"Authentication ... is the act of confirming the truth of an attribute of a single piece of data (datum) or entity. In contrast with Identification which refers to the act of stating or otherwise indicating a claim purportedly attesting to a person or thing's identity, Authentication is the process of actually confirming that identity. It might involve confirming the identity of a person by validating their identity documents, verifying the validity of a website with a digital certificate, tracing the age of an artifact by carbon dating, or ensuring that a product is what its packaging and labeling claim to be. In other words, Authentication often involves verifying the validity of at least one form of identification." [Authentication. Wikipedia]
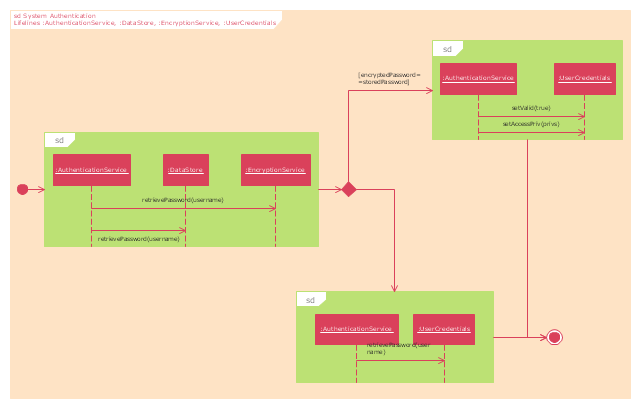
The UML interaction overview diagram example "System authentication" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
The UML interaction overview diagram example "System authentication" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
"There are two definitions for wireless LAN roaming:
Internal Roaming (1): The Mobile Station (MS) moves from one access point (AP) to another AP within a home network because the signal strength is too weak. An authentication server (RADIUS) performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A Mobile Station roaming from one access point to another often interrupts the flow of data among the Mobile Station and an application connected to the network. The Mobile Station, for instance, periodically monitors the presence of alternative access points (ones that will provide a better connection). At some point, based on proprietary mechanisms, the Mobile Station decides to re-associate with an access point having a stronger wireless signal. The Mobile Station, however, may lose a connection with an access point before associating with another access point. In order to provide reliable connections with applications, the Mobile Station must generally include software that provides session persistence.
External Roaming (2): The MS (client) moves into a WLAN of another Wireless Internet Service Provider (WISP) and takes their services (Hotspot). The user can independently of his home network use another foreign network, if this is open for visitors. There must be special authentication and billing systems for mobile services in a foreign network." [Wireless LAN. Wikipedia]
This Cisco roaming wireless local area network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Internal Roaming (1): The Mobile Station (MS) moves from one access point (AP) to another AP within a home network because the signal strength is too weak. An authentication server (RADIUS) performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A Mobile Station roaming from one access point to another often interrupts the flow of data among the Mobile Station and an application connected to the network. The Mobile Station, for instance, periodically monitors the presence of alternative access points (ones that will provide a better connection). At some point, based on proprietary mechanisms, the Mobile Station decides to re-associate with an access point having a stronger wireless signal. The Mobile Station, however, may lose a connection with an access point before associating with another access point. In order to provide reliable connections with applications, the Mobile Station must generally include software that provides session persistence.
External Roaming (2): The MS (client) moves into a WLAN of another Wireless Internet Service Provider (WISP) and takes their services (Hotspot). The user can independently of his home network use another foreign network, if this is open for visitors. There must be special authentication and billing systems for mobile services in a foreign network." [Wireless LAN. Wikipedia]
This Cisco roaming wireless local area network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
This interactive voice response (IVR) flowchart sample shows the store reporting process flow.
"Call centers use IVR systems to identify and segment callers. The ability to identify customers allows services to be tailored according to the customer profile. The caller can be given the option to wait in the queue, choose an automated service, or request a callback. The system may obtain caller line identification (CLI) data from the network to help identify or authenticate the caller. Additional caller authentication data could include account number, personal information, password and biometrics (such as voice print).
When an IVR system answers multiple phone numbers the use of DNIS ensures that the correct application and language is executed. A single large IVR system can handle calls for thousands of applications, each with its own phone numbers and script.
IVR also enables customer prioritization. In a system wherein individual customers may have a different status the service will automatically prioritize the individual's call and move customers to the front of a specific queue. Prioritization could also be based on the DNIS and call reason." [Interactive voice response. Wikipedia]
The IVR diagram example "Store reporting flowchart" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Call centers use IVR systems to identify and segment callers. The ability to identify customers allows services to be tailored according to the customer profile. The caller can be given the option to wait in the queue, choose an automated service, or request a callback. The system may obtain caller line identification (CLI) data from the network to help identify or authenticate the caller. Additional caller authentication data could include account number, personal information, password and biometrics (such as voice print).
When an IVR system answers multiple phone numbers the use of DNIS ensures that the correct application and language is executed. A single large IVR system can handle calls for thousands of applications, each with its own phone numbers and script.
