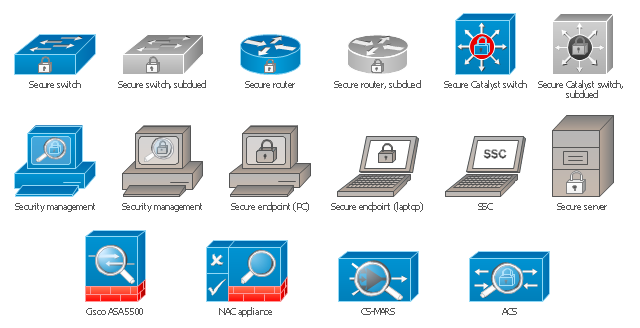
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
Cisco Security. Cisco icons, shapes, stencils and symbols
The ConceptDraw vector stencils library "Cisco Security" contains 16 symbols of security devices and equipment for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco products additional" contains 141 symbols of computer network devices and equipment for drawing Cisco network diagrams.
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
 Security and Access Plans
Security and Access Plans
The Security and Access Plans solution may be utilized in order to develop detailed equipment and cabling layout plans, blueprints, and wiring diagrams on internal and external security and access control systems, video surveillance and closed-circuit television (CCTV) systems. IT specialists, security managers, and other guards may use it to quickly design security plans and access plans, security chart, physical security plan, access chart, or access scheme on desire.
The vector stencils library "Logical symbols" contains 49 logical symbols for drawing logical network topology diagrams.
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco network topology" contains 89 symbols of Cisco network devices and design elements for drawing computer network topology diagrams.
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco network topology" contains 89 symbols of Cisco network devices and design elements for drawing computer network topology diagrams.
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"There are two basic categories of network topologies:
(1) Physical topologies,
(2) Logical topologies.
The shape of the cabling layout used to link devices is called the physical topology of the network. This refers to the layout of cabling, the locations of nodes, and the interconnections between the nodes and the cabling. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits.
The logical topology in contrast, is the way that the signals act on the network media, or the way that the data passes through the network from one device to the next without regard to the physical interconnection of the devices." [Network topology. Wikipedia]
The symbols example "Cisco network topology - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "AWS Security, Identity and Compliance" contains 25 Amazon Web Services security, identity and compliance icons.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Total Quality Management TQM Diagrams
Total Quality Management TQM Diagrams
Total Quality Management Diagrams solution extends ConceptDraw DIAGRAM software with samples, templates and vector stencils library for drawing the TQM flowcharts.
 PM Dashboards
PM Dashboards
The PM Dashboards solution extends the management boundaries of ConceptDraw DIAGRAM and ConceptDraw PROJECT products with an ability to demonstrate changes to the budget status, to show the project progress toward its objectives, to display clearly the identified key performance indicator (KPI) or the set of key performance indicators for any project. This solution provides you with examples and ability to generate three types of visual dashboards reports based on your project data Project Dashboard, Tactical Dashboard, and Radar Chart. By dynamically charting the project’s key performance indicators that are collected on one ConceptDraw DIAGRAM document page, all project participants, project managers, team members, team leaders, stakeholders, and the entire organizations, for which this solution is intended, have access to the daily status of projects they are involved in.
 Business Diagrams Package
Business Diagrams Package
Business Diagrams Package is a large set of comprehensive graphical solutions from the ConceptDraw Solution Park, which are powerful in solving the business, marketing and quality tasks in completely different fields, such as finance, education, health food and cooking, HR, and many others. The tools of this package's solutions are a powerful assistant in drawing all diversity of Financial and Marketing infographics, Business process workflow diagrams, Organizational charts, Education infographics, Quality diagrams, Health food diagrams, HR flowcharts, as well as different graphics and charts, which depict the values of key business indicators, their dependencies, give the full understanding of a situation within a company and on the market.
- Security management
- Er Diagram For Security Management System
- Cisco security - Vector stencils library
- Cisco security - Vector stencils library
- Cisco security - Vector stencils library
- Cisco security - Vector stencils library
- Cisco Security Manager
- Database Security Management System Er Diagram
- Cisco security - Vector stencils library
- Cisco security
- Network Security Diagrams | Network Security Model | Cisco security ...
- Cisco security - Vector stencils library | Cisco security - Vector ...
- Cisco security
- Cisco security - Vector stencils library | Access and security - Vector ...
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Cisco network topology - Vector stencils library
- Design elements - Cisco security
- Activity Diagram For Attendance Management System
- Cisco security - Vector stencils library | Design elements - Cisco ...





-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)






-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)






-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)

-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)

















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)




-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)







-logical-symbols---vector-stencils-library.png--diagram-flowchart-example.png)

























-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)














-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)











-cisco-network-topology---vector-stencils-library.png--diagram-flowchart-example.png)