- Electric and Telecom Plans Free
- Fire and Emergency Plans Free
- Floor Plans Free
- Plant Layout Plans Free
- School and Training Plans Free
- Seating Plans Free
- Security and Access Plans Free
- Site Plans Free
- Sport Field Plans Free
- Business Process Diagrams Free
- Business Process Mapping Free
- Classic Business Process Modeling Free
- Cross-Functional Flowcharts Free
- Event-driven Process Chain Diagrams Free
- IDEF Business Process Diagrams Free
- Logistics Flow Charts Free
- Workflow Diagrams Free
- ConceptDraw Dashboard for Facebook Free
- Mind Map Exchange Free
- MindTweet Free
- Note Exchange Free
- Project Exchange Free
- Social Media Response Free
- Active Directory Diagrams Free
- AWS Architecture Diagrams Free
- Azure Architecture Free
- Cisco Network Diagrams Free
- Cisco Networking Free
- Cloud Computing Diagrams Free
- Computer Network Diagrams Free
- Google Cloud Platform Free
- Interactive Voice Response Diagrams Free
- Network Layout Floor Plans Free
- Network Security Diagrams Free
- Rack Diagrams Free
- Telecommunication Network Diagrams Free
- Vehicular Networking Free
- Wireless Networks Free
- Comparison Dashboard Free
- Composition Dashboard Free
- Correlation Dashboard Free
- Frequency Distribution Dashboard Free
- Meter Dashboard Free
- Spatial Dashboard Free
- Status Dashboard Free
- Time Series Dashboard Free
- Basic Circle-Spoke Diagrams Free
- Basic Circular Arrows Diagrams Free
- Basic Venn Diagrams Free
- Block Diagrams Free
- Concept Maps Free
- Family Tree Free
- Flowcharts Free
- Basic Area Charts Free
- Basic Bar Graphs Free
- Basic Divided Bar Diagrams Free
- Basic Histograms Free
- Basic Line Graphs Free
- Basic Picture Graphs Free
- Basic Pie Charts Free
- Basic Scatter Diagrams Free
- Aerospace and Transport Free
- Artwork Free
- Audio, Video, Media Free
- Business and Finance Free
- Computers and Communications Free
- Holiday Free
- Manufacturing and Maintenance Free
- Nature Free
- People Free
- Presentation Clipart Free
- Safety and Security Free
- Analog Electronics Free
- Audio and Video Connectors Free
- Basic Circuit Diagrams Free
- Chemical and Process Engineering Free
- Digital Electronics Free
- Electrical Engineering Free
- Electron Tube Circuits Free
- Electronic Block Diagrams Free
- Fault Tree Analysis Diagrams Free
- GHS Hazard Pictograms Free
- Home Automation and Wiring Free
- Mechanical Engineering Free
- One-line Diagrams Free
- Power Сircuits Free
- Specification and Description Language (SDL) Free
- Telecom and AV Circuits Free
- Transport Hazard Pictograms Free
- Data-driven Infographics Free
- Pictorial Infographics Free
- Spatial Infographics Free
- Typography Infographics Free
- Calendars Free
- Decision Making Free
- Enterprise Architecture Diagrams Free
- Fishbone Diagrams Free
- Organizational Charts Free
- Plan-Do-Check-Act (PDCA) Free
- Seven Management and Planning Tools Free
- SWOT and TOWS Matrix Diagrams Free
- Timeline Diagrams Free
- Australia Map Free
- Continent Maps Free
- Directional Maps Free
- Germany Map Free
- Metro Map Free
- UK Map Free
- USA Maps Free
- Customer Journey Mapping Free
- Marketing Diagrams Free
- Matrices Free
- Pyramid Diagrams Free
- Sales Dashboard Free
- Sales Flowcharts Free
- Target and Circular Diagrams Free
- Cash Flow Reports Free
- Current Activities Reports Free
- Custom Excel Report Free
- Knowledge Reports Free
- MINDMAP Reports Free
- Overview Reports Free
- PM Agile Free
- PM Dashboards Free
- PM Docs Free
- PM Easy Free
- PM Meetings Free
- PM Personal Time Management Free
- PM Planning Free
- PM Presentations Free
- PM Response Free
- Resource Usage Reports Free
- Visual Reports Free
- House of Quality Free
- Quality Mind Map Free
- Total Quality Management TQM Diagrams Free
- Value Stream Mapping Free
- Astronomy Free
- Biology Free
- Chemistry Free
- Language Learning Free
- Mathematics Free
- Physics Free
- Piano Sheet Music Free
- Android User Interface Free
- Class Hierarchy Tree Free
- Data Flow Diagrams (DFD) Free
- DOM Tree Free
- Entity-Relationship Diagram (ERD) Free
- EXPRESS-G data Modeling Diagram Free
- IDEF0 Diagrams Free
- iPhone User Interface Free
- Jackson Structured Programming (JSP) Diagrams Free
- macOS User Interface Free
- Object-Role Modeling (ORM) Diagrams Free
- Rapid UML Free
- SYSML Free
- Website Wireframe Free
- Windows 10 User Interface Free
Network Security Diagrams
The Internet is a giant computer network, which connects billions of computers around the world, it is integral part of our everyday’s life and a huge world of unlimited possibilities. The Internet is an inexhaustible mine of information and enormous knowledge repository. It is a mean of sharing personal experiences and free mass media. But at the same time, the Internet is fraught with many dangers and threats including the cyber-attacks and various malicious programs, utilities, viruses, worms, trojans, and many others.
The computers and computer networks connected with Internet are very vulnerable. They are exposed daily to a large number of different attacks and dangers, and as a result, they need for effective protection. A software and network security devices are helping in the network security ensuring with different cyber security degrees. The task of network’s protection is particularly acute for enterprises and companies that use the Internet to transmit their data, in this case it is important to ensure the data protection during their transmission over the communication lines, to guarantee the reliable information storage, and also protection from the unauthorized remote access to the network. When creating a reliable network security plan, it is important to adhere network security tips, to take into account specifics of hardware, software, and company's policy, to anticipate the whole range of possible threats to this network and devise a tactic of defense.
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors. It will help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples included to Network Security Diagrams solution reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
-
Install this solution Free -
What I need to get started -
Solution Requirements - This solution requires the following products to be installed:
ConceptDraw DIAGRAM v17 - This solution requires the following products to be installed:
-
Compatibility - Monterey (12), Ventura (13), Sonoma (14)
MS Windows 8.1, 10 - Monterey (12), Ventura (13), Sonoma (14)
-
Support for this Solution -
Helpdesk
There are 4 stencil libraries containing 460 vector graphics for Network Security Diagrams solution.
