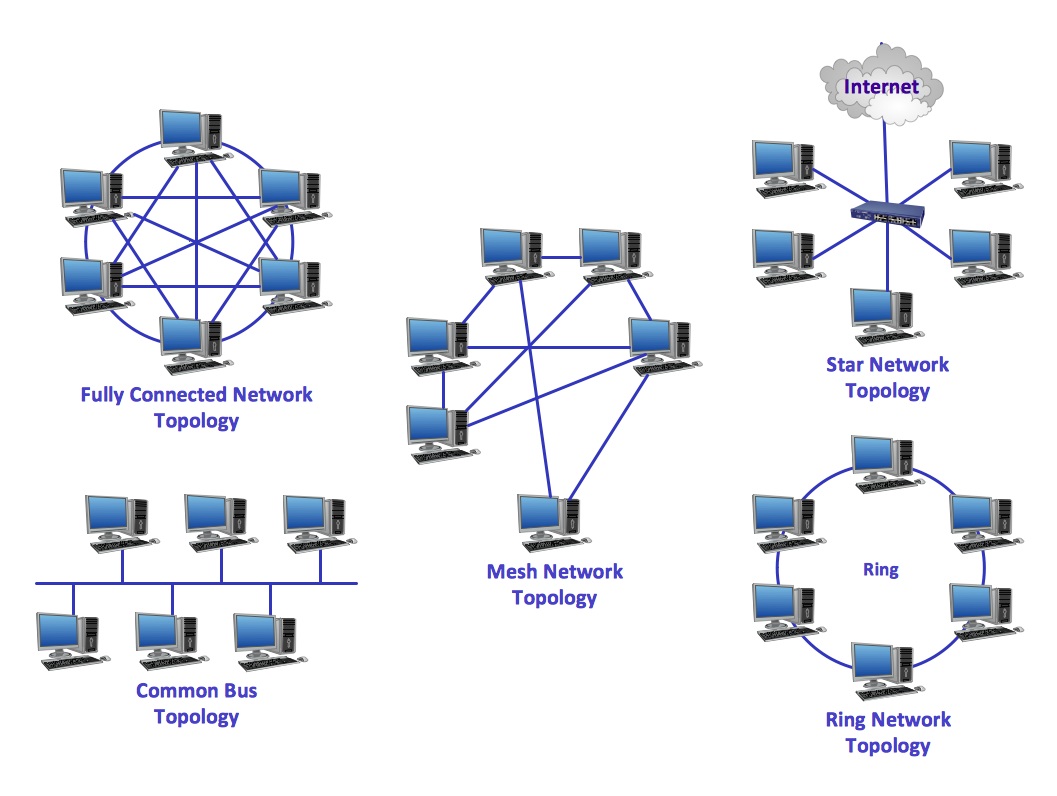
Network topology is a topological structure of computer network, which can be physical or logical. The physical topology depicts location of different computer network elements such as computers, cables and other devices. The logical topology visually displays network dataflows from one device to another. Sometimes network logical and physical topologies can be the same. ConceptDraw DIAGRAM diagramming and vector drawing software is powerful for drawing network maps and network topologies diagrams of any kinds and complexity thanks to the Computer Network Diagrams solution from the Computer and Networks area. ConceptDraw STORE proposes collection of network icons libraries and a lot of Network Topology Diagram examples, samples and templates which were created at ConceptDraw DIAGRAM software specially for Computer Network Diagrams solution. There are six basic types of the network topologies: Bus, Star, Ring, Mesh, Tree, Fully Connected. You can fast and easy design professional-looking diagram for each of them using the ConceptDraw DIAGRAM tools. There are plenty of web Visio-like diagramming software available. Web based diagrams software can be powerful, but sometimes it is essential to have desktop software. One of the most advanced diagrams tools like Visio for Mac OS is ConceptDraw DIAGRAM app.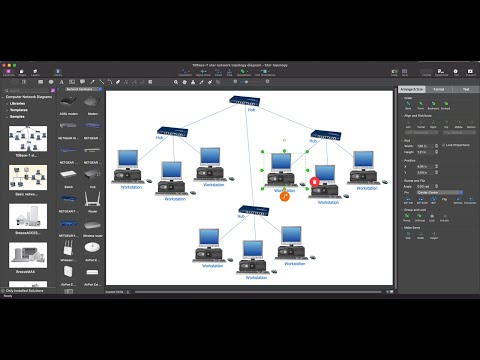
HelpDesk
How to Create a Network Security Diagram
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns a piece of information, considered to be valuable. The enforcement of network security, whether it be local network security, or wireless network security is the core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. The network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of a security system can be presented in the form of a Network Security diagram. ConceptDraw DIAGRAM provides the toolkit for network security system visualization with its Network Security Diagram solution.ATM Network. Computer and Network Examples
