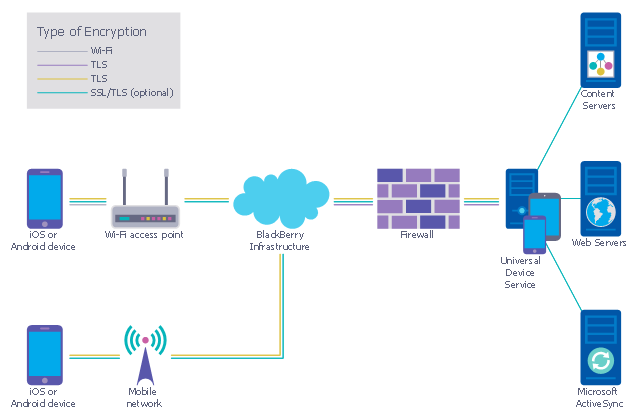
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services security, identity and compliance icons.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
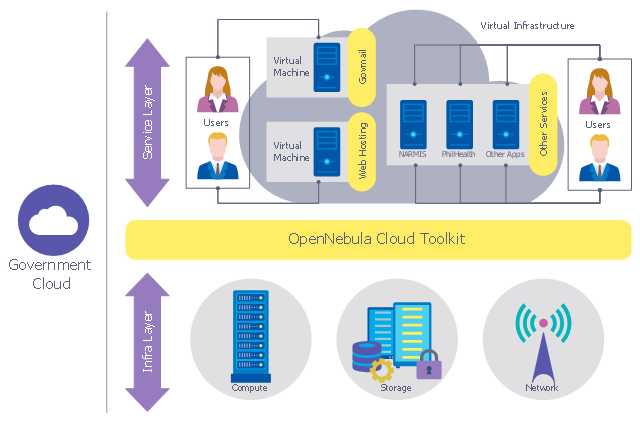
This example was designed on the base of the computer security diagram from the website of the Integrated Government Philippines (iGovPhil) Project.
"Department of Science and Technology (DOST) agencies, the Information and Communications Technology Office (DOST-ICTO) and the Advanced Science and Technology Institute (DOST-ASTI) are encouraging government institutions to adopt the use of cloud applications over traditional IT systems, as it unveiled a new online service called GovCloud or Government Cloud, which will enable government agencies to use secure online applications for their various computing requirements.
GovCloud was unveiled by Integrated Government Philippines (iGovPhil) Project at the start of a four-day celebration for Information and Communications Technology (ICT) Month 2013." [i.gov.ph/ govt-pushes-for-cloud-use-launches-govcloud/ ]
The cybersecurity diagram example "Government Cloud" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Department of Science and Technology (DOST) agencies, the Information and Communications Technology Office (DOST-ICTO) and the Advanced Science and Technology Institute (DOST-ASTI) are encouraging government institutions to adopt the use of cloud applications over traditional IT systems, as it unveiled a new online service called GovCloud or Government Cloud, which will enable government agencies to use secure online applications for their various computing requirements.
GovCloud was unveiled by Integrated Government Philippines (iGovPhil) Project at the start of a four-day celebration for Information and Communications Technology (ICT) Month 2013." [i.gov.ph/ govt-pushes-for-cloud-use-launches-govcloud/ ]
The cybersecurity diagram example "Government Cloud" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"In computer networking, cloud computing is computing that involves a large number of computers connected through a communication network such as the Internet, similar to utility computing. ...
Network-based services, which appear to be provided by real server hardware, and are in fact served up by virtual hardware, simulated by software running on one or more real machines are often called cloud computing. Such virtual servers do not physically exist and can therefore be moved around and scaled up or down on the fly without affecting the end user, somewhat like a cloud becoming larger or smaller without being a physical object. ...
Typically, the seller has actual energy-consuming servers which host products and services from a remote location, so end-users don't have to; they can simply log on to the network without installing anything. The major models of cloud computing service are known as software as a service, platform as a service, and infrastructure as a service. These cloud services may be offered in a public, private or hybrid network. Google, Amazon,leadsquared.com, Oracle Cloud, Salesforce, Zoho, Access2MyPC, and Microsoft Azure are some well-known cloud vendors." [Cloud computing. Wikipedia]
The AWS architecture diagram example "2-Tier Auto-scalable Web Application Architecture in 1 AZ" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network-based services, which appear to be provided by real server hardware, and are in fact served up by virtual hardware, simulated by software running on one or more real machines are often called cloud computing. Such virtual servers do not physically exist and can therefore be moved around and scaled up or down on the fly without affecting the end user, somewhat like a cloud becoming larger or smaller without being a physical object. ...
Typically, the seller has actual energy-consuming servers which host products and services from a remote location, so end-users don't have to; they can simply log on to the network without installing anything. The major models of cloud computing service are known as software as a service, platform as a service, and infrastructure as a service. These cloud services may be offered in a public, private or hybrid network. Google, Amazon,leadsquared.com, Oracle Cloud, Salesforce, Zoho, Access2MyPC, and Microsoft Azure are some well-known cloud vendors." [Cloud computing. Wikipedia]
The AWS architecture diagram example "2-Tier Auto-scalable Web Application Architecture in 1 AZ" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This computer security diagram example was designed on the base of the diagram from the website of the Centers for Disease Control and Prevention (CDC).
