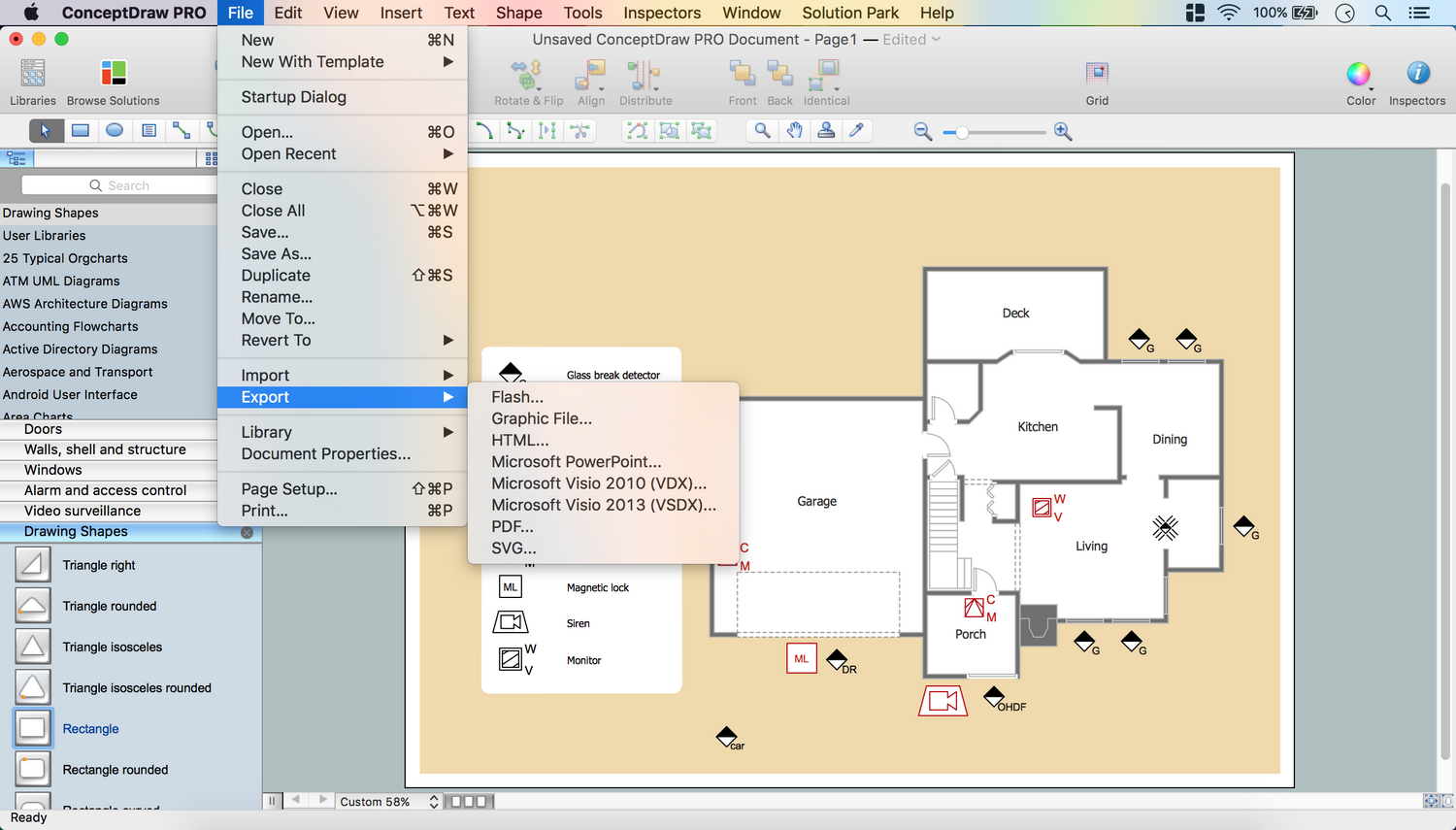
The vector stencils library "Alarm and access control" contains 80 shapes of digital proximity equipment, locking hardware, and access control equipment. Use it for drawing security and access plans of intrusion systems, time and attendance systems, and card and code access control security systems with ConceptDraw PRO software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
 Sales Flowcharts
Sales Flowcharts
The Sales Flowcharts solution lets you create and display sales process maps, sales process workflows, sales steps, the sales process, and anything else involving sales process management.
