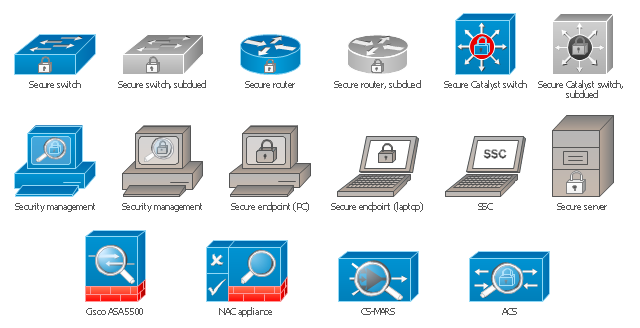
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Audit Flowcharts
Audit Flowcharts
Audit flowcharts solution extends ConceptDraw PRO software with templates, samples and library of vector stencils for drawing the audit and fiscal flow charts.
Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This financila dashboard example was drawn on the base of the Enterprise dashboard from the Mecklenburg County Government website.
[charmeck.org/ mecklenburg/ county/ CountyManagersOffice/ OMB/ dashboards/ Pages/ Enterprise.aspx]
"In management information systems, a dashboard is "an easy to read, often single page, real-time user interface, showing a graphical presentation of the current status (snapshot) and historical trends of an organization’s key performance indicators to enable instantaneous and informed decisions to be made at a glance."
For example, a manufacturing dashboard may show key performance indicators related to productivity such as number of parts manufactured, or number of failed quality inspections per hour. Similarly, a human resources dashboard may show KPIs related to staff recruitment, retention and composition, for example number of open positions, or average days or cost per recruitment.
Types of dashboards.
Dashboard of Sustainability screen shot illustrating example dashboard layout.
Digital dashboards may be laid out to track the flows inherent in the business processes that they monitor. Graphically, users may see the high-level processes and then drill down into low level data. This level of detail is often buried deep within the corporate enterprise and otherwise unavailable to the senior executives.
Three main types of digital dashboard dominate the market today: stand alone software applications, web-browser based applications, and desktop applications also known as desktop widgets. The last are driven by a widget engine.
Specialized dashboards may track all corporate functions. Examples include human resources, recruiting, sales, operations, security, information technology, project management, customer relationship management and many more departmental dashboards.
Digital dashboard projects involve business units as the driver and the information technology department as the enabler. The success of digital dashboard projects often depends on the metrics that were chosen for monitoring. Key performance indicators, balanced scorecards, and sales performance figures are some of the content appropriate on business dashboards." [Dashboard (management information systems). Wikipedia]
The example "Enterprise dashboard" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Composition Dashboard solution from the area "What is a Dashboard" of ConceptDraw Solution Park.
[charmeck.org/ mecklenburg/ county/ CountyManagersOffice/ OMB/ dashboards/ Pages/ Enterprise.aspx]
"In management information systems, a dashboard is "an easy to read, often single page, real-time user interface, showing a graphical presentation of the current status (snapshot) and historical trends of an organization’s key performance indicators to enable instantaneous and informed decisions to be made at a glance."
For example, a manufacturing dashboard may show key performance indicators related to productivity such as number of parts manufactured, or number of failed quality inspections per hour. Similarly, a human resources dashboard may show KPIs related to staff recruitment, retention and composition, for example number of open positions, or average days or cost per recruitment.
Types of dashboards.
Dashboard of Sustainability screen shot illustrating example dashboard layout.
Digital dashboards may be laid out to track the flows inherent in the business processes that they monitor. Graphically, users may see the high-level processes and then drill down into low level data. This level of detail is often buried deep within the corporate enterprise and otherwise unavailable to the senior executives.
Three main types of digital dashboard dominate the market today: stand alone software applications, web-browser based applications, and desktop applications also known as desktop widgets. The last are driven by a widget engine.
Specialized dashboards may track all corporate functions. Examples include human resources, recruiting, sales, operations, security, information technology, project management, customer relationship management and many more departmental dashboards.
Digital dashboard projects involve business units as the driver and the information technology department as the enabler. The success of digital dashboard projects often depends on the metrics that were chosen for monitoring. Key performance indicators, balanced scorecards, and sales performance figures are some of the content appropriate on business dashboards." [Dashboard (management information systems). Wikipedia]
The example "Enterprise dashboard" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Composition Dashboard solution from the area "What is a Dashboard" of ConceptDraw Solution Park.
The vector clipart library Access and security contains 17 images of access control and security system equipment.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
"In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
Locks and login credentials are two analogous mechanisms of access control. ...
The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap. Within these environments, physical key management may also be employed as a means of further managing and monitoring access to mechanically keyed areas or access to certain small assets." [Access control. Wikipedia]
Use the vector stencils library Access and security to draw illustrations and diagrams of safety and security system equipment using the ConceptDraw PRO diagramming and vector drawing software.
The clipart example "Design elements - Access and security" is included in the Safety and Security solution from the Illustration area of ConceptDraw Solution Park.
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw PRO extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 PM Presentations
PM Presentations
This solution extends ConceptDraw MINDMAP and ConceptDraw PRO software, improving the efficiency of the project management process by using the same source data to build targeted presentations.
The vector stencils library "Sales department" contains 49 company department icons.
Use these sales pictograms to draw your sales flowcharts, workflow diagrams and process charts with the ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Sales department" is included in the Sales Flowcharts solution from the Marketing area of ConceptDraw Solution Park.