Design Elements — Cybersecurity Сlipart

Design Elements — Cybersecurity Connectors
Design Elements — Cybersecurity Round Icons
Design Elements — Cybersecurity Shapes

Network Security Diagrams Examples
There are a few samples that you see on this page which were created in the ConceptDraw DIAGRAM application by using the Network Security Diagrams solution. Some of the solution's capabilities as well as the professional results which you can achieve are all demonstrated here on this page.
All source documents are vector graphic documents which are always available for modifying, reviewing and/or converting to many different formats, such as MS PowerPoint, PDF file, MS Visio, and many other graphic ones from the ConceptDraw Solution Park or ConceptDraw STORE. The Network Security Diagrams solution is available to all ConceptDraw DIAGRAM users to get installed and used while working in the ConceptDraw DIAGRAM diagramming and drawing software.
Example 1: 10 Steps to Cyber Security Infographic
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 15 minutes creating this sample.
What is a cyber security and what are the ways of its assurance? The cyber security is a huge set of different tools of protection, among which there are special programs for protection against hacking, the back-up systems and other tools that continuously protect the information and resources of organizations and users from the intruders. This infographic shows 10 steps to cyber security, which can be used by organizations as effective ways for protecting from cyber-attacks. From this diagram you can see that the Information Risk Management Regime possess the central place in overall cyber strategy of an organization. It is surrounded with nine not less important steps: Network security, Malware prevention, Monitoring, Incident management, User education and awareness, Home and mobile working, Secure configuration, Removable media controls, and Managing user privileges. Use the Network Security Diagrams solution to tell about the news at a network security field and network security devices in a visual and attractive way.

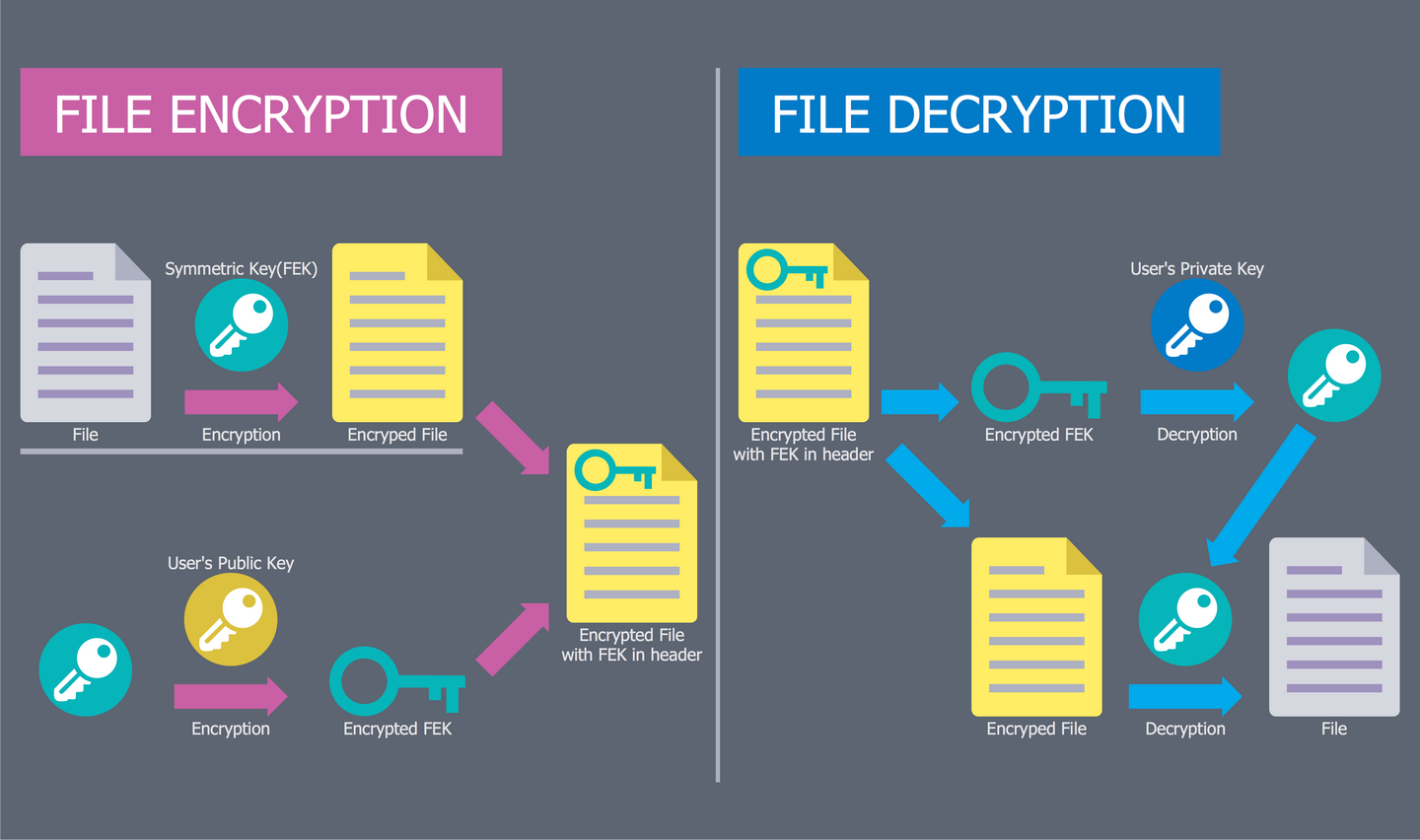
Example 2: EFS Operation
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 5 minutes creating this sample.
This Network Security Schematic illustrates the Encrypting File System (EFS) - the technology realized at Microsoft Windows, which provides the encryption of the file system with a goal to protect the confidential information and data from the attackers that possess a physical access to the computer. By default, the files are not encrypted, but this function can be enabled by users for a certain file, directory, or drive. The space on this diagram is divided on two parts, at the left side is visually represented the process of file encryption, at the right part - the process of its decryption. The colorful, attractive and vivid elements from the libraries of Network Security Diagrams solution make the Cyber Security Diagrams designed in ConceptDraw DIAGRAM software clear and appealing for speaker and wide audience. They are perfect anywhere, where they are in demand - in reports, science magazines, articles on the websites, and so on.