Security Plans
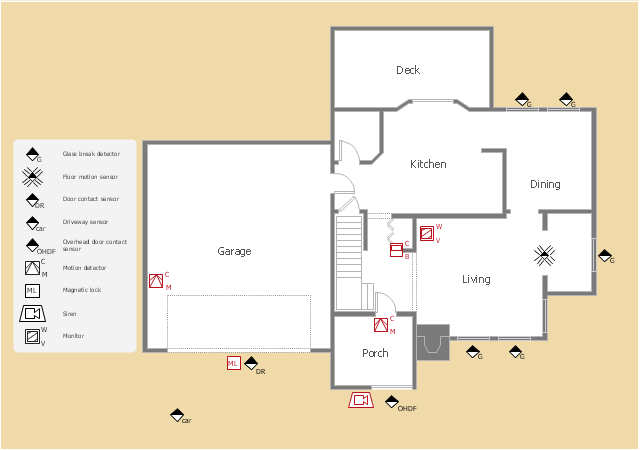
No security system cannot be constructed without detailed security plan, or even a set of plans in some cases. ConceptDraw PRO software offers the Security and Access Plans Solution from the Building Plans Area to help you design the Security Plans for any premises and of any complexity."A security alarm is a system designed to detect intrusion – unauthorized entry – into a building or area. Security alarms are used in residential, commercial, industrial, and military properties for protection against burglary (theft) or property damage, as well as personal protection against intruders. Car alarms likewise protect vehicles and their contents. Prisons also use security systems for control of inmates.
Some alarm systems serve a single purpose of burglary protection; combination systems provide both fire and intrusion protection. Intrusion alarm systems may also be combined with closed-circuit television surveillance systems to automatically record the activities of intruders, and may interface to access control systems for electrically locked doors. Systems range from small, self-contained noisemakers, to complicated, multi-area systems with computer monitoring and control." [Security alarm. Wikipedia]
The example "Security system plan" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
