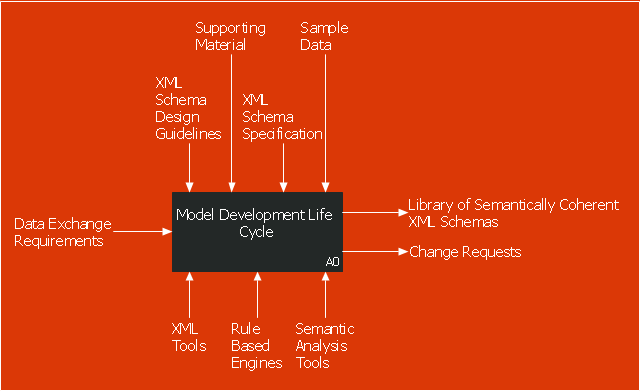
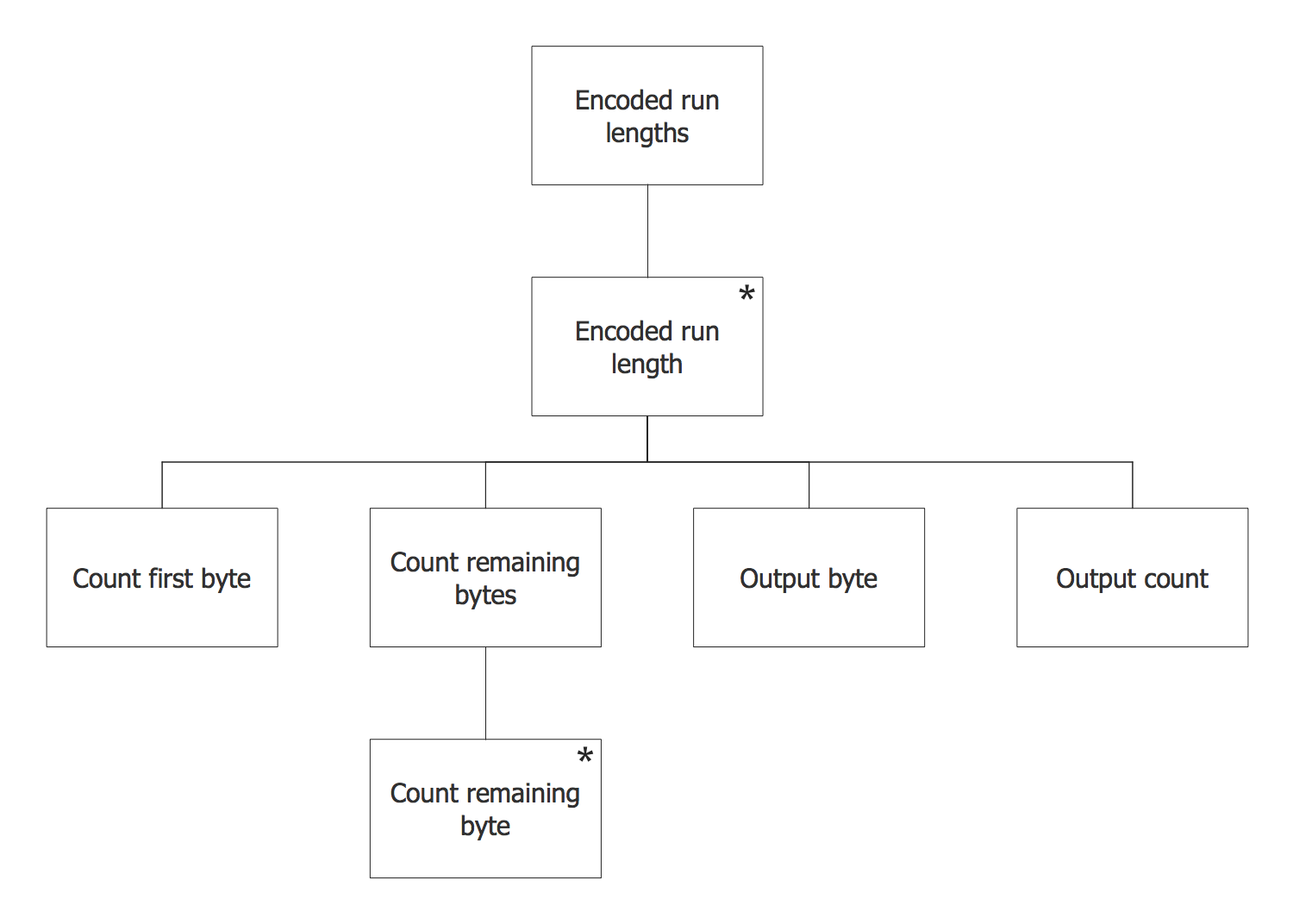
This IDEF0 diagram sample was created on the base of the figure from the website of the Engineering Laboratory of the National Institute of Standards and Technology (NIST). [mel.nist.gov/ msidlibrary/ doc/ kc_ morris/ gsa-final_ files/ image002.gif]
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life cycle. Wikipedia]
The IDEF0 diagram example "Model development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the IDEF0 Diagrams solution from the Software Development area of ConceptDraw Solution Park.
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life cycle. Wikipedia]
The IDEF0 diagram example "Model development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the IDEF0 Diagrams solution from the Software Development area of ConceptDraw Solution Park.