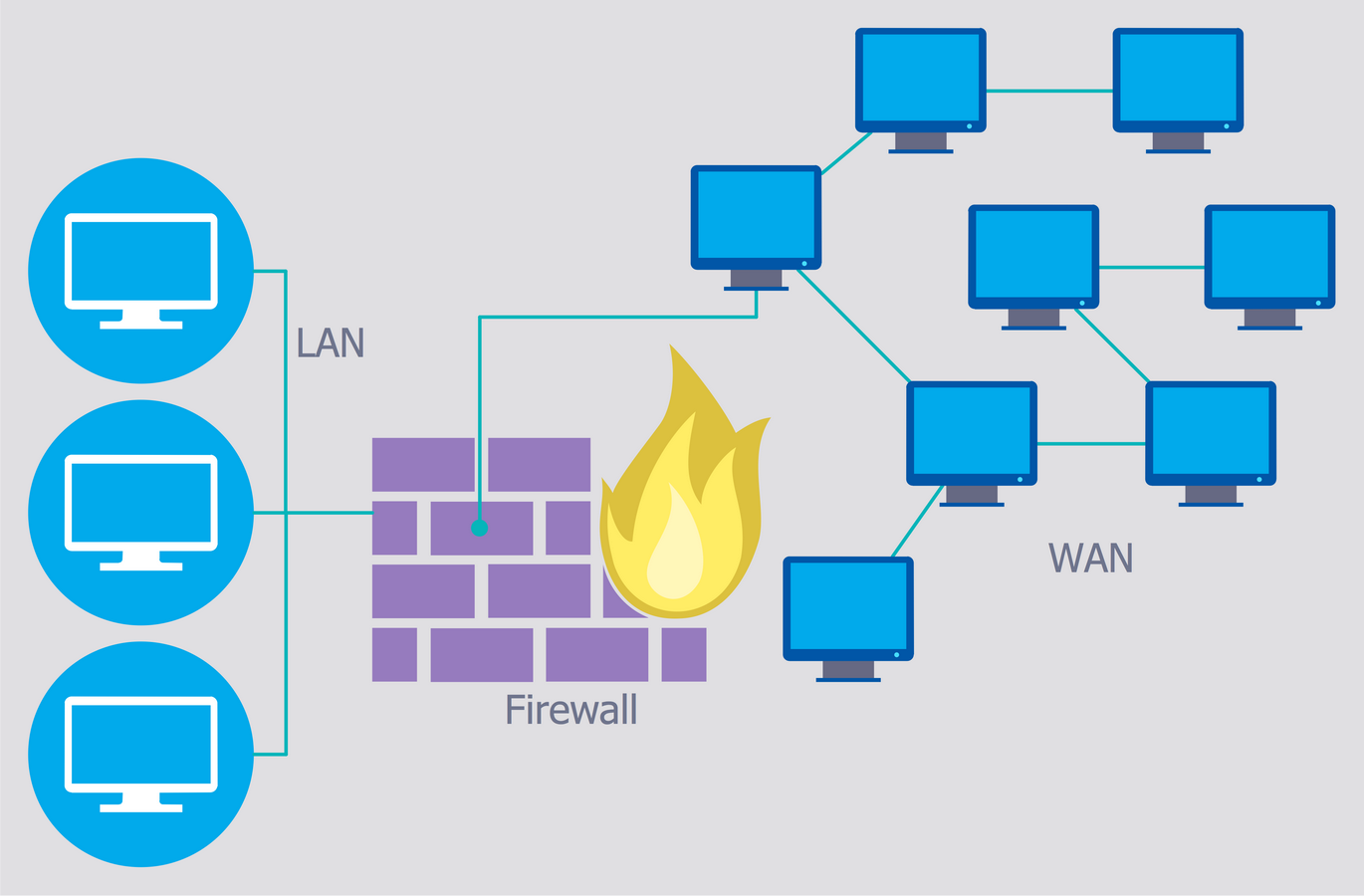
Example 3: Firewall Between LAN and WAN
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 5 minutes creating this sample.
Nowadays, the global network abounds with wide variety of malicious software and viruses. To protect your computer or the local network of several computers from these occurences is recommended to use a firewall. The firewall is the set of hardware and software used at a computer network for the control of incoming and outcoming traffic with a goal of network protection from the external threats, attacks, illegal entry, unauthorized access to personal data, operating system and files. It is one of the basic and the most easily implemented methods of network security, often its actions are unnoticed, but it is desperately required for the safety of your computer and local network. This Network Security Diagram illustrates the use of firewall and its correct placement between the Local Area Network (LAN) and Wide Area Network (WAN). For greater reliability it is recommended to use a firewall simultaneously with reliable antivirus software.
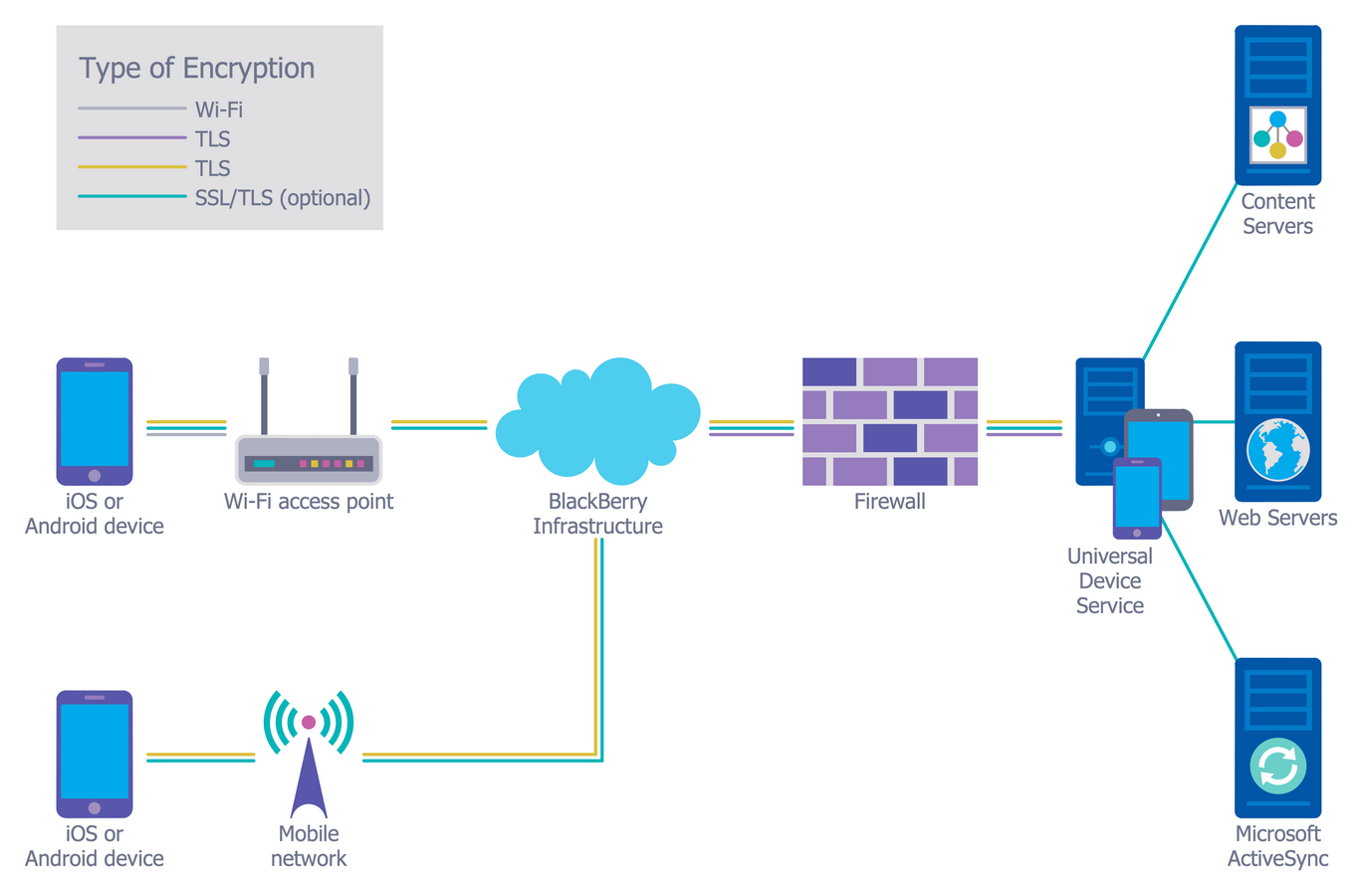
Example 4: Recommended Network Architecture
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 5 minutes creating this sample.
