Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
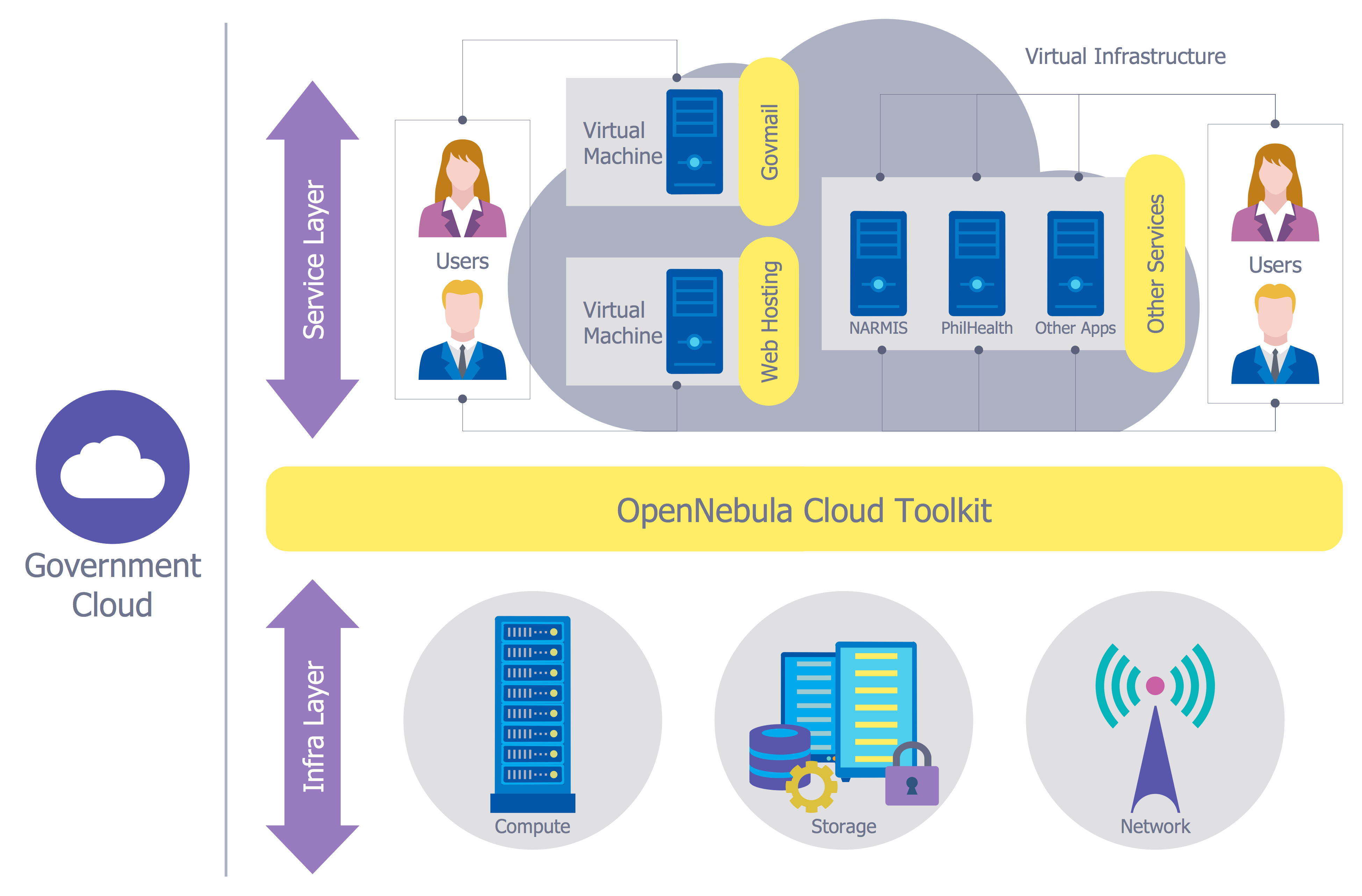
Network Security Model
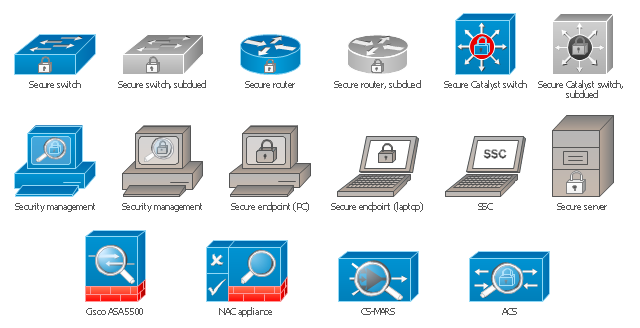
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
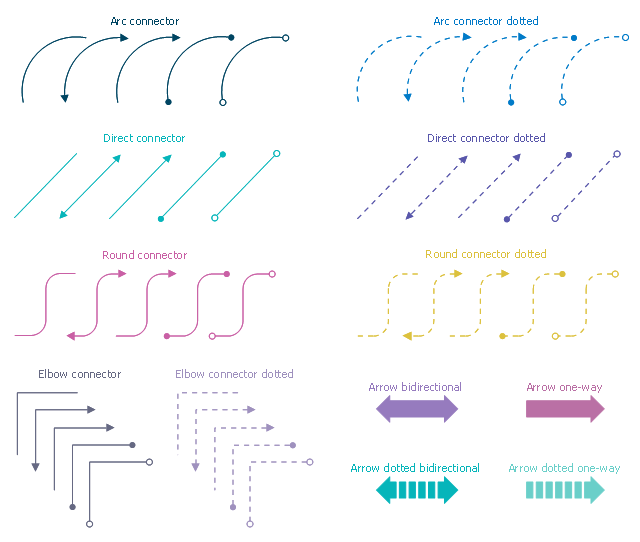
The vector stencils library "Cybersecurity connectors" contains 44 network security diagram connection lines.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Network security consists of the policies adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access." [Network security. Wikipedia]
The icon set example "Design elements - Cybersecurity connectors" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Network security consists of the policies adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access." [Network security. Wikipedia]
The icon set example "Design elements - Cybersecurity connectors" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Network Layout Floor Plans
Network Layout Floor Plans
Network Layout Floor Plan solution extends ConceptDraw PR software with samples, templates and libraries of vector stencils for drawing the computer network layout floor plans.
 Computer and Networks Area
Computer and Networks Area
The solutions from Computer and Networks Area of ConceptDraw Solution Park collect samples, templates and vector stencils libraries for drawing computer and network diagrams, schemes and technical drawings.
 Business Processes Area
Business Processes Area
Solutions of Business Processes area extend ConceptDraw PRO software with samples, templates and vector stencils libraries for drawing business process diagrams and flowcharts for business process management.
 Business Process Diagrams
Business Process Diagrams
The Business Process Diagram Solution extends ConceptDraw PRO v10 BPMN software with its RapidDraw interface, templates, samples, and libraries based on the BPMN 1.2 and BPMN 2.0 standards. This powerful solution permits you to visualize easily both simple and complex processes, as well as design business models. The Business Process Diagram solution allows one to quickly develop and document in detail any business processes at any stage of a project’s planning and implementation.
