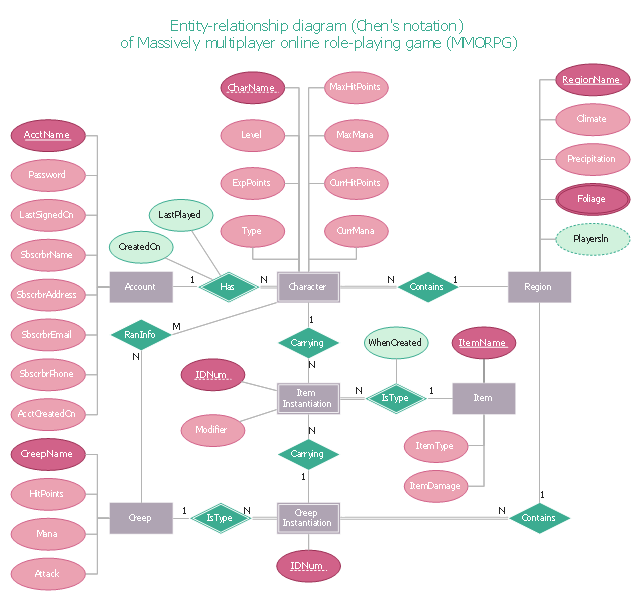
"In software engineering, an entity–relationship model (ER model) is a data model for describing a database in an abstract way.Chen's notation for entity–relationship modeling uses rectangles to represent entity sets, and diamonds to represent relationships appropriate for first-class objects: they can have attributes and relationships of their own. If an entity set participates in a relationship set, they are connected with a line.
Attributes are drawn as ovals and are connected with a line to exactly one entity or relationship set." [Entity–relationship model. Wikipedia]
This sample Chen's ER-diagram illustrates the structure of a typical MMORP game.
"Massively multiplayer online role-playing game (MMORPG) mixes the genres of role-playing video games and Massively multiplayer online games, possibly in the form of web browser-based games, in which a very large number of players interact with one another within a virtual world.
As in all RPGs, players assume the role of a character (often in a fantasy world or science-fiction world) and take control over many of that character's actions. MMORPGs are distinguished from single-player or small multi-player online RPGs by the number of players, and by the game's persistent world (usually hosted by the game's publisher), which continues to exist and evolve while the player is offline and away from the game." [Massively multiplayer online role-playing game. Wikipedia]
This ERD example was redrawn using the ConceptDraw PRO diagramming and vector drawing software from the Wikipedia file: ER Diagram MMORPG.png. [en.wikipedia.org/ wiki/ File:ER_ Diagram_ MMORPG.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
This Chen's ERD example is included in the Entity-Relationship Diagram (ERD) solution from the Software Development area of ConceptDraw Solution Park.
Attributes are drawn as ovals and are connected with a line to exactly one entity or relationship set." [Entity–relationship model. Wikipedia]
This sample Chen's ER-diagram illustrates the structure of a typical MMORP game.
"Massively multiplayer online role-playing game (MMORPG) mixes the genres of role-playing video games and Massively multiplayer online games, possibly in the form of web browser-based games, in which a very large number of players interact with one another within a virtual world.
As in all RPGs, players assume the role of a character (often in a fantasy world or science-fiction world) and take control over many of that character's actions. MMORPGs are distinguished from single-player or small multi-player online RPGs by the number of players, and by the game's persistent world (usually hosted by the game's publisher), which continues to exist and evolve while the player is offline and away from the game." [Massively multiplayer online role-playing game. Wikipedia]
This ERD example was redrawn using the ConceptDraw PRO diagramming and vector drawing software from the Wikipedia file: ER Diagram MMORPG.png. [en.wikipedia.org/ wiki/ File:ER_ Diagram_ MMORPG.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
This Chen's ERD example is included in the Entity-Relationship Diagram (ERD) solution from the Software Development area of ConceptDraw Solution Park.