This sample is an excellent example of network architecture with marked on it types of cryptographic protocols. In real networks, you can combine various ways of assuring network security, it is useful to learn the network security tips and apply them to envisage all cyber security degrees. The main security components on this diagram are BlackBerry Infrastructure, Firewall and Universal Device Service. The BlackBerry Infrastructure was developed to help manage the mobile devices of a company and to provide a secure connection to transfer the data between the company's mail, the content servers and user's devices. The BlackBerry Infrastructure provides the reliable and secure path between the company and each user, which is based on cryptographic, strong and mutual authentication. A firewall is a network security device, which monitors the incoming and outgoing network traffic, allows or blocks it. The Universal Device Service lets to manage the iOS devices and Android devices at your company's environment.
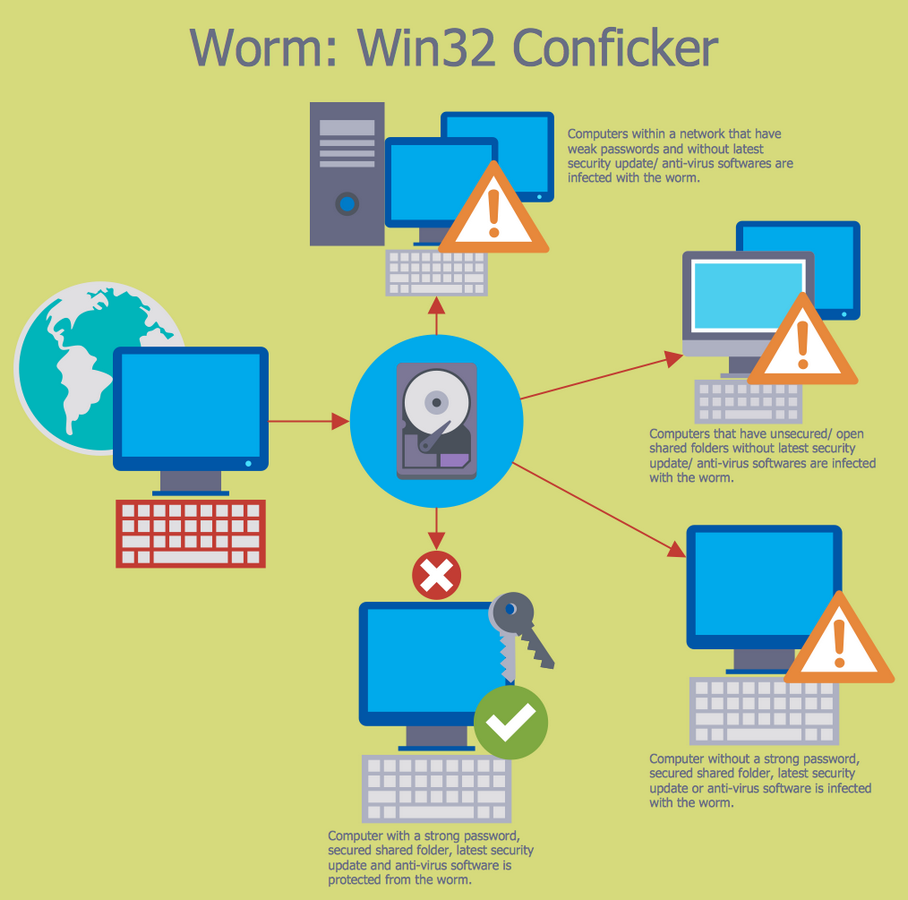
Example 5: Spread of Conficker Worm
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 10 minutes creating this sample.
The ensuring of safety of a wireless network and all other types of networks is a necessity today. This Cybersecurity Diagram narrates about the protection of your computer from the Conficker, which is a fast-spreading worm, a blended threat oriented on the vulnerability of a Windows operating system. The computer worm is a standalone malware computer program, which has a property to replicate itself in a computer and to spread to other computers using the computer network, to send automatically its copies by e-mail, without requiring any user actions. A qualitative firewall in combination with an antivirus software helps to protect sustainably your computer from the malicious virtual worms that reduce the speed of your computer, consume large amounts of system memory and network bandwidth. Use the modern IT security solutions, ConceptDraw DIAGRAM diagramming and vector drawing software with Network Security Diagrams solution to develop new ways of network security and to realize them effectively.
