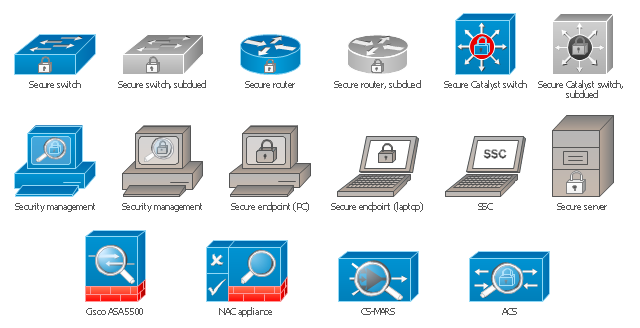
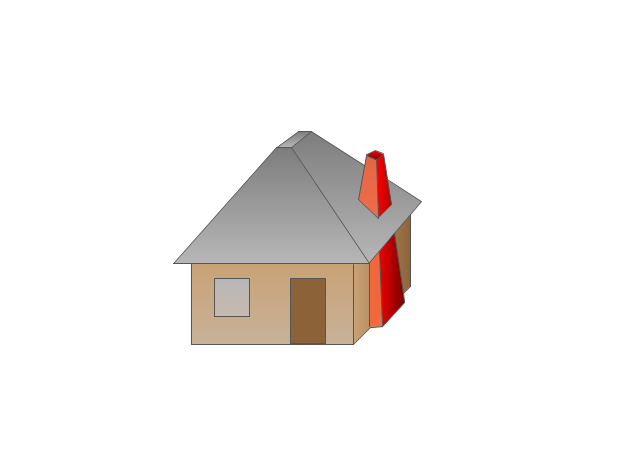
Cisco Security. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library "Cisco Security" contains 16 symbols of security devices and equipment for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.Cisco Network Design. Cisco icons, shapes, stencils, symbols and design elements
Cisco is the largest company, which specializes in the field of high technologies, develops and sells network equipment mainly for the large organizations and telecommunication companies. Cisco produces wide variety of devices and equipment, such as routers, switches, gateways, servers, network security devices (firewalls, VPN, IDs, etc.), ATM switches, cable modems and DSL equipment, access points Wi-Fi, products for IP telephony, etc. The first commercially successful multi-protocol router, which enabled for previously incompatible computers to communicate between themselves, is also developed by Cisco company. Cisco is a generally accepted standard, which uses globally recognized Cisco icons for all produced Cisco equipment. ConceptDraw DIAGRAM software extended with Cisco Network Diagrams solution from Computer and Network