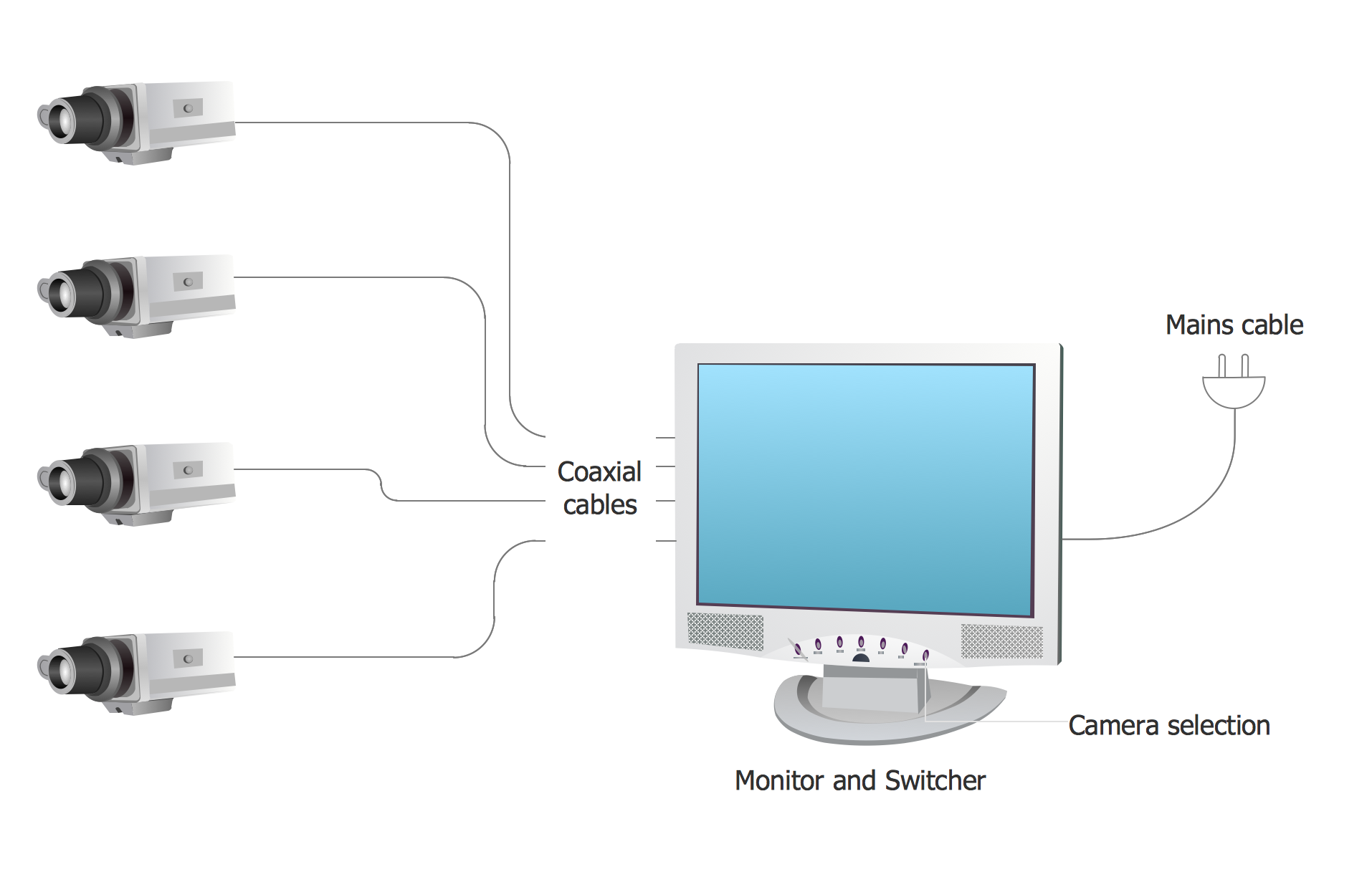
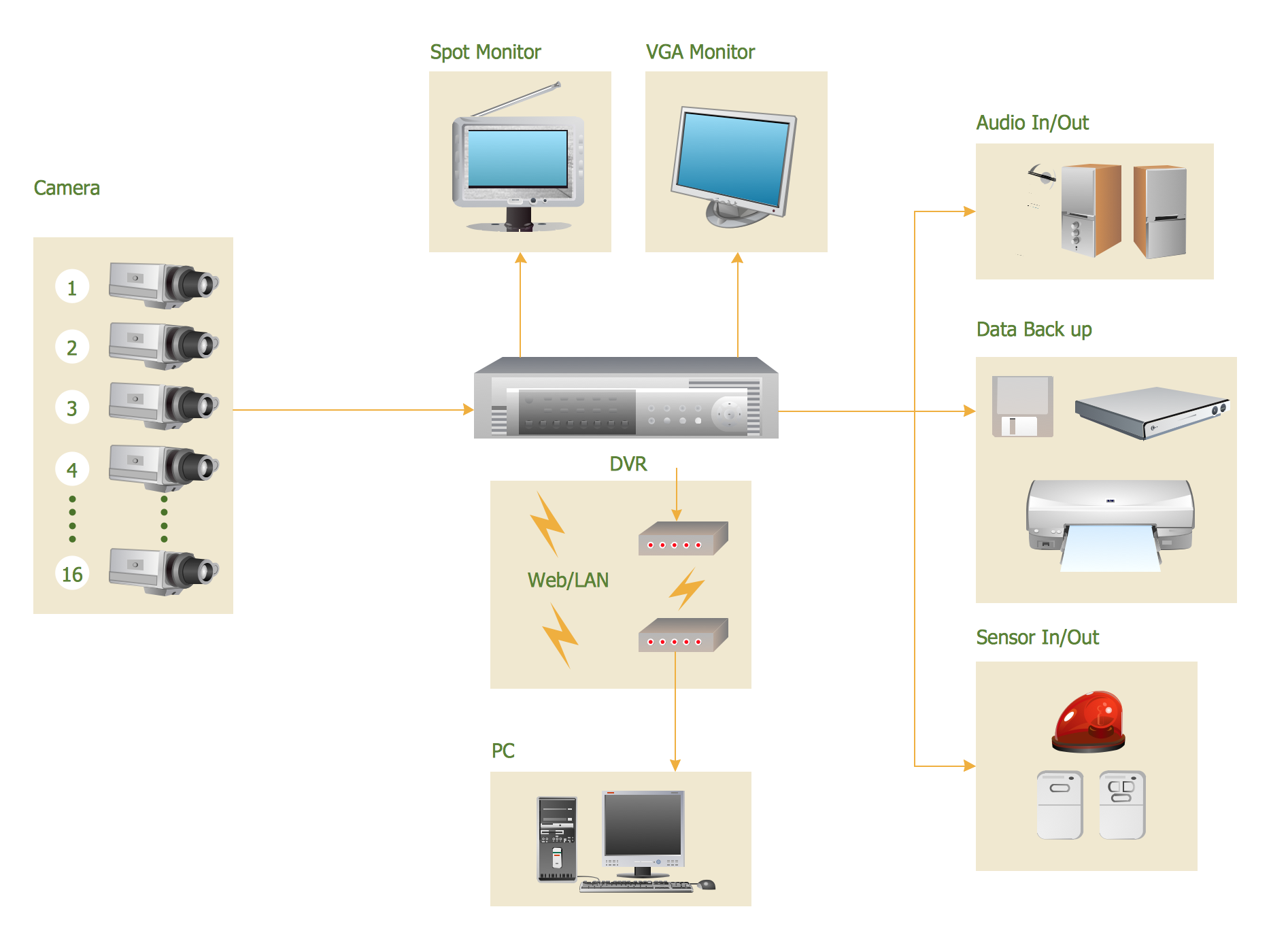
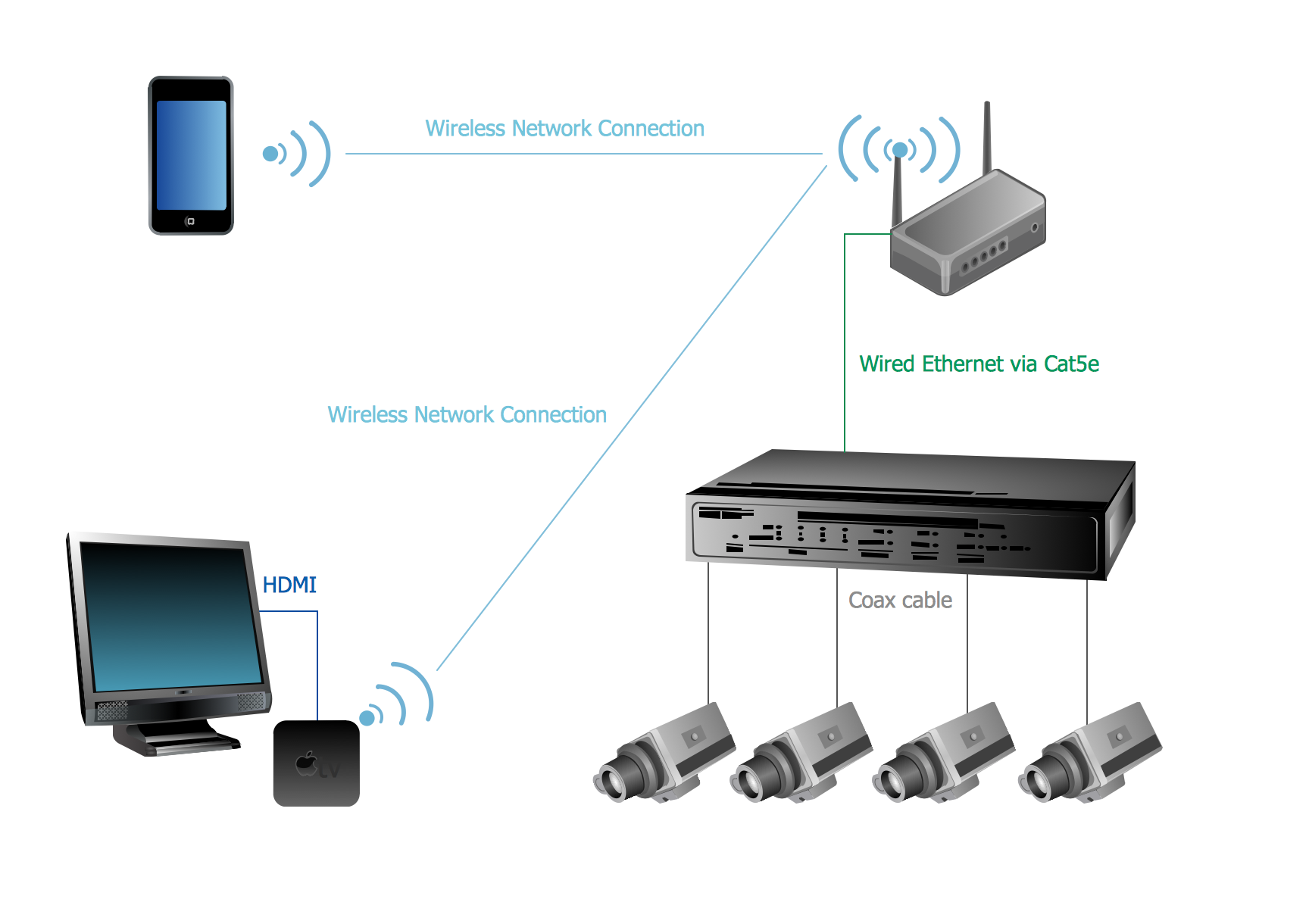
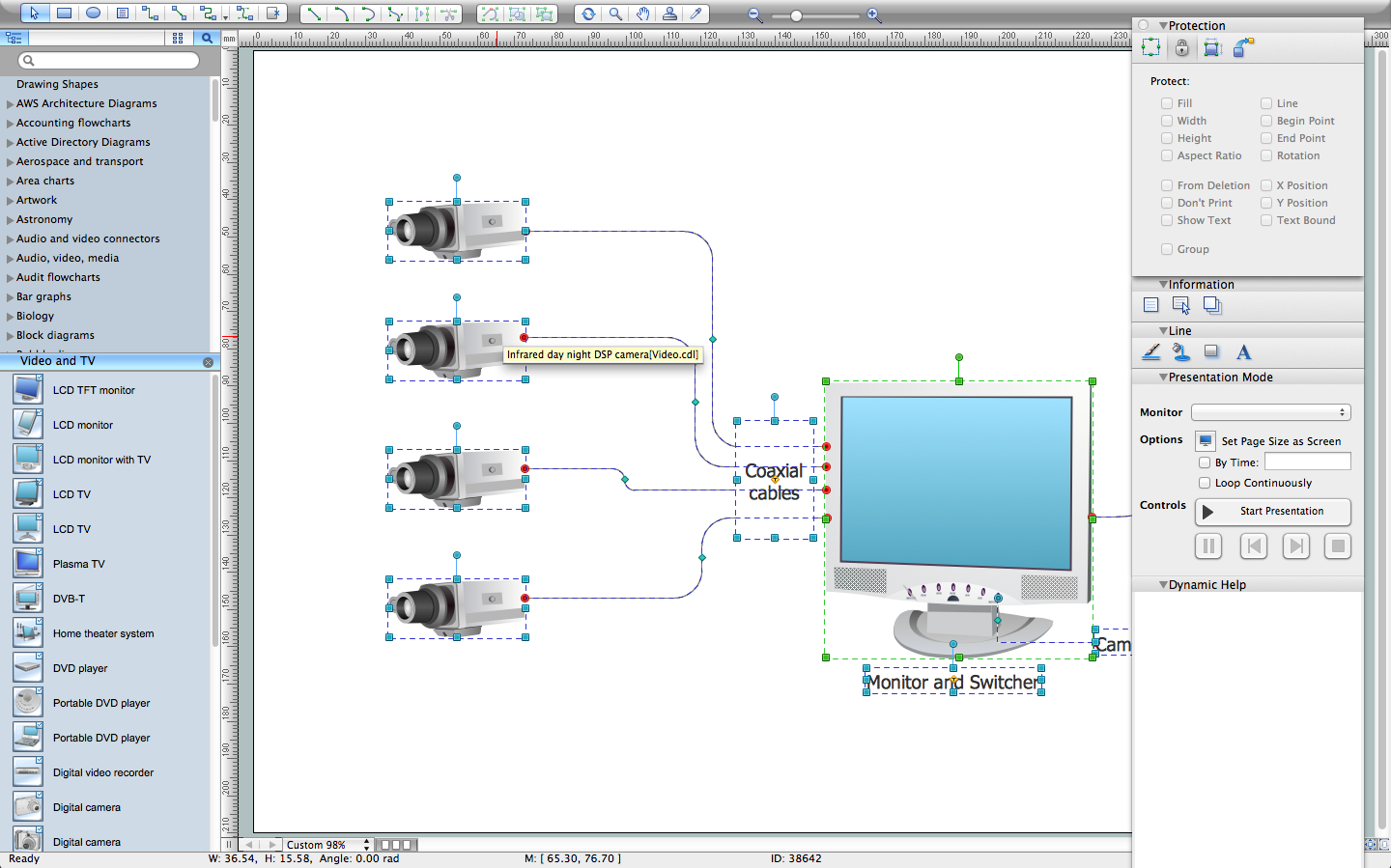
Basic CCTV System Diagram. CCTV Network Diagram Example
ConceptDraw PRO enhanced with Audio, Video, Media solution is a helpful tool for illustration of a CCTV network. It contains library of vector cliparts of video and TV devices and different digital gadgets for drawing such illustrationsCCTV Surveillance System Diagram. CCTV Network Diagram Example
Creating CCTV system diagrams is quick and easy with ConceptDraw PRO diagramming software enhanced with Audio, Video, Media solution from ConceptDraw Solution Park. It contains library of vector cliparts of video and TV devices and different digital gadgets for drawing this kind of diagrams.
 Security and Access Plans
Security and Access Plans
This solution extends ConceptDraw PRO software with physical security plan, security chart, access chart, security plans, access schemes, access plans , CCTV System Plan samples, templates and libraries of design elements for drawing the Security and Acce
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw PRO extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park."Surveillance is the monitoring of the behavior, activities, or other changing information, usually of people for the purpose of influencing, managing, directing, or protecting them. This can include observation from a distance by means of electronic equipment (such as CCTV cameras), or interception of electronically transmitted information (such as Internet traffic or phone calls); and it can include simple, relatively no- or low-technology methods such as human intelligence agents and postal interception. ...