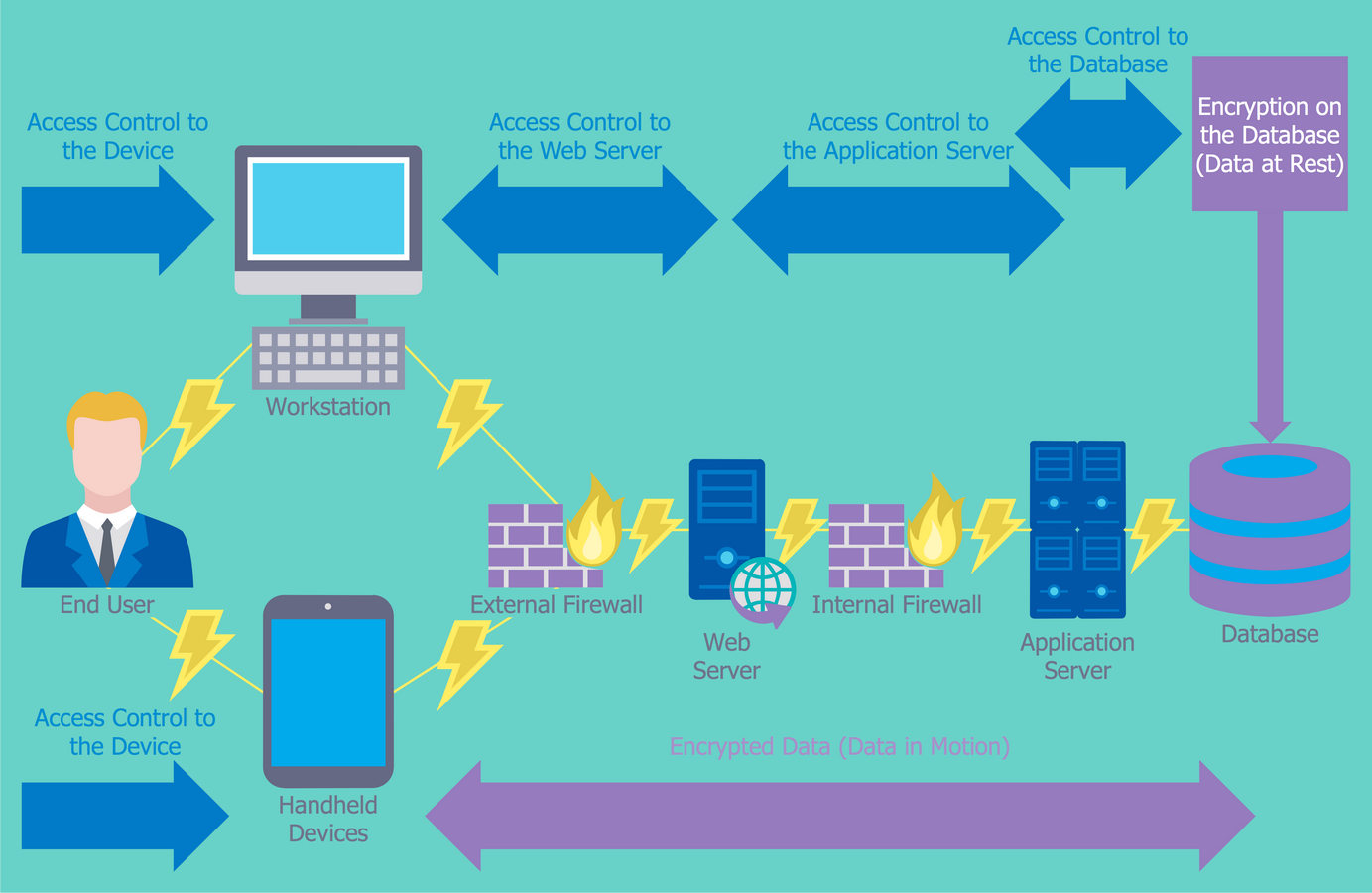
Example 6: Access Control and Encryption
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 10 minutes creating this sample.
The access control is used to limit the access of some users categories to a certain device, web server, application server or a database. The encryption is one of ways to access control, it lets to convert the plain text into the ciphertext that is looks like the set of random characters. And only the application of a key lets transform it backwards to the plain text. Typically, the key is a mathematical algorithm known only to the sender of message and its intended recipient, moreover for encryption and decryption of information should be used the same key, otherwise the text reading will be impossible. This computer security diagram was designed with help of the Network Security Diagrams solution tools on the base of the diagram from the website of the Centers for Disease Control and Prevention (CDC) and describes how to secure the data using together the access control and encryption.
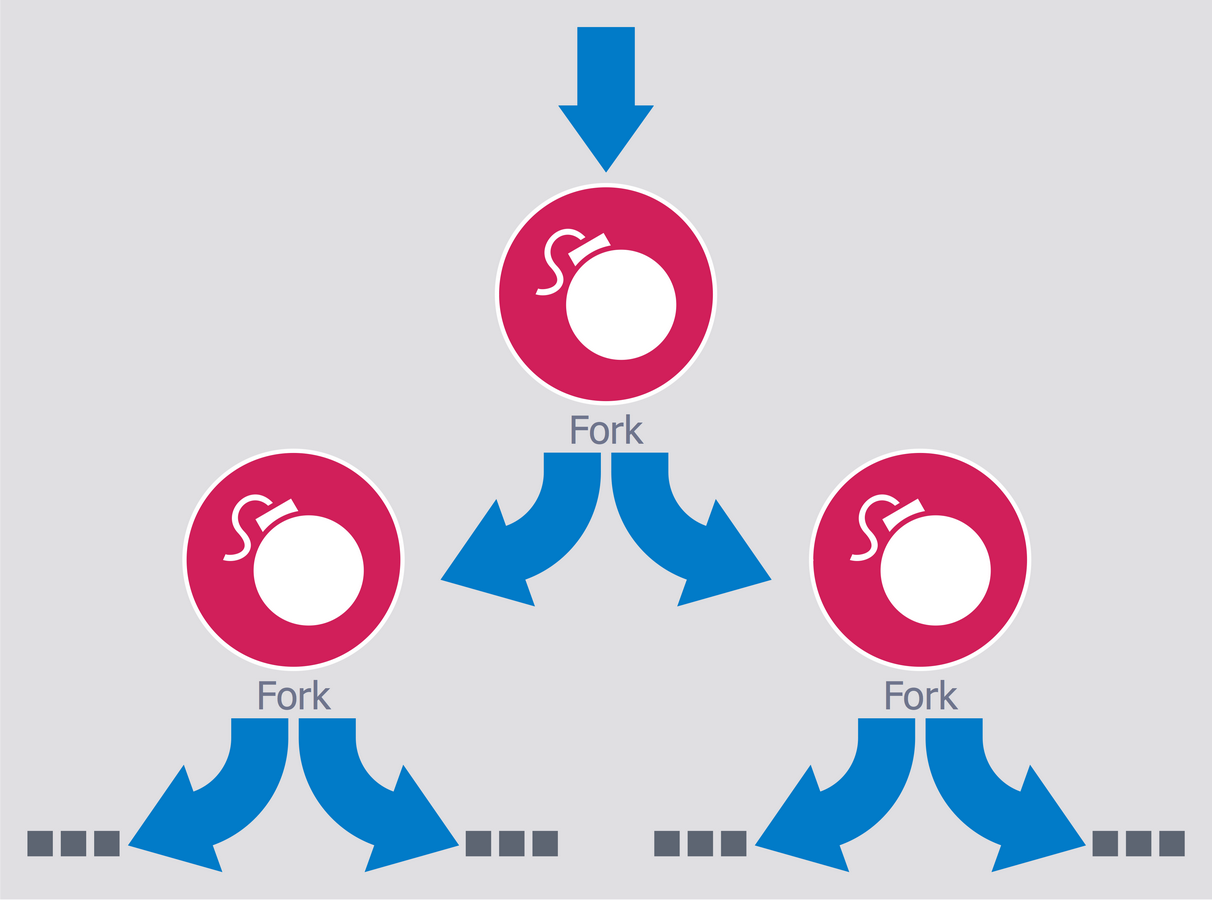
Example 7: Fork Bomb
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 10 minutes creating this sample.