area contains a lot of predesigned Cisco network design elements for professional drawing Cisco network diagrams, visualization computer network topologies, equipment connections and arrangement.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
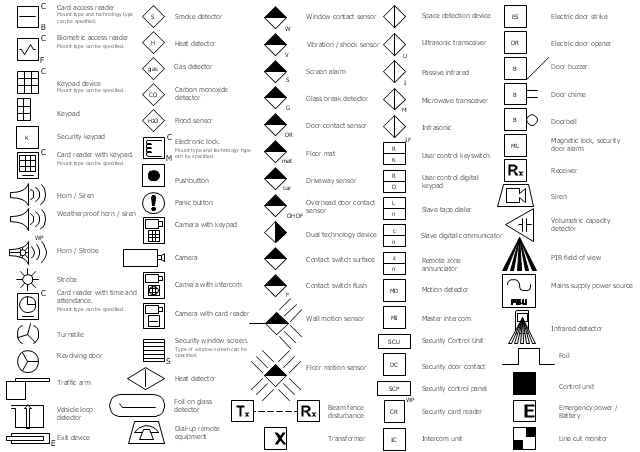
The vector stencils library Alarm and access control contains 80 symbols of digital proximity equipment, locking hardware, and access control equipment.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
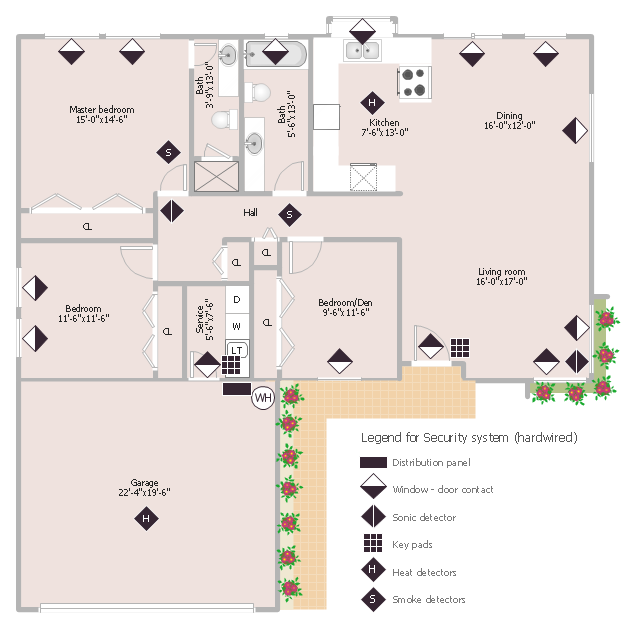
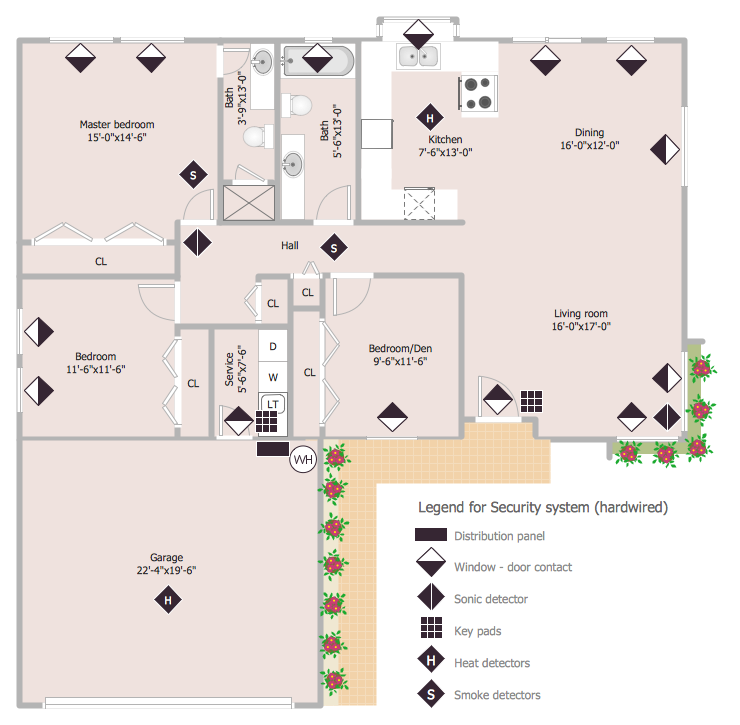
This sample was created on the base of the floor plan with security system device symbols from the website of the California State University, Sacramento. [imet.csus.edu/ imet1/ denyer/ mhs_ denyer/ drafting/ arch_ ch_ 31/ 31-28.jpg]
Legend for the security system hardware includes distribution panel, window-door contact, sonic detector, key pads, heat detectors, smoke detectors.
The example "Security system floor plan" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
Legend for the security system hardware includes distribution panel, window-door contact, sonic detector, key pads, heat detectors, smoke detectors.