Surveillance is very useful to governments and law enforcement to maintain social control, recognize and monitor threats, and prevent/ investigate criminal activity. With the advent of programs such as the Total Information Awareness program and ADVISE, technologies such as high speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of their subjects." [Surveillance. Wikipedia]
[itl.nist.gov/ iad/ 894.01/ tests/ avss/ 2009/ ]
The example "Camera layout schematic" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
Surveillance is very useful to governments and law enforcement to maintain social control, recognize and monitor threats, and prevent/ investigate criminal activity. With the advent of programs such as the Total Information Awareness program and ADVISE, technologies such as high speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of their subjects." [Surveillance. Wikipedia]
[itl.nist.gov/ iad/ 894.01/ tests/ avss/ 2009/ ]
The example "Camera layout schematic" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.CCTV Network Example
The following examples cctv network were created in ConceptDraw PRO diagramming and vector drawing software using the Audio, Video, Media Solution. Using this easily customizable cctv network template you can represent any existing cctv network.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
CCTV Network Diagram Software
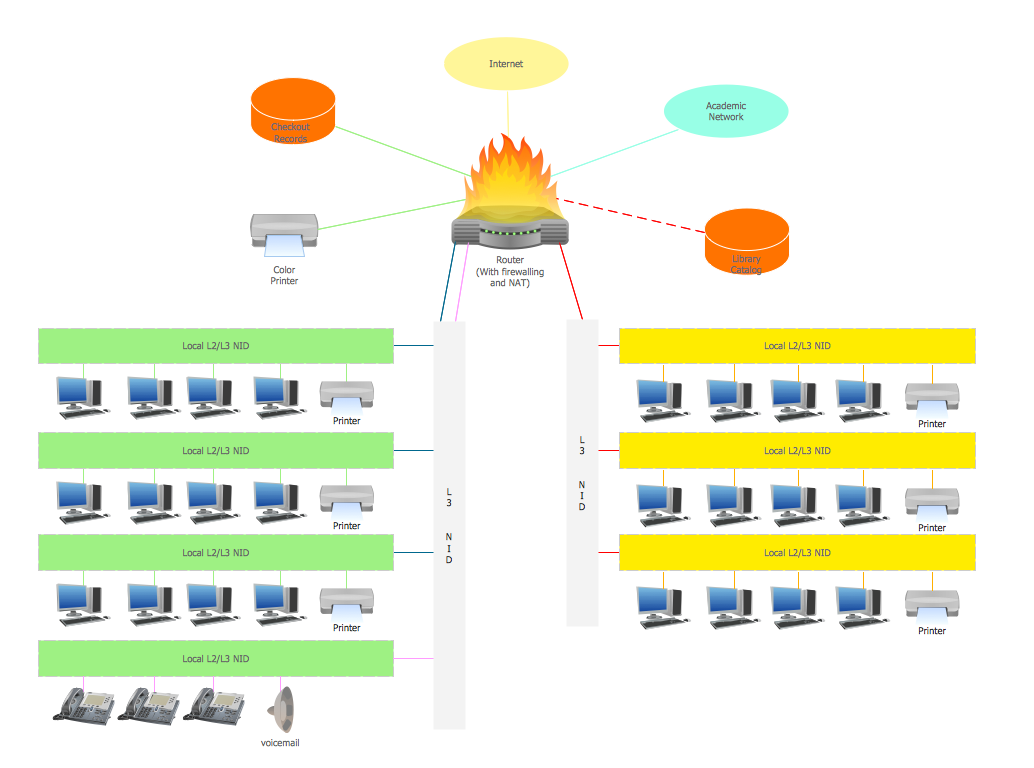
The CCTV is the process that carried out using the video cameras for transmitting the signal to the specific location, on the limited set of monitors. We are talking about the video cameras that are used for monitoring on such guarded objects as airports, banks, stores, military objects, etc. CCTV equipment is also used in the industrial installations, for surveillance in the public places, for recording the video on the digital video recorders.Campus Area Networks (CAN). Computer and Network Examples
Campus Area Network (CAN) is a computer network which provides wireless access to the Internet or LAN for the users located in two or more buildings on the limited geographical area, or in the open space surrounding these buildings. Campus Area Network is usually set in campus of a university or college, but the same kind of planning and design can be applied for other purposes, for enterprises, office buildings, military bases, industrial complexes, public places like supermarkets, entertainment centers, etc. Another form of temporary CAN can exist during some special events such as rallies, music festivals. The elementary Campus Area Network can also arise spontaneously, due to the distance of spread the radio signals from the access points that are not limited by buildings walls. It is also sensible to have additional access points for the larger and more complex CANs, located at specially places chosen for serving clients. Design easy diagrams and schemes for the Campus Area Networks with Computer Network Diagrams solution for ConceptDraw PRO.
- How To Indicate Cctv Camera On A Building Plan
- Basic CCTV System Diagram. CCTV Network Diagram Example ...
- Camera layout schematic | CCTV Network Example | Basic CCTV ...
- How to Create a CCTV Diagram in ConceptDraw PRO | Basic CCTV ...
- Information Communication Technology Gadgets
- CCTV Network Example | Basic CCTV System Diagram. CCTV ...
- How to Create a CCTV Diagram in ConceptDraw PRO | Camera ...
- CCTV Network Diagram Software | CCTV Network Example | Basic ...
- How To Create The Dbms System For Cctv Cameras Diagram