The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
The vector stencils library "Logical symbols" contains 49 logical symbols for drawing logical network topology diagrams.
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Logical topology, or signal topology, is the arrangement of devices on a computer network and how they communicate with one another. How devices are connected to the network through the actual cables that transmit data, or the physical structure of the network, is called the physical topology. Physical topology defines how the systems are physically connected. It represents the physical layout of the devices on the network. The logical topology defines how the systems communicate across the physical topologies.
Logical topologies are bound to network protocols and describe how data is moved across the network. ... EXAMPLE : twisted pair Ethernet is a logical bus topology in a physical star topology layout. While IBM's token ring is a logical ring topology, it is physically set up in star topology." [Logical topology. Wikipedia]
The icons example "Logical symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
 Floor Plans
Floor Plans
Construction, repair and remodeling of the home, flat, office, or any other building or premise begins with the development of detailed building plan and floor plans. Correct and quick visualization of the building ideas is important for further construction of any building.
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Cooking Recipes
Cooking Recipes
Create quick and easy recipe diagrams with the Cooking Recipes solution. Make a tasty meal for dinner, for holidays, or for a party.
The vector stencils library "Cisco products additional" contains 141 symbols of computer network devices and equipment for drawing Cisco network diagrams.
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
 Aerospace and Transport
Aerospace and Transport
This solution extends ConceptDraw PRO software with templates, samples and library of vector clipart for drawing the Aerospace and Transport Illustrations. It contains clipart of aerospace objects and transportation vehicles, office buildings and anci
- Network Security . Computer and Network Examples | Cisco security ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Security Management
- Cisco security - Vector stencils library
- How To use Appliances Symbols for Building Plan | Design ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Network Diagram Software LAN Network Diagrams & Diagrams for ...
- Network Management Appliance
- Cisco Network Design. Cisco icons, shapes, stencils, symbols and ...
- Home area networks (HAN). Computer and Network Examples ...
- Network Security Diagrams | Network Glossary Definition | Network ...
- How To Create Emergency Plans and Fire Evacuation | Design ...
- How To use Appliances Symbols for Building Plan
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Appliances - Vector stencils library | Security system floor plan ...
- Cisco Network Equipment Vector Stencils
- Personal area (PAN) networks . Computer and Network Examples ...
- Project — Assigning Resources | Advanced Resource Assignment ...
- Local area network (LAN). Computer and Network Examples ...
- Ethernet local area network layout floor plan | Network Layout Floor ...





-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)





-logical-symbols---vector-stencils-library.png--diagram-flowchart-example.png)















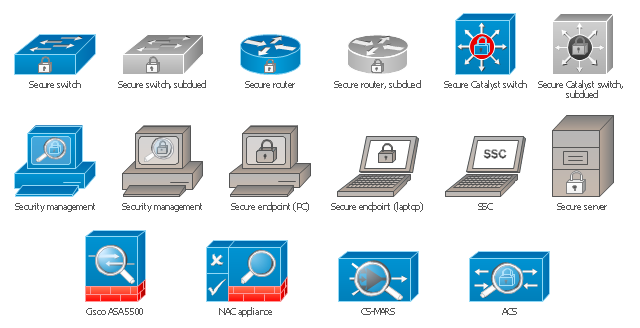




-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)






-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)

-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)

















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)




-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)