The example "Security system floor plan" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
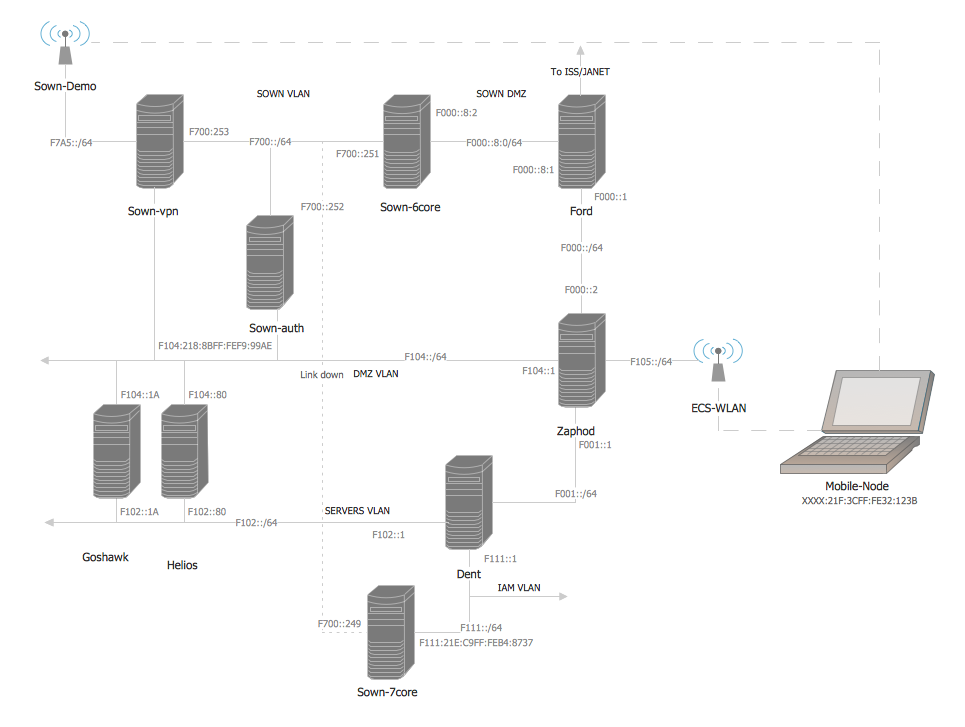
Physical Security Plan
ConceptDraw DIAGRAM diagramming and vector drawing software extended with Security and Access Plans Solution from the Building Plans Area of ConceptDraw Solution Park is a powerful software for fast and easy drawing professional looking Physical Security Plan.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
HelpDesk
How to Draw a Security and Access Floor Plan
When you are dealing with floor plans for your office or home, it's good to have a security and access plan as well. Any equipment that is responsible for certain aspects of security can be incorporated into a security and access floor plan. Any equipment that is responsible for certain aspects of security can be incorporated into a security and access floor plan. Ability to create a security and access plan in ConceptDraw DIAGRAM is contained in the Security and Access Plans solution. You can use ConceptDraw DIAGRAM to make the security and access plans for your office simple, accurate and easy-to-read.Cisco Switches and Hubs. Cisco icons, shapes, stencils and symbols
Cisco switches and hubs deliver the best performance, and often used as network solutions for small businesses, enterprises, data centers. Cisco switches are the core interconnect devices of each computer network. The numerous Cisco switches specifically designed for various applications. Network switches are separated for two types: fixed configuration and modular switches. The fixed configuration switches deprecate swapping or adding another module, and vice versa for modular switch.The vector stencils library "Logical symbols" contains 49 logical symbols for drawing logical network topology diagrams.
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
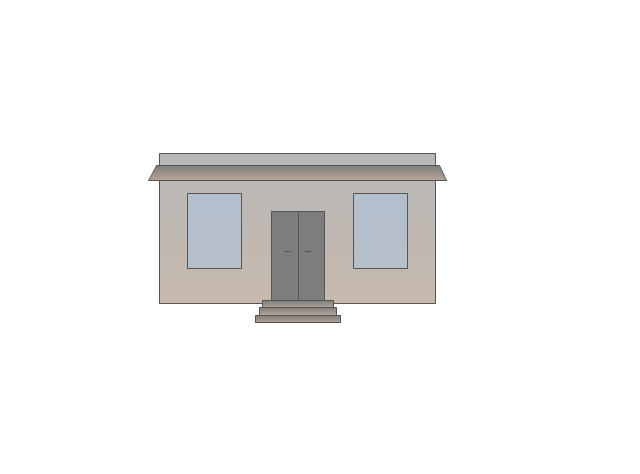
 Security and Access Plans
Security and Access Plans
The Security and Access Plans solution may be utilized in order to develop detailed equipment and cabling layout plans, blueprints, and wiring diagrams on internal and external security and access control systems, video surveillance and closed-circuit television (CCTV) systems. IT specialists, security managers, and other guards may use it to quickly design security plans and access plans, security chart, physical security plan, access chart, or access scheme on desire.