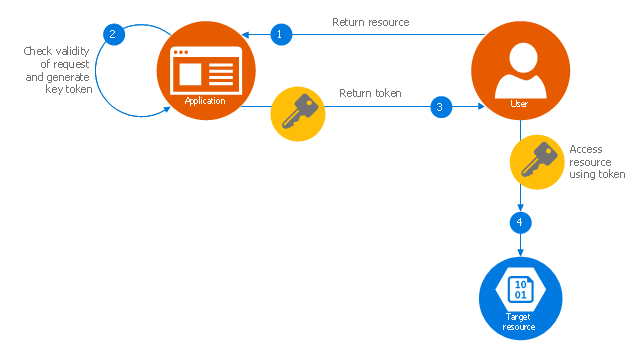
This Azure cloud architecture pattern diagram template was created on the base of figure in the article "Valet Key Pattern" from the Microsoft Developer Network (MSDN) website.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
"Valet Key Pattern.
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance. ...
Client programs and web browsers often need to read and write files or data streams to and from an application’s storage. ...
Data stores have the capability to handle upload and download of data directly, without requiring the application to perform any processing to move this data, but this typically requires the client to have access to the security credentials for the store.
... applications must be able to securely control access to data in a granular way, but still reduce the load on the server by setting up this connection and then allowing the client to communicate directly with the data store to perform the required read or write operations. ...
To resolve the problem of controlling access to a data store where the store itself cannot manage authentication and authorization of clients, one typical solution is to restrict access to the data store’s public connection and provide the client with a key or token that the data store itself can validate.
This key or token is usually referred to as a valet key. It provides time-limited access to specific resources and allows only predefined operations such as reading and writing to storage or queues, or uploading and downloading in a web browser. Applications can create and issue valet keys to client devices and web browsers quickly and easily, allowing clients to perform the required operations without requiring the application to directly handle the data transfer. This removes the processing overhead, and the consequent impact on performance and scalability, from the application and the server." [msdn.microsoft.com/ ru-RU/ library/ dn568102.aspx]
The Azure cloud system architecture diagram template "Valet key pattern" for the ConceptDraw PRO diagramming and vector drawing software is included in the Azure Architecture solutin from the Computer and Networks area of ConceptDraw Solution Park.
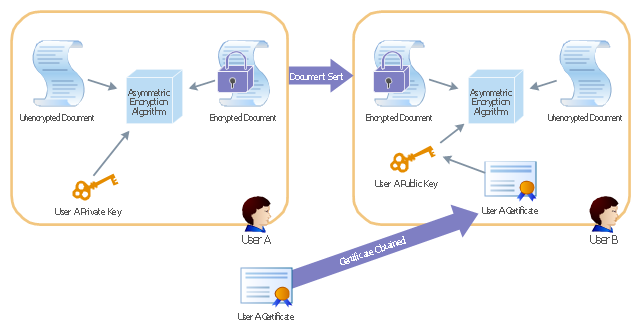
This AD diagram example was redesigned from the picture "Asymmetric
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
encryption" from the book "Active Directory for Dummies".
"Asymmetric Encryption:
This scenario uses a public and private key pair that is associated with each other. With this type of encryption, one of the keys is used to encrypt the data in such a way that only the corresponding second key is capable of decrypting the information. ...
In asymmetric encryption, two different keys are involved in the process: one for encrypting the document and a different but related key for decrypting the document. The two keys are generated at the same time so that if a document is encrypted with one of the keys, only the second related key can decrypt the document. ... Typically, these keys are referred to as a private key and a public key. A private key is one that is generated for a particular user and is never shared with any other user or computer. A public key is typically one of the pieces of data that’s stored in a PKI certificate. Although this type of encryption creates a very secure way of sharing data, an added benefit is you knowing that a piece of data decrypted by using a particular user’s public key must have come from that user because no other user would have the private key the document was encrypted with."
[Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Asymmetric encryption" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Sales Flowcharts
Sales Flowcharts
The Sales Flowcharts solution lets you create and display sales process maps, sales process workflows, sales steps, the sales process, and anything else involving sales process management.
- Key Cartoon Png
- Glyphicon Of Key Png
- Key Tool Png
- Key Activities Vector Png
- Orange Updown Arrow Png
- Sales symbols - Vector stencils library | Tourism in the world: key ...
- Glyph icons - Vector stencils library | Css Search Png
- Key Vector Png
- Growth Of Indicators Png
- Blob Storage Icon Png
- Key Icon Png
- Chevron Focus Indicator Icon Png
- Glyph icons - Vector stencils library | Gear Settings Png
- Pathway Png
- Sns Cisco Png Icons
- Ios Refresh Icon Line Png
- Tourism in the world: key figures
- Sunlight Arrow Png
- White Searchicon Png
- Orange Triangle Png