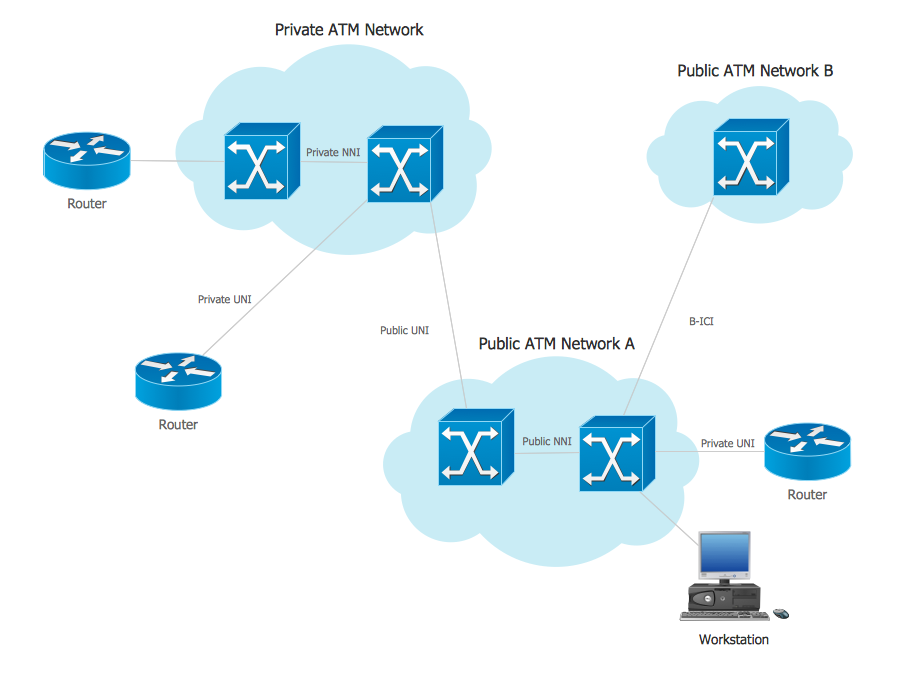
Asynchronous Transfer Mode (ATM) is a high-speed networking standard intended for supporting the voice and data communications. ConceptDraw DIAGRAM is a powerful network diagramming and vector drawing software that provides the Computer and Networks solution with wide set of ready-to-use predesigned vector stencils and examples to help you design the ATM Networks quick and easy.
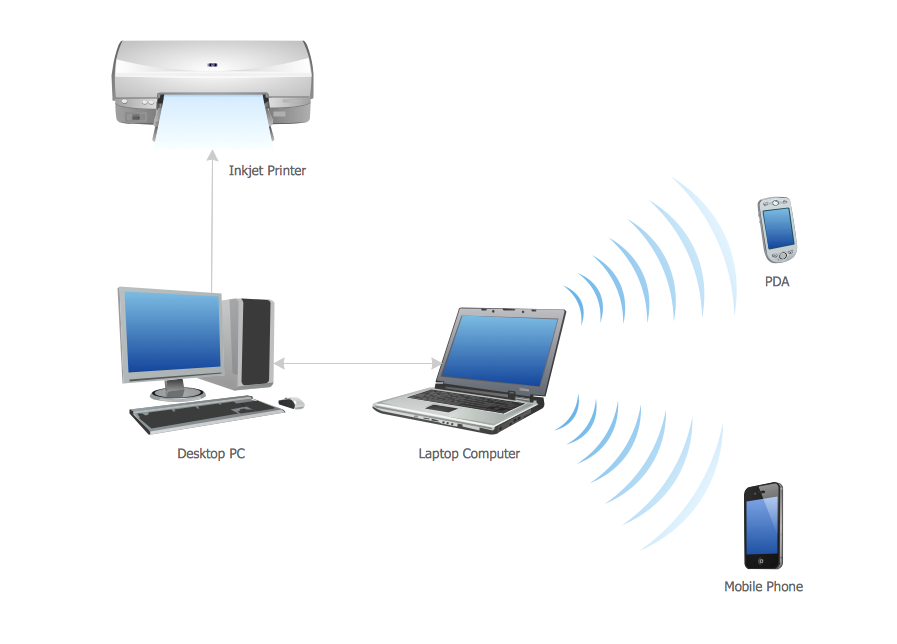
Personal area (PAN) networks. Computer and Network Examples
Personal area network (PAN) is a network organized on a limited area and used for data transmission between various personal devices, such as computers, tablets, laptops, telephones, different digital and mobile devices, etc. and also for connecting to higher level network and Internet. PAN is used to manage the interconnections of IT devices which surround a single user and generally contains such appliances, as cordless mice, keyboard, phone, and Bluetooth handsets. PANs can be wired with computer buses, or wirelessly connected to the Internet using such network technologies as Bluetooth, Z-Wave, ZigBee, IrDa, UWB, Body Area Network. PANs have a lot of pros and cons, they are expedient, lucrative and handy, but sometimes have bad connection with other networks on the same radio bands, Bluetooth has distance limits and slow data transfer speed, but is comparatively safe. ConceptDraw DIAGRAM diagramming software supplied with numerous solutions of Computer and Networks Area included to ConceptDraw Solution Park perfectly suits for designing the Personal Area Networks.