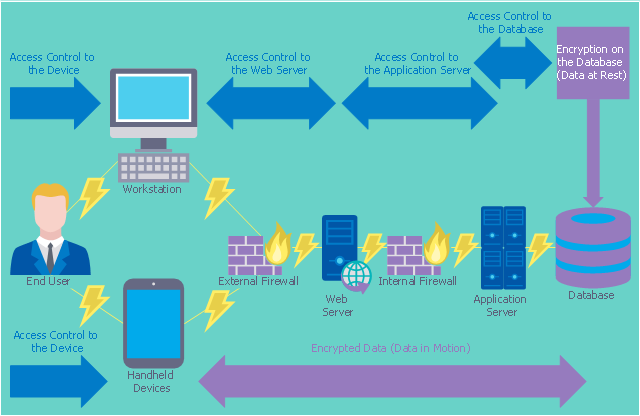
"Encryption and Cryptography
Encryption converts plain text into ciphertext, and decryption converts ciphertext back into plain text. Ciphertext looks like random characters, but is actually the result of the application of a key to the plain text. A key is usually a mathematical algorithm known only to the sender and the intended recipient of the message.
A cryptosystem is a system for encrypting and decrypting data. A strong cryptosystem has many possible keys, so a third party would be unlikely to find the correct key by trying all possible keys. A strong cryptosystem also produces ciphertext that appears random to all standard statistical tests and resists all known methods for breaking codes.
Access Control
Before implementing encryption, an organization needs to ensure access to the database is limited to authorized users. Access controls that should be addressed include rules for creating users, users’ privileges to access objects, and users’ permissions to perform commands and various tasks.
The following diagram illustrates how access control and encryption work together to secure data" [cdc.gov/ cancer/ npcr/ tools/ security/ encryption2.htm]
The cybersecurity diagram example "Access control and encryption " was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Encryption and Cryptography
Encryption converts plain text into ciphertext, and decryption converts ciphertext back into plain text. Ciphertext looks like random characters, but is actually the result of the application of a key to the plain text. A key is usually a mathematical algorithm known only to the sender and the intended recipient of the message.
A cryptosystem is a system for encrypting and decrypting data. A strong cryptosystem has many possible keys, so a third party would be unlikely to find the correct key by trying all possible keys. A strong cryptosystem also produces ciphertext that appears random to all standard statistical tests and resists all known methods for breaking codes.
Access Control
Before implementing encryption, an organization needs to ensure access to the database is limited to authorized users. Access controls that should be addressed include rules for creating users, users’ privileges to access objects, and users’ permissions to perform commands and various tasks.
The following diagram illustrates how access control and encryption work together to secure data" [cdc.gov/ cancer/ npcr/ tools/ security/ encryption2.htm]
The cybersecurity diagram example "Access control and encryption " was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 iPhone User Interface
iPhone User Interface
iPhone User Interface solution extends ConceptDraw PRO v10 software with templates, samples and libraries with large quantity of vector stencils of graphical user interface elements, Apps icons, UI patterns for designing and prototyping of the iOS applic
 AWS Architecture Diagrams
AWS Architecture Diagrams
AWS Architecture Diagrams with powerful drawing tools and numerous predesigned Amazon icons and AWS simple icons is the best for creation the AWS Architecture Diagrams, describing the use of Amazon Web Services or Amazon Cloud Services, their application for development and implementation the systems running on the AWS infrastructure. The multifarious samples give you the good understanding of AWS platform, its structure, services, resources and features, wide opportunities, advantages and benefits from their use; solution’s templates are essential and helpful when designing, description and implementing the AWS infrastructure based systems. Use them in technical documentation, advertising and marketing materials, in specifications, presentation slides, whitepapers, datasheets, posters, etc.
- Conceptdraw.com: Mind Map Software, Drawing Tools | Project ...
- Recommended network architecture for BlackBerry SWS | Network ...
- Access control and encryption
- Make A Diagram Of Computer Security
- Network Security Diagrams | Network Security Devices ...
- Mobile app security | Network Security Diagrams | IT Security ...
- Government Cloud | Network Security Diagrams | Network Security ...
- AWS Architecture Diagrams | Amazon Web Services Diagrams ...
- Login and registration processing - EPC diagram | Flowchart | Cloud ...
- Global vehicular network diagram template | Hotel Network ...
- 2-Tier Auto-scalable Web Application Architecture in 1 AZ (v2.0) | 3 ...
- 2-Tier Auto-scalable Web Application Architecture in 1 AZ (v2.0 ...
- Cisco Network Templates | Computer Network Diagrams | Logical ...
- 3-Tier Auto-scalable Web Application Architecture | 2-Tier Auto ...
- Cyber Security Degrees | Cisco Security . Cisco icons, shapes ...
- Security and Access Plans | How to Draw a Security and Access ...
- Security and Access Plans | How to Draw a Security and Access ...
- AWS Application Services - Vector stencils library | Design elements ...
- Account Flowchart. Flowchart Examples | Budgeted appropriations ...
- Application server rack diagram | Rack Diagrams | Server ...
.png--diagram-flowchart-example.png)