The vector stencils library "Shipping and receiving" contains 18 symbols of industrial shipping and receiving equipment.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
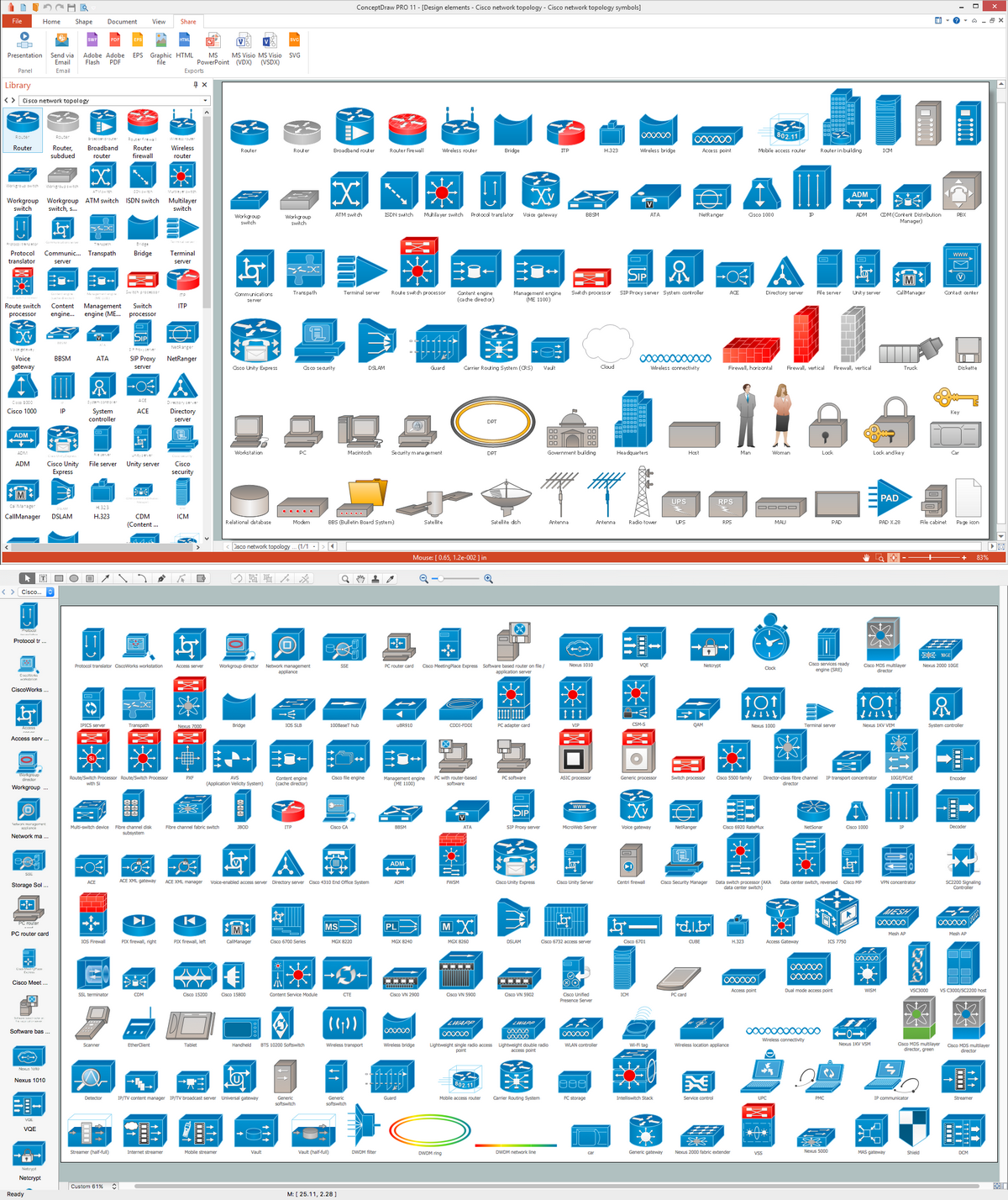
Cisco Network Topology. Cisco icons, shapes, stencils and symbols
Cisco Network Topology represents the arrangement of worldwide recognized and standardized Cisco network symbols, icons, shapes, and stencils which help visualize the schemes of computer networks. Any equipment used in Cisco networks is also named a node and network topology diagram represents the scheme of connection the used nodes. Cisco Network Diagram illustrates how the signals enter on the networked devices and how the data spread within a network from one device to another. These diagrams are useful for engineers while constructing computer networks and working with them. Cisco Network Diagrams solution included to Computer and Networks area of ConceptDraw Solution Park contains quick-start templates, professionally designed samples and examples, and numerous libraries with a lot of predesigned vector design elements, icons, and shapes of Cisco equipment, components, devices, links which provide for ConceptDraw DIAGRAM users a perfect possibility of simple and quick drawing Cisco Network Diagrams and Schematics, Network Designs and Maps of any complexity.Interior Design. Site Plan — Design Elements
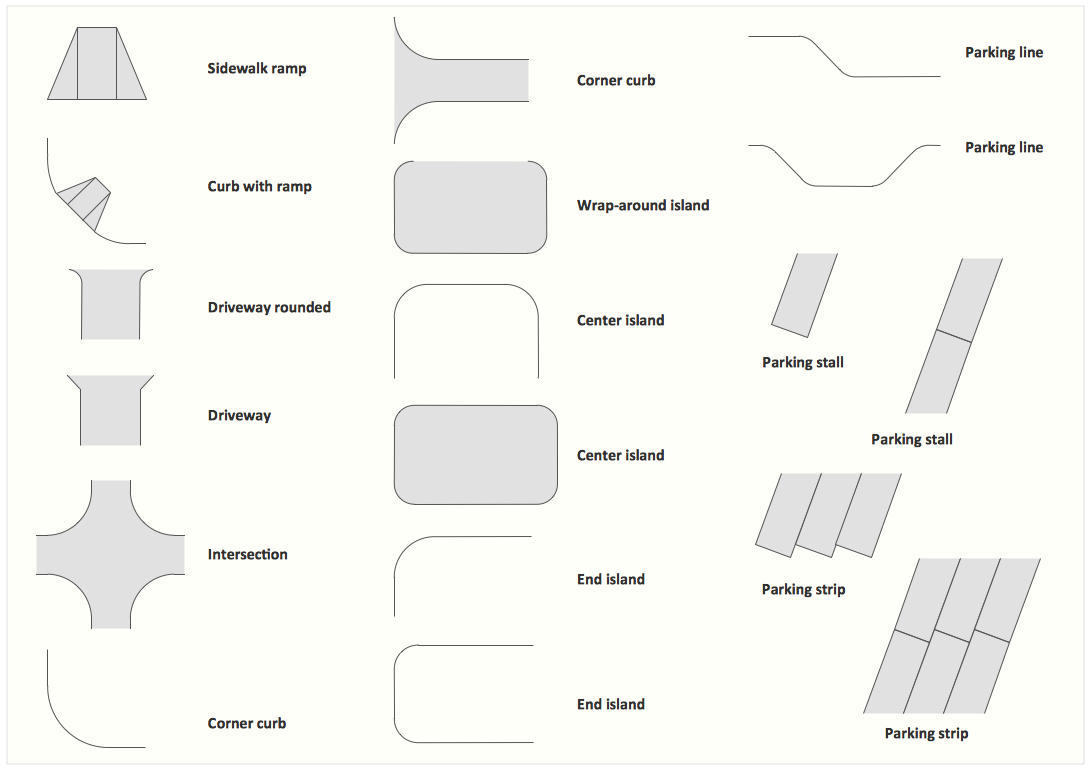
Site plans are large scale drawings that illustrate a lot of useful information, such as location of buildings on the surrounding territories, topography of the site, roads, footpaths, paved and hardstandings areas, ramps, parking areas, fencing, walls and gates, landscape elements, trees and plants, layout of external lighting and service runs, adjoining and adjacent structures, surrounding streets, and many other details. On each Site plan are also designated the scale, dimensions, site boundaries, key materials, and other additional notes. ConceptDraw DIAGRAM diagramming and interior design software extended with Site Plans solution from Building Plans area contains Parking and Roads, Site Accessories, Trees and Plants libraries with numerous collection of ready-to-use vector design elements for drawing detailed Site plans, Site design plans, Structural site plans, Landscape drawings for any locality and of any complexity without efforts. This software will be also useful for planning the parks, creation yard layouts, development residential and commercial landscape designs.The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services icons: AWS Directory Service, AWS Config, AWS CloudTrail, AWS Trusted Advisor, Amazon CloudWatch, Alarm. Use it to draw AWS architecture diagrams of your cloud infrastructure services.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers. ...