Campus Area Networks (CAN). Computer and Network Examples
Campus Area Network (CAN) is a computer network which provides wireless access to the Internet or LAN for the users located in two or more buildings on the limited geographical area, or in the open space surrounding these buildings. Campus Area Network is usually set in campus of a university or college, but the same kind of planning and design can be applied for other purposes, for enterprises, office buildings, military bases, industrial complexes, public places like supermarkets, entertainment centers, etc. Another form of temporary CAN can exist during some special events such as rallies, music festivals. The elementary Campus Area Network can also arise spontaneously, due to the distance of spread the radio signals from the access points that are not limited by buildings walls. It is also sensible to have additional access points for the larger and more complex CANs, located at specially places chosen for serving clients. Design easy diagrams and schemes for the Campus Area Networks with Computer Network Diagrams solution for ConceptDraw DIAGRAM.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
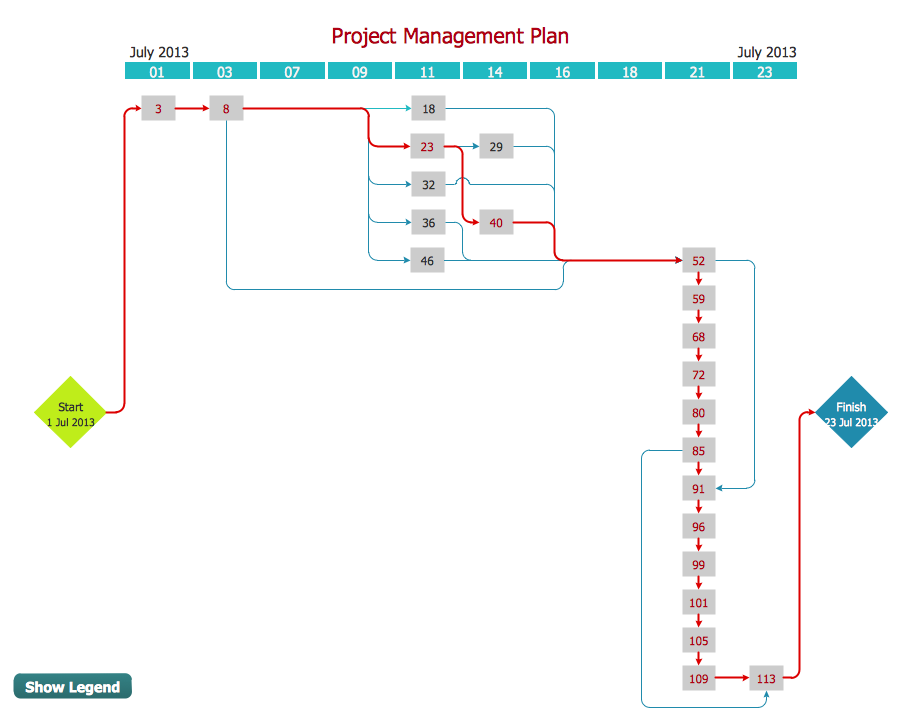
Activity Network Diagram Method
Activity Network Diagram - This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the Seven Management and Planning Tools solution from the Management area of ConceptDraw Solution Park. This sample shows the PERT (Program Evaluation Review Technique) chart of the request on proposal. A request for proposal (RFP) is a request of the company or the organization to potential suppliers to submit the business proposals for service or goods that it is interested to purchase. The RFP is represented on the initial procurement stage and allows to define the risks and benefits.- Types Of Network Security Models
- Security Plans | Network Layout Floor Plans | Network Security ...
- Computer Network Diagrams | Block Diagram Of Different Types Of ...
- How to Create a Network Security Diagram Using ConceptDraw ...
- Cisco Network Diagrams | Telecommunication Network Diagrams ...
- Network Security Diagrams | Network Diagram Software ISG ...
- Computer Network Diagrams | Network Security Diagrams | Wan ...
- Network Security Diagrams | How to Create a Network Security ...
- How to Create a Network Security Diagram Using ConceptDraw ...
- Architecture Diagrams | Network Security Architecture Diagram ...