This sample illustrates the principle of the Fork bomb, also known as a rabbit virus or wabbit. A Fork bomb is a malicious or incorrectly written program that infinitely creates the copies of itself, which also create the copies of themselves, etc. filling all free space in the list of active processes of the operating system, in result of that becomes impossible to start any other useful program. A Fork bomb is not necessarily a specially written program, it can be caused by the simple programming error and to lead finally to serious consequences from the memory leak until the complete cessation a system's work. On this diagram you can see the processes that are recursively forked, in result of this occurs the deplete of available resources, the denial of service and the system crash due to heavy workload on a computing system and the critical lack of system resources.
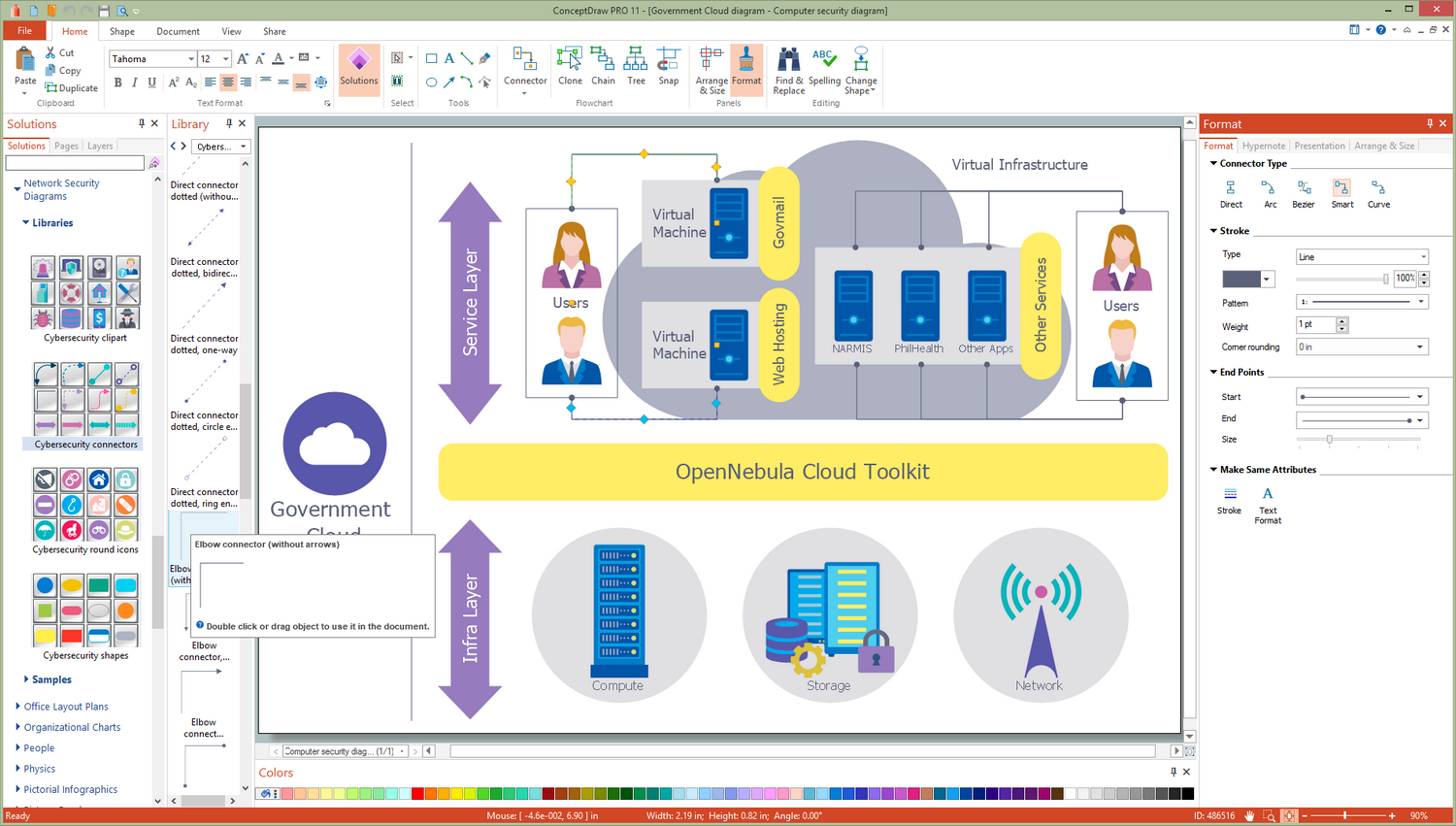
Example 8: Government Cloud Diagram
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 10 minutes creating this sample.
In connection with constantly rising amounts of information and data, and necessity of increasing the effectiveness of work with them, the organizations more and more begin to use the cloud technologies and services. A Government Cloud or a GovCloud is a cloud model, which gives to governments abilities to provide the cloud services for the government agencies, lets to ensure an effective control over the national security and protection the citizens in a cyber space, gives some measure of freedom for people in compliance with law and regulations within a country. This sample was designed on the base of computer security diagram from the website of Integrated Government Philippines (iGovPhil) Project and illustrates the arrangement and use of a Government Cloud at the country. The use of cloud applications instead traditional IT systems is welcomed by the Department of Science and Technology agencies, the Information and Communications Technology Office, and the Advanced Science and Technology Institute.

