Security and Access Plans
Security and Access Plans
This solution extends ConceptDraw PRO software with physical security plan, security chart, access chart, security plans, access schemes, access plans , CCTV System Plan samples, templates and libraries of design elements for drawing the Security and Acce
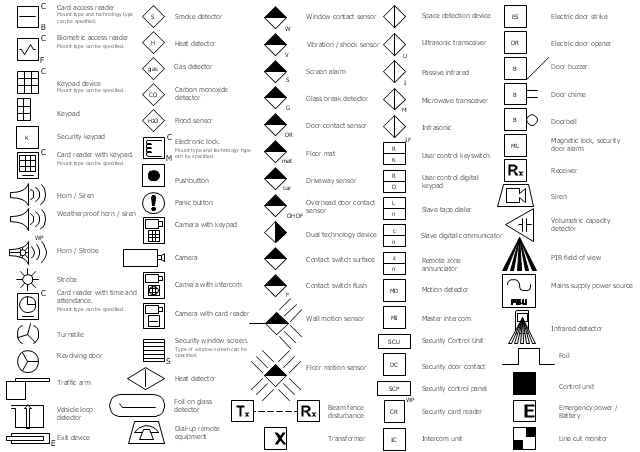
The vector stencils library Alarm and access control contains 80 symbols of digital proximity equipment, locking hardware, and access control equipment.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
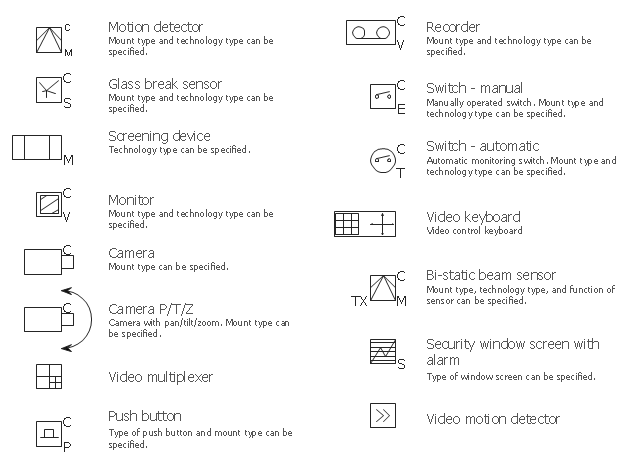
The vector stencils library Video surveillance contains 15 symbols of electronic closed-circuit television (CCTV) equipment, digital video cameras and recording devices and covert video equipment.
"Closed-circuit television (CCTV) is the use of video cameras to transmit a signal to a specific place, on a limited set of monitors. It differs from broadcast television in that the signal is not openly transmitted, though it may employ point to point (P2P), point to multipoint, or mesh wireless links. Though almost all video cameras fit this definition, the term is most often applied to those used for surveillance in areas that may need monitoring such as banks, casinos, airports, military installations, and convenience stores.
In industrial plants, CCTV equipment may be used to observe parts of a process from a central control room, for example when the environment is not suitable for humans. CCTV systems may operate continuously or only as required to monitor a particular event. A more advanced form of CCTV, utilizing digital video recorders (DVRs), provides recording for possibly many years, with a variety of quality and performance options and extra features (such as motion-detection and email alerts). More recently, decentralized IP cameras, some equipped with megapixel sensors, support recording directly to network-attached storage devices, or internal flash for completely stand-alone operation. Surveillance of the public using CCTV is particularly common in many areas around the world." [Closed-circuit television. Wikipedia]
Use the design elements library Video surveillance to design the layout plans of security and access systems, and internal and external video surveillance and security control monitoring systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Video surveillance is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"Closed-circuit television (CCTV) is the use of video cameras to transmit a signal to a specific place, on a limited set of monitors. It differs from broadcast television in that the signal is not openly transmitted, though it may employ point to point (P2P), point to multipoint, or mesh wireless links. Though almost all video cameras fit this definition, the term is most often applied to those used for surveillance in areas that may need monitoring such as banks, casinos, airports, military installations, and convenience stores.
In industrial plants, CCTV equipment may be used to observe parts of a process from a central control room, for example when the environment is not suitable for humans. CCTV systems may operate continuously or only as required to monitor a particular event. A more advanced form of CCTV, utilizing digital video recorders (DVRs), provides recording for possibly many years, with a variety of quality and performance options and extra features (such as motion-detection and email alerts). More recently, decentralized IP cameras, some equipped with megapixel sensors, support recording directly to network-attached storage devices, or internal flash for completely stand-alone operation. Surveillance of the public using CCTV is particularly common in many areas around the world." [Closed-circuit television. Wikipedia]
Use the design elements library Video surveillance to design the layout plans of security and access systems, and internal and external video surveillance and security control monitoring systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Video surveillance is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Trango" contains 10 clipart icons of Trango devices for drawing computer network diagrams and telecommunication equipment layouts.
"Trango Systems, Inc., was founded in 1996 and is headquartered in San Diego County, California. ...
Trango Systems microwave backhaul solutions and products are used in cellular/ mobile backhaul, Enterprise LAN/ WAN Bridging, All-IP Service Provider Networks, and Government/ Municipal applications." [trangosys.com]
The clip art example "Trango - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Telecommunication Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Trango Systems, Inc., was founded in 1996 and is headquartered in San Diego County, California. ...
Trango Systems microwave backhaul solutions and products are used in cellular/ mobile backhaul, Enterprise LAN/ WAN Bridging, All-IP Service Provider Networks, and Government/ Municipal applications." [trangosys.com]
The clip art example "Trango - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Telecommunication Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
- Security and Access Plans | How to Draw a Security and Access ...
- Design elements - Alarm and access control | Camera layout ...
- Layout Diagram Door Access Control
- Design elements - Alarm and access control | Office Layout Plans ...
- Illustration Area | Access Control And Cctv Systems Layout Drawing ...
- Security and Access Plans | Design elements - Alarm and access ...
- Design elements - Alarm and access control | Network layout ...
- Access Control System Usecase Diagram
- Door Symbol Used In Layout Diagram
- Erd For Door Access Control System
- Design elements - Alarm and access control | Physical Security Plan ...
- Smoke alarm equipment layout floor plan | Security and Access ...
- Security system floor plan | Design elements - Alarm and access ...
- Design elements - Alarm and access control | Alarm and access ...
- Door Access Control System Symbols
- How to Draw a Security and Access Floor Plan | Network Layout ...
- Access System
- Access Control Symbols Gate Vehicle
- Interior Design Office Layout Plan Design Element | Physical ...
- Design elements - Alarm and access control | Security system plan ...