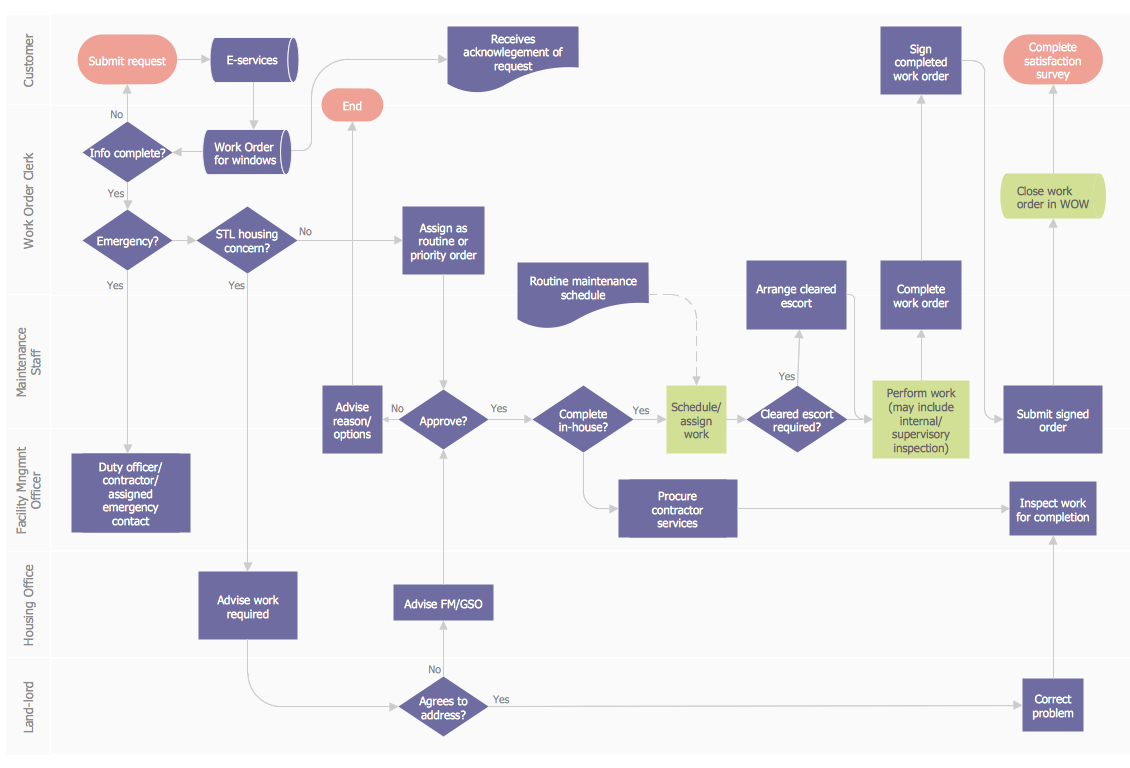
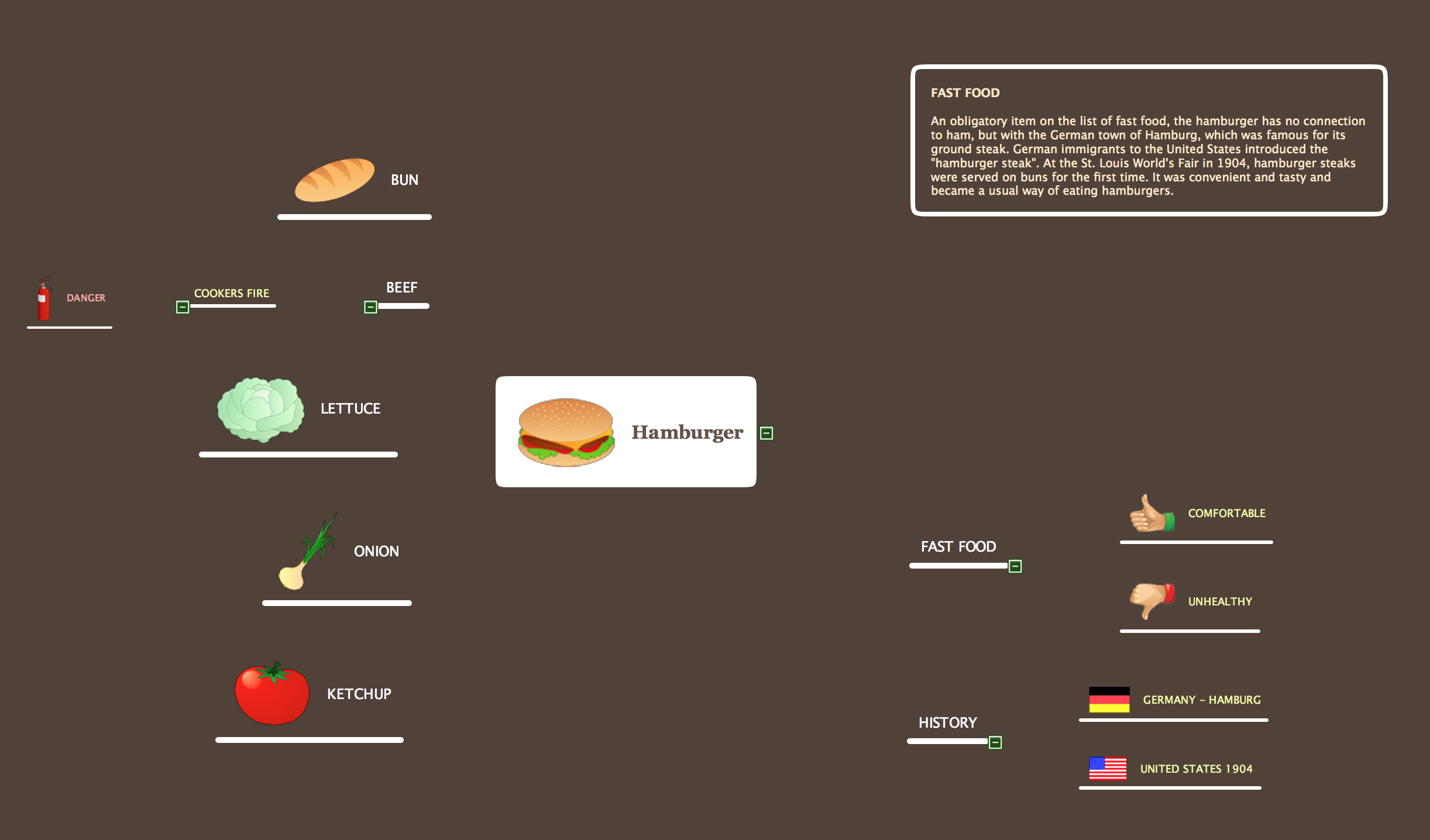
Work Order Process Flowchart. Business Process Mapping Examples
The business process is a set of actions or tasks which are undertaken by an organization for production some goods or services, they are then offered for the customers and are ordered by them. Process Flowcharts and Order Process Flowcharts are sufficiently prevalent, well known and actively used in variety of fields of life, business and science. They are constructed using the common standardized symbols, thus are clear and understandable for all. They help effectively represent the processes, determine the order in which the process activities happen, document the order processes, and also effectively analyze the processes with a goal to increase their efficiency. Create your own Process Flowcharts, Order Process Flowcharts, Cross-Functional Flow Charts representing the order processing steps using powerful drawing tools of ConceptDraw DIAGRAM software and variety of predesigned vector objects from the libraries of Business Process Mapping Solution from Business Processes area of ConceptDraw Solution Park.Mind Map Food
ConceptDraw MINDMAP from ConceptDraw Office suite is versatile, powerful and at the same time easy-to-use tool for brainstorming, project planning, organizing ideas and data, meeting management, note taking, etc. It lets quickly create the Mind Maps that intuitively illustrate the thought process and offers for using wide variety of document styles and formats. ConceptDraw MINDMAP delivers its users the perfect possibility of exporting constructed Mind Maps, of