Some alarm systems serve a single purpose of burglary protection; combination systems provide both fire and intrusion protection. Intrusion alarm systems may also be combined with closed-circuit television surveillance systems to automatically record the activities of intruders, and may interface to access control systems for electrically locked doors. Systems range from small, self-contained noisemakers, to complicated, multi-area systems with computer monitoring and control." [Security alarm. Wikipedia]
The example "Security system plan" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity" contains 24 cybersecurity icons.
Use it to design your computer and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
Use it to design your computer and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
The vector stencils library "Cybersecurity" contains 24 cybersecurity icons.
Use it to design your computer and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
Use it to design your computer and telecom illustrations and infographics with ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Cybersecurity" is included in the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
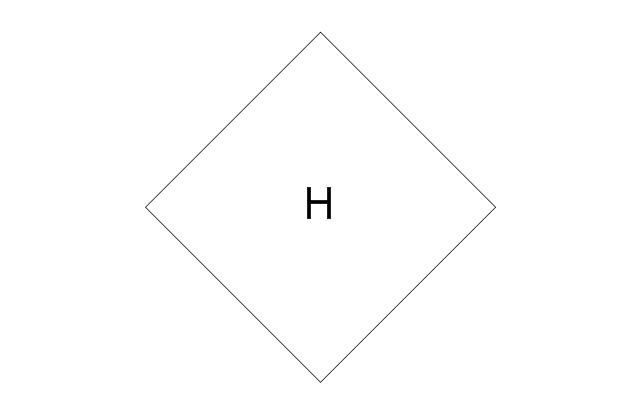
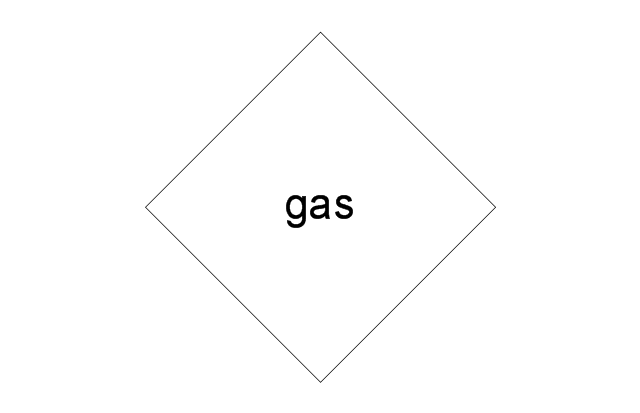
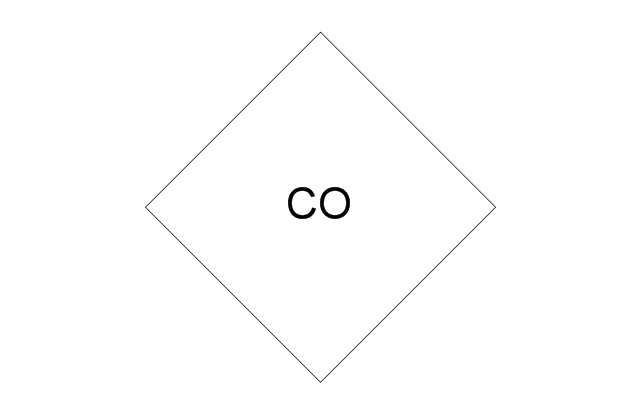
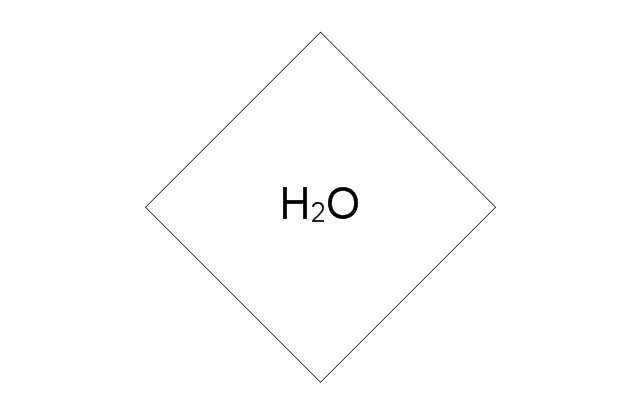
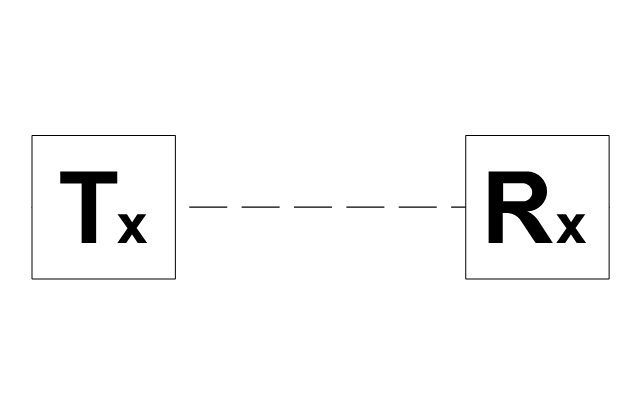
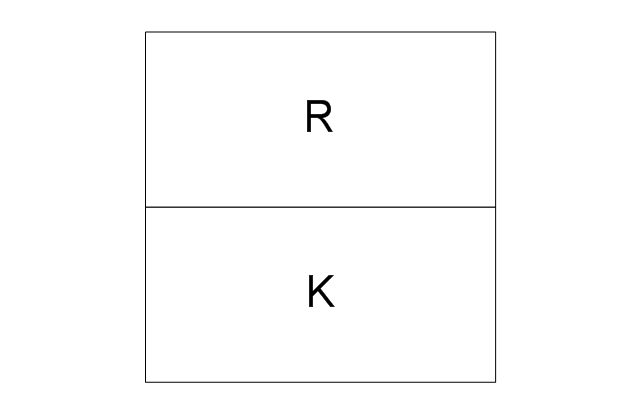
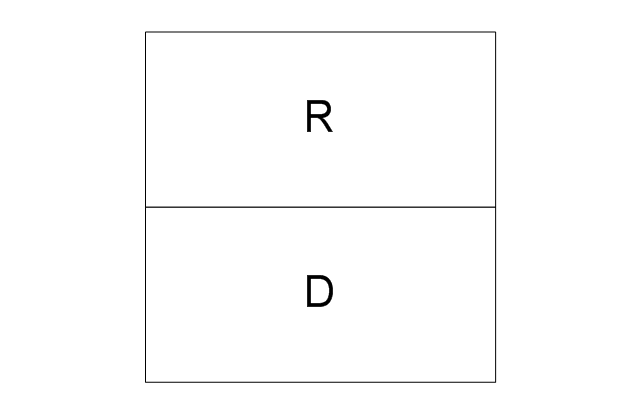
The vector stencils library "Logical symbols" contains 49 logical symbols for drawing logical network topology diagrams.