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed. ...
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility. ...
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe." [aws.amazon.com/ security/ ]
The symbols example "AWS Security, Identity and Compliance - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
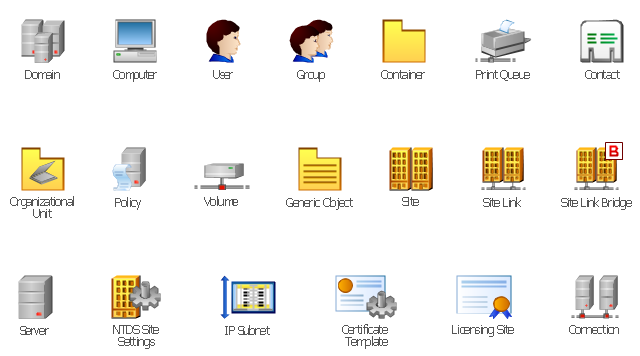
The vector stencils library "Active Directory" contains 20 symbols of Active Directory objects for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"Objects.
An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The shapes example "Design elements - Active Directory" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Objects.
An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The shapes example "Design elements - Active Directory" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The design elements library Site accessories contains 18 symbols of vehicle access control equipment (tollbooth, tollgate, parking fees payment box), a handicapped sign, outdoor lighting, and garbage receptacles.
"A site plan is an architectural plan, landscape architecture document, and a detailed engineering drawing of proposed improvements to a given lot. A site plan usually shows a building footprint, travelways, parking, drainage facilities, sanitary sewer lines, water lines, trails, lighting, and landscaping and garden elements." [Site plan. Wikipedia]
Use the Site accessories library to design plans, equipment layouts and maps of sites, parking lots, residential and commercial landscapes, parks, yards, plats, outdoor recreational facilities, and irrigation systems using ConceptDraw PRO diagramming and vector drawing software.
The design elements library Site accessories is contained in the Site Plans solution from the Building Plans area of ConceptDraw Solution Park.
"A site plan is an architectural plan, landscape architecture document, and a detailed engineering drawing of proposed improvements to a given lot. A site plan usually shows a building footprint, travelways, parking, drainage facilities, sanitary sewer lines, water lines, trails, lighting, and landscaping and garden elements." [Site plan. Wikipedia]
Use the Site accessories library to design plans, equipment layouts and maps of sites, parking lots, residential and commercial landscapes, parks, yards, plats, outdoor recreational facilities, and irrigation systems using ConceptDraw PRO diagramming and vector drawing software.
The design elements library Site accessories is contained in the Site Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library Initiation and annunciation contains 9 symbols of Fire Alarm Control Panel (FACP) or Fire Alarm Control Unit (FACU) elements, triggering devices, audible alarm systems, timers, security control equipment, and recording devices.