easy making MS PowerPoint presentations from the Mind Maps, of publishing the images and maps to Twitter and creating the illustrated tweet story. ConceptDraw MINDMAP application offers the powerful tools for designing the maps for any thematic, including the cooking. You can visually represent any recipe, the needed ingredients and steps of preparation some dishes, tell about the recipe's history, compose the menu for day, week, month, depict the basic information about any cuisine in the world. It is convenient to use the possibility of easy making different Mind Maps when making the menu for restaurants, cafes, fast food factories, etc.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
- Process Flowchart | Mine Worker Mind Mapping Image
- Mind Map Food | How to exchange data files of major mind mapping ...
- How to Create a PowerPoint Presentation from a SWOT Analysis ...
- Resources and energy - Vector stencils library | Design elements ...
- Resources and energy - Vector stencils library | Network Security ...
- Process Flowchart | Basic Flowchart Symbols and Meaning ...
- How to Purchase ConceptDraw Products for Academic/Nonprofit ...
- Energy Pyramid Diagram | Resources and energy - Vector stencils ...
- Porter's Value Chain | Block diagram - Porter's five forces model ...
- Manufacturing and Maintenance | Manufacturing and Maintenance ...
- Human Resource Development | Electronic human resources (E-HR ...
- Energy resources diagram | Resources and energy - Vector stencils ...
- People - Vector stencils library | Professions - Vector stencils library ...
- Maintenance - Vector stencils library | Manufacturing and ...