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
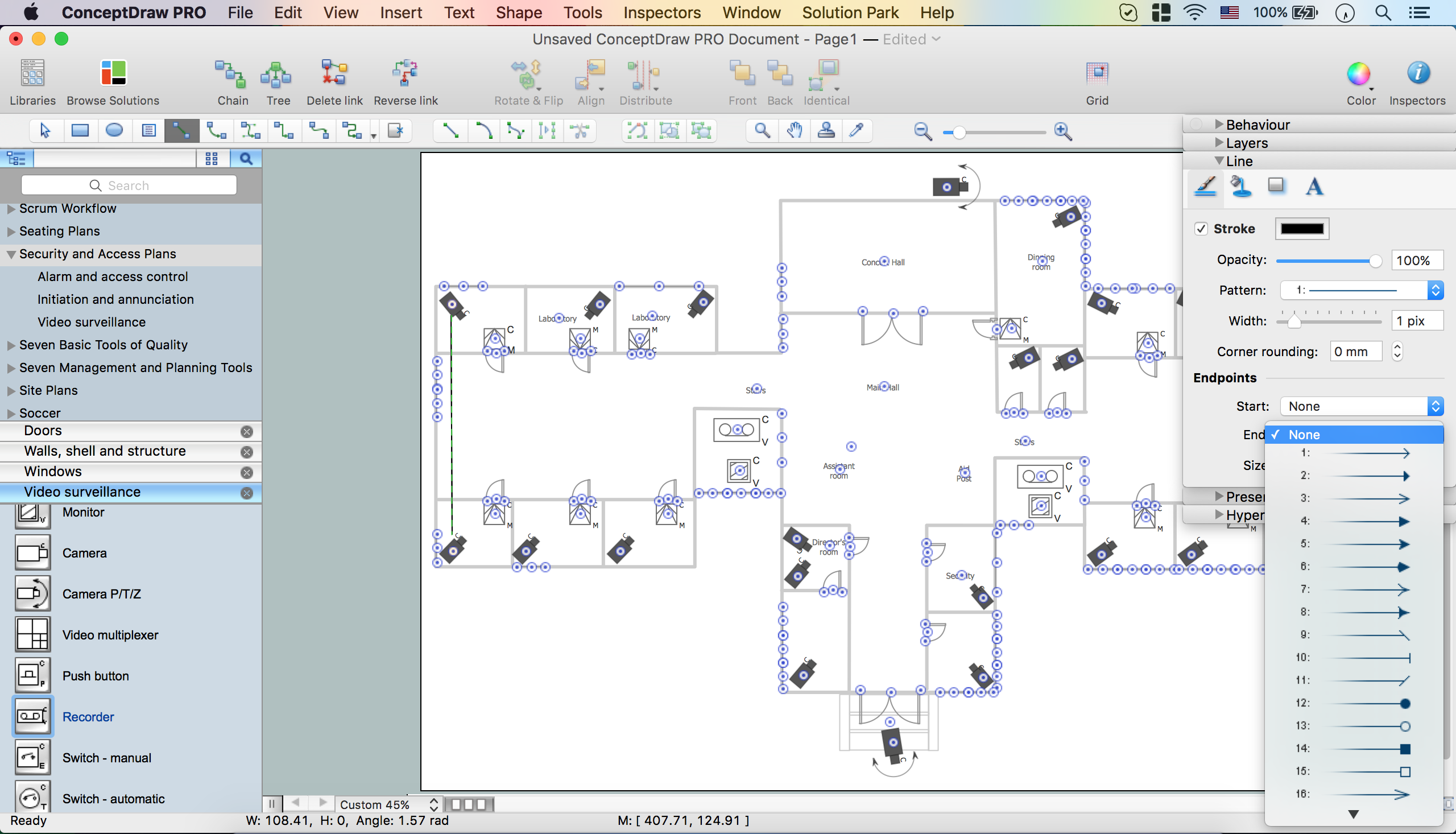
How To Create CCTV Network Diagram
Closed-circuit television (CCTV) uses cameras and monitors to carry out video surveillance. Unlike broadcast television this system has only local signal. It is a feature of almost every video camera, yet CCTV is mainly a system for visual control of certain areas such as banks, airports, supermarkets, and other places for security reasons. Developing and installing CCTV system is a time-consuming process. It also requires certain knowledge and skills. ConceptDraw is a solution of setting video cameras rationally. You can achieve two aims at once: CCTV Design Tool saves your time and your money and helps you make professional video surveillance system.
 Security and Access Plans
Security and Access Plans
This solution extends ConceptDraw PRO software with physical security plan, security chart, access chart, security plans, access schemes, access plans , CCTV System Plan samples, templates and libraries of design elements for drawing the Security and Acce
The vector stencils library "Logical symbols" contains 49 logical symbols for drawing logical network topology diagrams.
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks



























-logical-symbols---vector-stencils-library.png--diagram-flowchart-example.png)