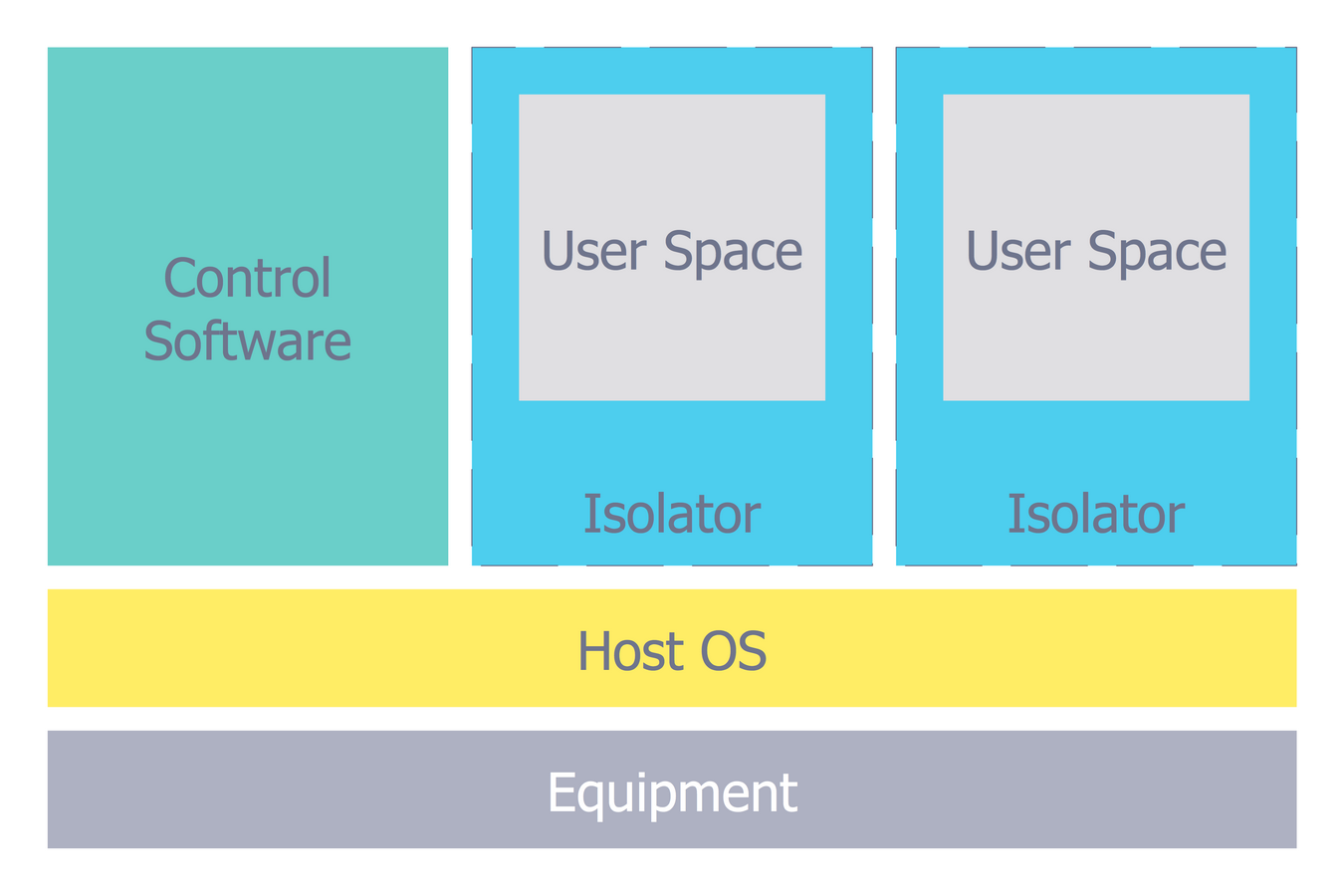
Example 9: Isolator Architecture Diagram
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 10 minutes creating this sample.
This Computer Security Diagram example visualizes the architecture of an isolator. The isolator is a software used for isolation of execution the applications in the areas of implementation and the contexts. It lets to run the same application a few times in multiple instances, even if it was not intended for this. The isolator is a very efficient solution with small amount of overheads, such as time spent by a system, but the virtualized environments are not completely isolated. A virtualization is an act of creation of a virtual version of something, including the virtual computer hardware platforms, storage devices, operating systems, and computer network resources. Only the isolators related with Linux systems actually consist of several components and can take various forms. The use of simple predesigned elements offered by the libraries of Network Security Diagrams solution, allowed to create this comprehensive and detailed diagram in a few moments.
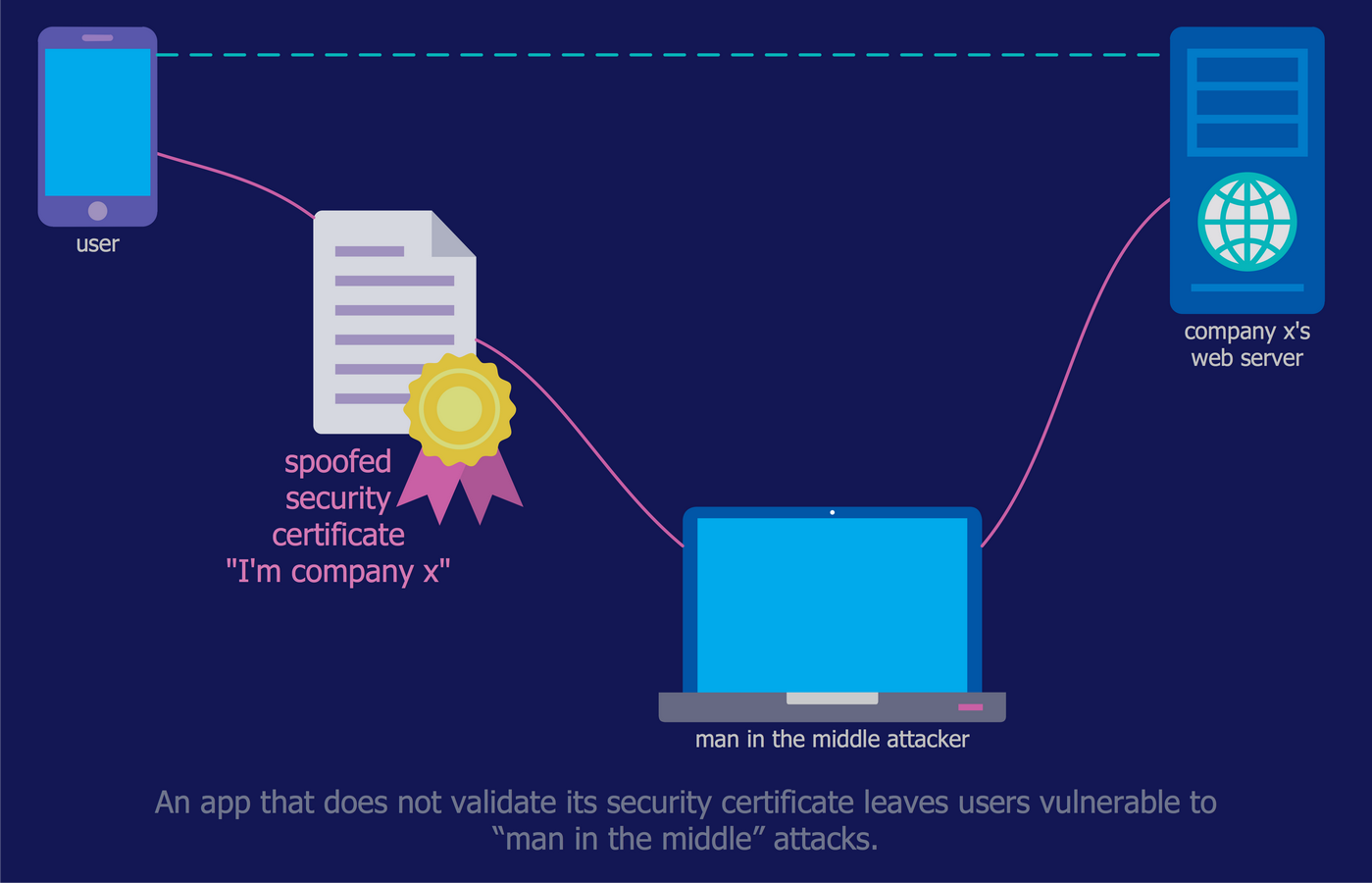
Example 10: Mobile App Security
This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An experienced user spent 10 minutes creating this sample.
