The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
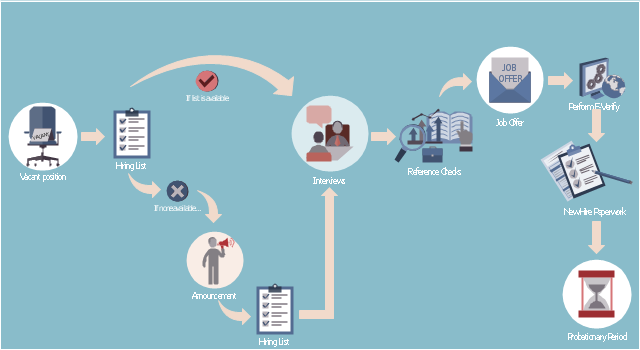
This HR infographics example was designed on the base of flowchart "Hiring Process" from the website of the Idaho Division of Human Resources.
"... hiring process flowchart outlining the steps to fill a vacant position." [dhr.idaho.gov/ hiringprocess.html]
"What is a hiring list and what are they for?
A hiring list consists of applicants who completed and passed the examination for a vacant classified position.
The applicants are ranked on the hiring list in order from highest to lowest score." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Hiring%20 List%20 Guidance.pdf]
"Announcements.
Announcing a vacant position benefits the agency by allowing a wide array of applicants the opportunity to compete for job openings, resulting in a more qualified employee. The State Merit System requires all appointments, promotions and separations in the classified service to be based on competence, valid job requirements, and individual performance." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Announcement.pdf]
"Conducting A Lawful Employment Interview.
Interviewing prospective employees is one of the most important activities employers do. The employer’s objective of an interview is to determine whether an applicant is suitable for an available position. The interview provides the employer an opportunity to obtain in-depth information about a job applicant’s skills, work history, and employment background for this purpose." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Conducting%20 a%20 Lawful%20 Employment%20 Interview.pdf]
"Reference Checks.
References should be checked after a successful interview with a candidate, but before you offer them the position. If after interviewing there are several candidates that are qualified for the position, reference checks are also a way to further distinguish who might best fit within your agency." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Reference%20 Checks.pdf]
"Making the job offer.
Before offering the position to your selected candidate, be sure to speak with your HR and fiscal staff. They may have some suggestions for negotiating the starting salary, etc.
Job Offer Letter.
... A job offer letter should be given to the newly hired employee after you have verbally negotiated the terms of employment. This letter confirms the conditions of employment the selected candidate has accepted and gives them information for their first day." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Making%20 the%20 job%20 offer.pdf]
"E-verify.
To ensure compliance with the Governor’s Executive Order 2009-10, all
State Agencies are encouraged to participate in E-verify.
E-verify is an internet based system that allows an employer, using information reported on an employee’s Form I-9, to determine the eligibility of that employee to work in the United States.
The E-Verify system is operated by the U.S. Department of Homeland Security in partnership with the Social Security Administration and its use is free of charge to employers." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ EVerify%20 Statement.pdf]
"New Hire Paperwork.
There are several important forms for the new employee to fill out." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ New%20 Hire%20 Paperwork.pdf]
"Probationary Period.
All appointments and promotions into classified positions require a probationary period of 1,040 hours
except for peace officers who must serve 2,080 hours.
The probationary period is a working test period to evaluate the work performance of the employee and to determine their suitability for the position." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Probationary%20 Period%20 for%20 Hiring%20 Process.pdf]
The HR infographics example "Hiring process workflow" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the HR Flowcharts solution from the Management area of ConceptDraw Solution Park.
"... hiring process flowchart outlining the steps to fill a vacant position." [dhr.idaho.gov/ hiringprocess.html]
"What is a hiring list and what are they for?
A hiring list consists of applicants who completed and passed the examination for a vacant classified position.
The applicants are ranked on the hiring list in order from highest to lowest score." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Hiring%20 List%20 Guidance.pdf]
"Announcements.
Announcing a vacant position benefits the agency by allowing a wide array of applicants the opportunity to compete for job openings, resulting in a more qualified employee. The State Merit System requires all appointments, promotions and separations in the classified service to be based on competence, valid job requirements, and individual performance." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Announcement.pdf]
"Conducting A Lawful Employment Interview.
Interviewing prospective employees is one of the most important activities employers do. The employer’s objective of an interview is to determine whether an applicant is suitable for an available position. The interview provides the employer an opportunity to obtain in-depth information about a job applicant’s skills, work history, and employment background for this purpose." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Conducting%20 a%20 Lawful%20 Employment%20 Interview.pdf]
"Reference Checks.
References should be checked after a successful interview with a candidate, but before you offer them the position. If after interviewing there are several candidates that are qualified for the position, reference checks are also a way to further distinguish who might best fit within your agency." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Reference%20 Checks.pdf]
"Making the job offer.
Before offering the position to your selected candidate, be sure to speak with your HR and fiscal staff. They may have some suggestions for negotiating the starting salary, etc.
Job Offer Letter.
... A job offer letter should be given to the newly hired employee after you have verbally negotiated the terms of employment. This letter confirms the conditions of employment the selected candidate has accepted and gives them information for their first day." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Making%20 the%20 job%20 offer.pdf]
"E-verify.
To ensure compliance with the Governor’s Executive Order 2009-10, all
State Agencies are encouraged to participate in E-verify.
E-verify is an internet based system that allows an employer, using information reported on an employee’s Form I-9, to determine the eligibility of that employee to work in the United States.
The E-Verify system is operated by the U.S. Department of Homeland Security in partnership with the Social Security Administration and its use is free of charge to employers." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ EVerify%20 Statement.pdf]
"New Hire Paperwork.
There are several important forms for the new employee to fill out." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ New%20 Hire%20 Paperwork.pdf]
"Probationary Period.
All appointments and promotions into classified positions require a probationary period of 1,040 hours
except for peace officers who must serve 2,080 hours.
The probationary period is a working test period to evaluate the work performance of the employee and to determine their suitability for the position." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Probationary%20 Period%20 for%20 Hiring%20 Process.pdf]
The HR infographics example "Hiring process workflow" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the HR Flowcharts solution from the Management area of ConceptDraw Solution Park.
 Vehicular Networking
Vehicular Networking
Vehicular Networking solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for drawing the vehicular computer communication network diagrams and schemes.
- Cisco security - Vector stencils library
- Safety and Security | UML object diagram - Safety inspection | Fire ...
- How to Draw a Security and Access Floor Plan | Safety and Security ...
- Network Security . Computer and Network Examples | Cisco security ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Account Flowchart. Flowchart Examples | Budgeted appropriations ...
- Security and Access Plans | How to Draw a Security and Access ...
- Security Management
- Project — Assigning Resources | Advanced Resource Assignment ...
- Business process diagram BPMN 1.2 - Hiring process | Recruitment ...
- Classification Of Information System Flow Chart
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Flow Chart Symbols | Hiring process workflow | How To Create a ...
- Design elements - HR department | HR Flowcharts | Human ...
- Hiring process workflow | Recruitment | HR Flowcharts | Employee ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Cisco Security Equipment Symbols
- Human Resources | Electronic human resources (E-HR) | Types of ...
- Hiring process workflow | How to Create a HR Process Flowchart ...
- Hiring process workflow | Flow chart Example. Warehouse Flowchart ...





-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)