Use these sales pictograms to draw your sales flowcharts, workflow diagrams and process charts with the ConceptDraw PRO diagramming and vector drawing software.
The vector stencils library "Sales department" is included in the Sales Flowcharts solution from the Marketing area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
 IDEF0 Diagrams
IDEF0 Diagrams
IDEF0 Diagrams solution extends ConceptDraw PRO software with templates, samples and library of vector stencils for drawing the IDEF0 diagrams.
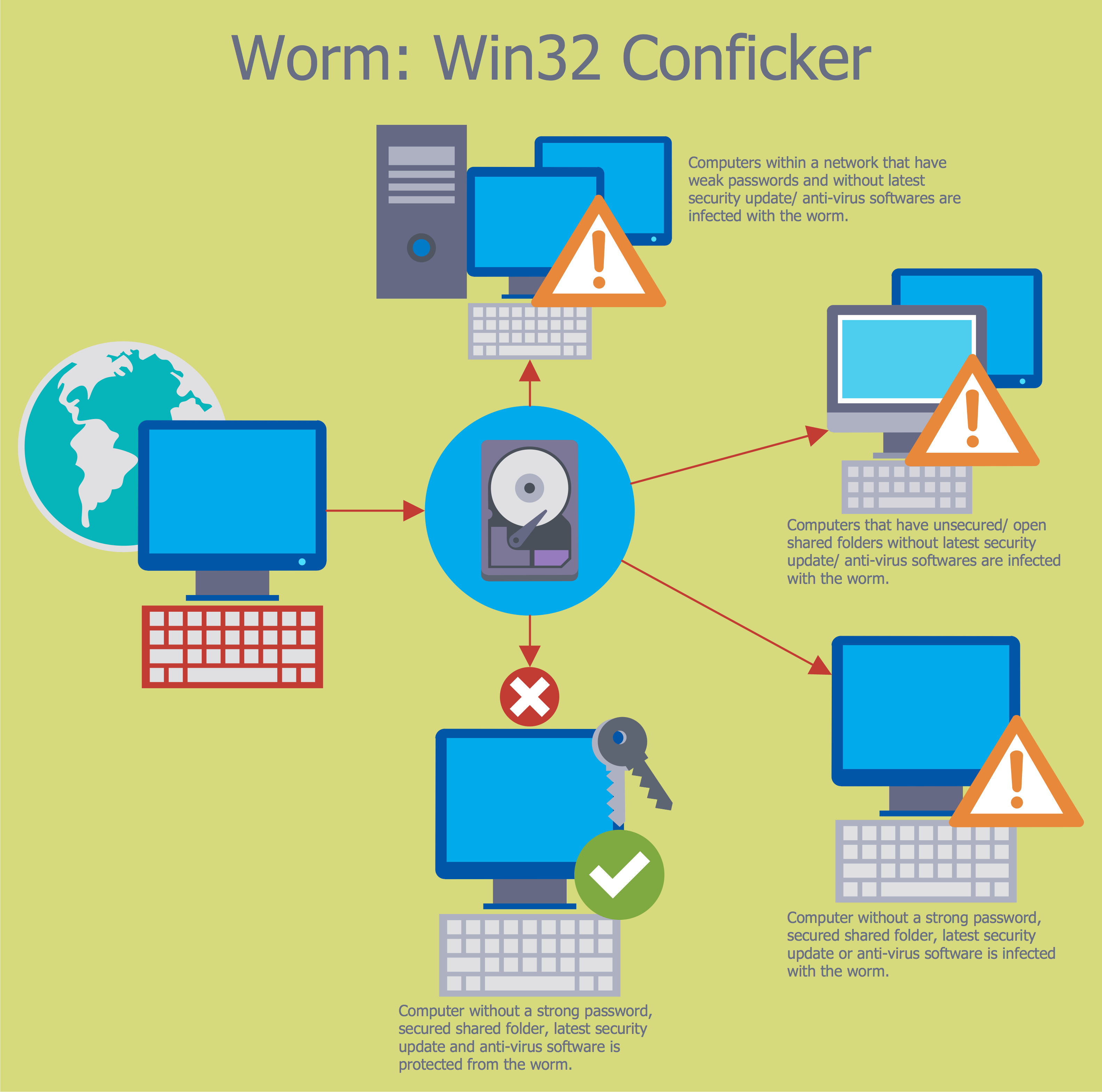
Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw PRO diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.- Cisco security - Vector stencils library
- Security Management
- Network Security . Computer and Network Examples | Cisco security ...
- How to Draw a Security and Access Floor Plan | Safety and Security ...
- Design elements - Alarm and access control | Design elements ...
- Design elements - HR department | HR Flowcharts | Human ...
- Security and Access Plans | How to Draw a Security and Access ...
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Account Flowchart. Flowchart Examples | Budgeted appropriations ...
- Project — Assigning Resources | Advanced Resource Assignment ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Safety and Security | Design elements - Access and security ...
- Pyramid Model Of Information Security System
- Conceptdraw.com: Mind Map Software, Drawing Tools | Project ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Types of Flowcharts | Design elements - Meter indicators | Control ...
- Enterprise Architecture Diagrams | Network Diagram Software ...
- Graphical Presentation Of Current Trends In Business Management
- Enterprise dashboard | HR Flowcharts | KPI Dashboard | Human ...
- Cisco Security Equipment Symbols





-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)