The range of applications for modern mobile devices impresses with its diversity. However, not many of them, even the most popular, secure and encrypt the information that they send or receive. This often turns by a serious threat to users and their devices, especially when you work with your bank account, fill the taxes, or make the purchases with a credit card. This sample was designed on the base of diagram from the article "How secure is that mobile app?" of N.V. Fleming published on the website of the U.S. Federal Trade Commission (FTC). Often the companies not validate security certificates to make sure that the apps sent the information to the right place. So, the users are susceptible to the attacks of the “man in the middle”, which remaining unnoticed can simply trick the app and allows it the access to communications between the app and online service. The best way of protection is to use secure networks, which obligatory encrypt the information.
Inside

What I Need to Get Started
Both ConceptDraw DIAGRAM diagramming and drawing software and the Network Security Diagrams solution can help illustrate useful knowledge about network security, cyber security degrees, secure wireless network. The Network Security Diagrams solution can be found in the Computer and Networks area of ConceptDraw STORE application that can be downloaded from this site. Make sure that both ConceptDraw DIAGRAM and ConceptDraw STORE applications are installed on your computer before you get started.
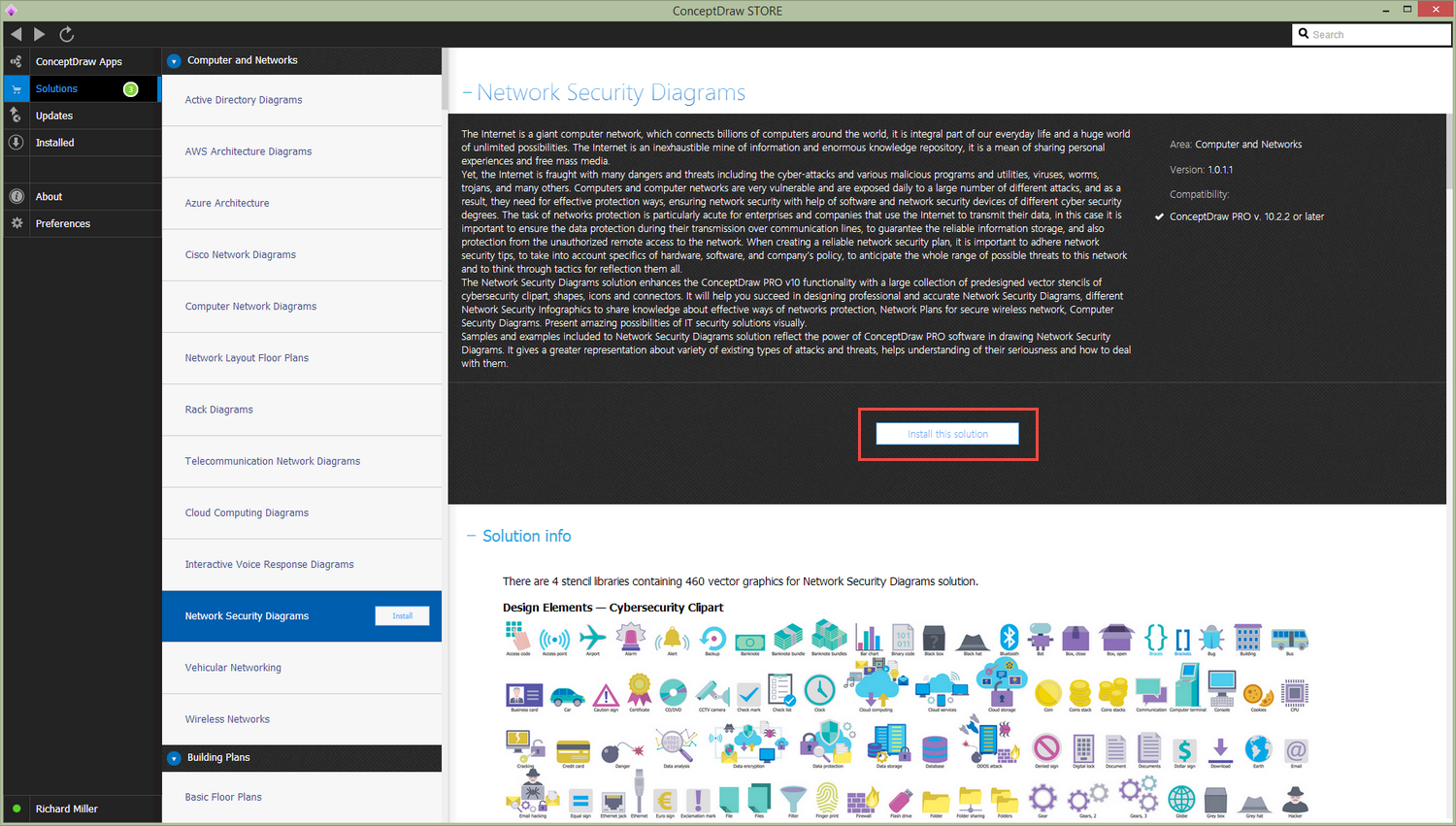
How to install
After ConceptDraw STORE and ConceptDraw DIAGRAM are downloaded and installed, you can install the Network Security Diagrams solution from the ConceptDraw STORE.
Start using
To make sure that you are doing it all right, use the pre-designed symbols from the stencil libraries from the solution to make your drawings look smart and professional. Also, the pre-made examples from this solution can be used as drafts so your own drawings can be based on them. Using the samples, you can always change their structures, colors and data.