 Event-driven Process Chain (EPC) Diagrams
Event-driven Process Chain (EPC) Diagrams
Event-driven Process Chain (EPC) Diagram is a type of flowchart widely used for modeling in business engineering and reengineering, business process improvement, and analysis. EPC method was developed within the Architecture of Integrated Information Systems (ARIS) framework.
 Business Productivity Area
Business Productivity Area
Business Productivity Solutions extend ConceptDraw products with tools for making presentations, conducting meetings, preparing documents, brainstorming, or building new strategies.
- Business Productivity Area | Management pictograms - Vector ...
- Computer Network Diagrams | Call center network diagram | Cisco ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Design Example Of A Company Network
- Network Security . Computer and Network Examples | Cisco security ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Network Security . Computer and Network Examples | Cisco security ...
- Conceptdraw.com: Mind Map Software, Drawing Tools | Project ...
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Network Security Devices | Network Security | Network Security ...
- Design elements - Cybersecurity connectors | Cyber Security ...
- Network Diagram Software Enterprise Private Network | Network ...
- ConceptDraw PRO Network Diagram Tool | Cisco Security . Cisco ...
- Cisco security - Vector stencils library
- Safety and Security | Security and Access Plans ... - Conceptdraw.com
- Large Business Network Diagrams
- Project — Assigning Resources | Advanced Resource Assignment ...
- Security Management
- Enterprise private network | EPN Frame-Relay and Dial-up Network ...
- Company Logo





-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)