This example was designed on the base of the cybersecurity infographic from the website gov.uk. (Open Government Licence v3.0. nationalarchives.gov.uk/ doc/ open-government-licence/ version/ 3/ )
"10 Steps To Cyber Security...
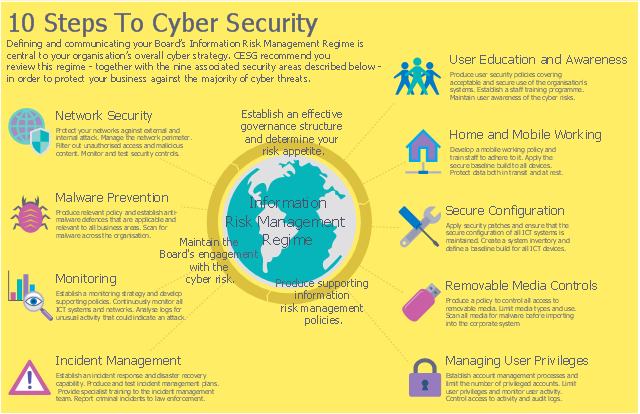
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Used Solutions
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw PRO software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
 Azure Architecture
Azure Architecture
Azure Architecture solution bundles into one handy tool everything you need to create effective Azure Architecture diagrams. It adds the extra value to versatile ConceptDraw PRO software and extends the users capabilities with comprehensive collection of Microsoft Azure themed graphics, logos, preset templates, wide array of predesigned vector symbols that covers the subjects such as Azure management, Azure storage, and Azure services, amongst others, and allow you to illustrate Azure Architecture diagrams at any degree of complexity, to present visually your Azure cloud system architecture with professional style, to design Azure cloud topology, to document Windows Azure Architecture and Azure Cloud System Architecture, to visualize the great abilities and work of Microsoft Azure Cloud System and Azure services.
- Network Security Monitoring
- 10 Steps to Cyber Security | Cloud round icons - Vector stencils ...
- Security and Access Plans | Computer Network Diagrams | Azure ...
- 10 Steps to Cyber Security | Network Security Tips | Network ...
- 10 Steps to Cyber Security | Camera layout schematic | Windows 10 ...
- Hvac Monitoring
- SYSML | Process Flowchart | Security and Access Plans | Activity ...
- Network Security Devices | Cyber Security Degrees | Network ...
- Use Case Diagram Of Remote Computer Monitoring