IVR also enables customer prioritization. In a system wherein individual customers may have a different status the service will automatically prioritize the individual's call and move customers to the front of a specific queue. Prioritization could also be based on the DNIS and call reason." [Interactive voice response. Wikipedia]
The IVR diagram example "Store reporting flowchart" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Azure Architecture
Azure Architecture
Azure Architecture solution bundles into one handy tool everything you need to create effective Azure Architecture diagrams. It adds the extra value to versatile ConceptDraw PRO software and extends the users capabilities with comprehensive collection of Microsoft Azure themed graphics, logos, preset templates, wide array of predesigned vector symbols that covers the subjects such as Azure management, Azure storage, and Azure services, amongst others, and allow you to illustrate Azure Architecture diagrams at any degree of complexity, to present visually your Azure cloud system architecture with professional style, to design Azure cloud topology, to document Windows Azure Architecture and Azure Cloud System Architecture, to visualize the great abilities and work of Microsoft Azure Cloud System and Azure services.
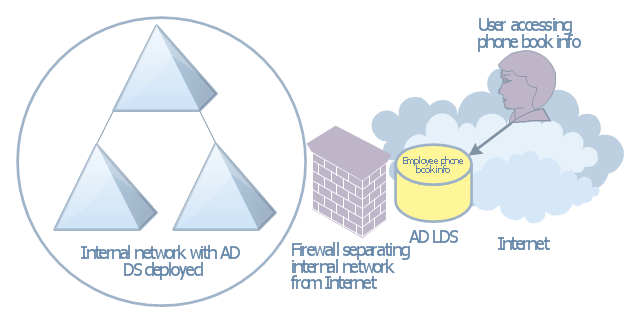
This AD diagram example was created based on the picture "AD LDS as a phone book service" from the book "Active Directory for Dummies".
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "AWS Mobile Services and Game Development" contains 7 icons: AWS Cognito icon, AWS Mobile Analytics icon, Amazon SNS icons, AWS Device Farm icon, AWS Mobile Hub icon, Amazon GameLift icon.
Use it to draw Amazon Web Services architecture diagrams with ConceptDraw PRO diagramming and vector drawing software.
"AWS Mobile Hub lets you easily add and configure features for your mobile apps, including user authentication, data storage, backend logic, push notifications, content delivery, and analytics. After you build your app, AWS Mobile Hub gives you easy access to testing on real devices, as well as analytics dashboards to track usage of your app – all from a single, integrated console." [aws.amazon.com/ mobile/ ]
"Amazon Web Services offers a comprehensive suite of products and services for video game developers across every major platform: mobile, console, PC and online. From AAA console and PC games, to educational and serious games, AWS provides the back end servers and hosting services for your game studio." [aws.amazon.com/ gaming/ ]
The AWS icons example "Design elements - AWS Mobile Services and Game Development" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to draw Amazon Web Services architecture diagrams with ConceptDraw PRO diagramming and vector drawing software.
"AWS Mobile Hub lets you easily add and configure features for your mobile apps, including user authentication, data storage, backend logic, push notifications, content delivery, and analytics. After you build your app, AWS Mobile Hub gives you easy access to testing on real devices, as well as analytics dashboards to track usage of your app – all from a single, integrated console." [aws.amazon.com/ mobile/ ]
"Amazon Web Services offers a comprehensive suite of products and services for video game developers across every major platform: mobile, console, PC and online. From AAA console and PC games, to educational and serious games, AWS provides the back end servers and hosting services for your game studio." [aws.amazon.com/ gaming/ ]
The AWS icons example "Design elements - AWS Mobile Services and Game Development" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
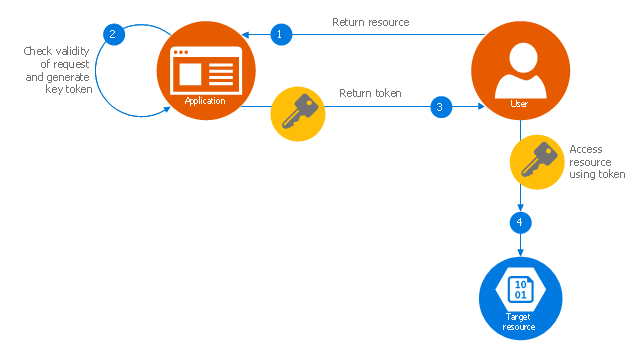
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Valet Key Pattern" from the Microsoft Developer Network (MSDN) website.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
- System Authentication
- Activity Diagram For Authentication Mobile Devices
- Authentication Drawing
- Flowchart Of Computer Authentication
- Component Diagrams For Graphical Password Authentication System
- Active Directory Authentication Flowchart
- Example For Small Data Flow Diagram
- Usecase Diagram For Authentication For Social Websites
- UML activity diagram - Cash withdrawal from ATM | ATM UML ...
- Roaming wireless local area network diagram | Wisp Setup Diagram
- Roaming wireless local area network diagram | Wireless Weak Signal
- Software Defined Networking System Overview | Diagramming ...
- UML Deployment Diagram Example - ATM System UML diagrams ...
- Roaming wireless local area network diagram | Wireless broadband ...
- Basic Flowchart Symbols and Meaning | Interaction Overview ...
- How to Create an Active Directory Diagram in ConceptDraw PRO ...
- Roaming wireless local area network diagram | Cisco Network ...
- Internet Connectivity. Computer and Network Examples | Roaming ...
- Wireless Network WLAN | Roaming wireless local area network ...