"A Fire Alarm Control Panel (FACP), or Fire Alarm Control Unit (FACU), is the controlling component of a Fire Alarm System. The panel receives information from environmental sensors designed to detect changes associated with fire, monitors their operational integrity and provides for automatic control of equipment, and transmission of information necessary to prepare the facility for fire based on a predetermined sequence. The panel may also supply electrical energy to operate any associated sensor, control, transmitter, or relay. There are four basic types of panels: coded panels, conventional panels, addressable panels, and multiplex systems." [Fire alarm control panel. Wikipedia]
Use the shapes library Initiation and annunciation to draw layout floor plans, communications schematics and wiring diagrams of security systems using the ConceptDraw PRO diagramming and vector drawing software.
The design elements library Initiation and annunciation is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"A Fire Alarm Control Panel (FACP), or Fire Alarm Control Unit (FACU), is the controlling component of a Fire Alarm System. The panel receives information from environmental sensors designed to detect changes associated with fire, monitors their operational integrity and provides for automatic control of equipment, and transmission of information necessary to prepare the facility for fire based on a predetermined sequence. The panel may also supply electrical energy to operate any associated sensor, control, transmitter, or relay. There are four basic types of panels: coded panels, conventional panels, addressable panels, and multiplex systems." [Fire alarm control panel. Wikipedia]
Use the shapes library Initiation and annunciation to draw layout floor plans, communications schematics and wiring diagrams of security systems using the ConceptDraw PRO diagramming and vector drawing software.
The design elements library Initiation and annunciation is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Shipping and receiving" contains 18 symbols of industrial shipping and receiving equipment.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
Use the design elements library "Shipping and receiving" to draw factory warehouse equipment layout plans, floor plans of shipping and receiving centers with equipment for hauling, transporting, and distributing manufactured goods, freight, cargo, and stock from plants and industrial facilities using the ConceptDraw PRO diagramming and vector drawing software.
"Freight transport, or shipping, is a key in the value chain in manufacturing.
While all modes of transport are used for cargo transport, there is high differentiation between the nature of the cargo transport, in which mode is chosen.
Logistics refers to the entire process of transferring products from producer to consumer, including storage, transport, transshipment, warehousing, material-handling and packaging, with associated exchange of information.
Containerization, with the standardization of ISO containers on all vehicles and at all ports, has revolutionized international and domestic trade, offering huge reduction in transshipment costs. Traditionally, all cargo had to be manually loaded and unloaded into the haul of any ship or car; containerization allows for automated handling and transfer between modes, and the standardized sizes allow for gains in economy of scale in vehicle operation." [Transport. Freight.
Wikipedia]
This shapes library "Shipping and receiving" is included in the Plant Layout Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Cisco network topology" contains 89 symbols of Cisco network devices and design elements for drawing computer network topology diagrams.
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
- Design elements - Initiation and annunciation | Security and Access ...
- Cisco Network Topology. Cisco icons, shapes, stencils and symbols ...
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Design elements - Appliances | Security system floor plan | Upright ...
- Cisco Symbols Free
- Security and Access Plans | Physical Security Plan | Cctv Legend ...
- Cisco Routers. Cisco icons, shapes, stencils and symbols | Cisco ...
- Cisco Optical. Cisco icons, shapes, stencils and symbols | Cisco ...
- Security and Access Plans | Physical Security Plan | Cctv Electrical ...
- Cisco Security . Cisco icons, shapes, stencils and symbols
- Security and Access Plans | Architect Symbols For Smoke Alarms
- Safety and Security | Cisco Network Design. Cisco icons, shapes ...
- ConceptDraw PRO Network Diagram Tool | Cisco Security . Cisco ...
- Cisco Security . Cisco icons, shapes, stencils and symbols
- Security and Access Plans | How to Draw a Security and Access ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Security System Door Contact Symbols
- Safety and Security | Security and Access Plans ... - Conceptdraw.com






-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)





-logical-symbols---vector-stencils-library.png--diagram-flowchart-example.png)


























-aws-security,-identity-and-compliance---vector-stencils-library.png--diagram-flowchart-example.png)






















-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)














-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)











-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)