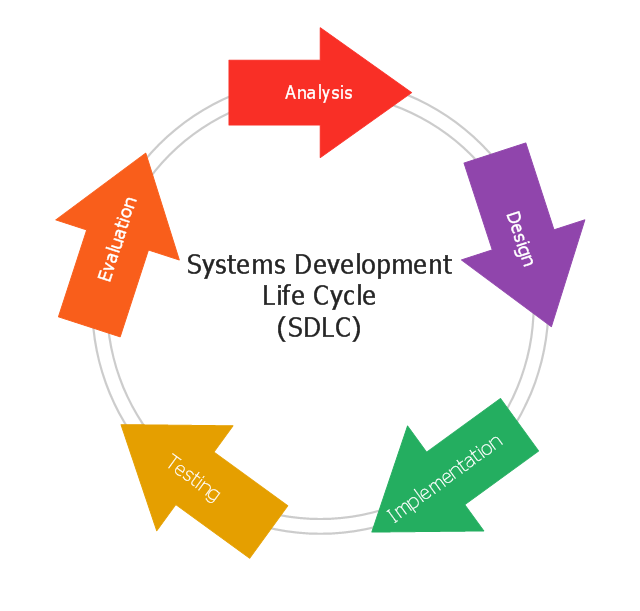
This circular arrows diagram sample shows the systems development life cycle (SDLC) stages.
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life-cycle. Wikipedia]
The arrow circle diagram example "Systems development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
"The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. The systems development life-cycle concept applies to a range of hardware and software configurations, as a system can be composed of hardware only, software only, or a combination of both." [Systems development life-cycle. Wikipedia]
The arrow circle diagram example "Systems development life cycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
Program to Make Flow Chart
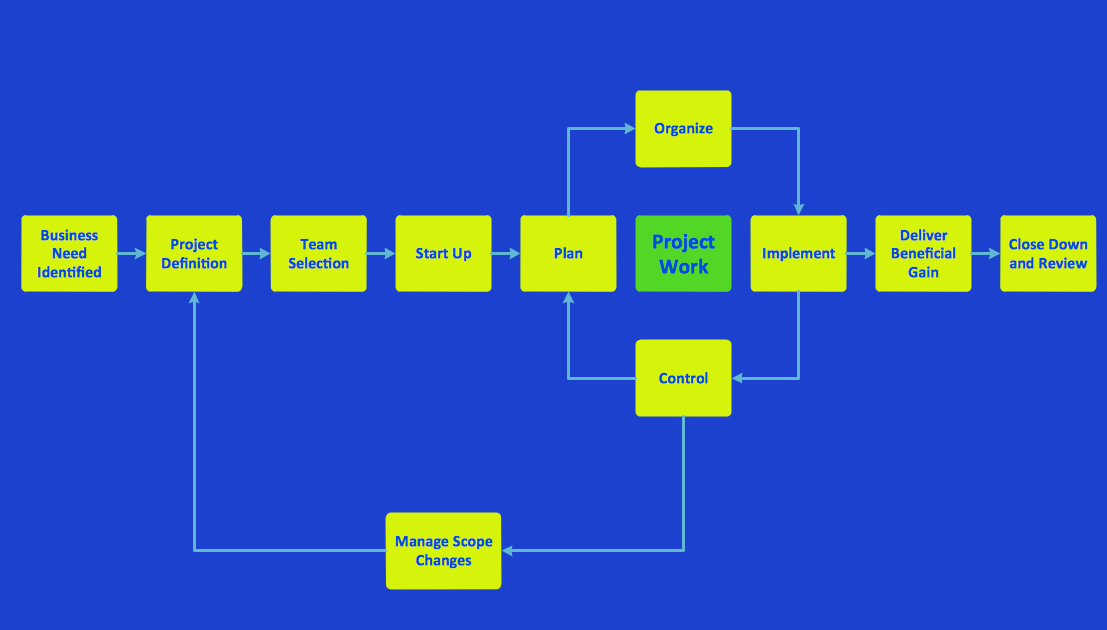
Use ConceptDraw PRO diagramming and business graphics software for drawing your own PM life cycle flow charts.Structured Systems Analysis and Design Method (SSADM) with ConceptDraw PRO
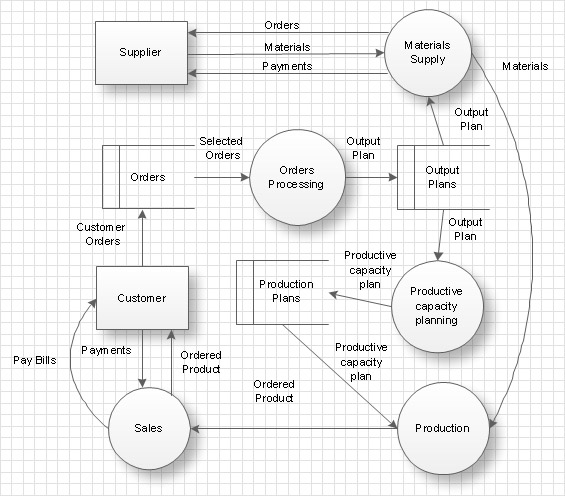
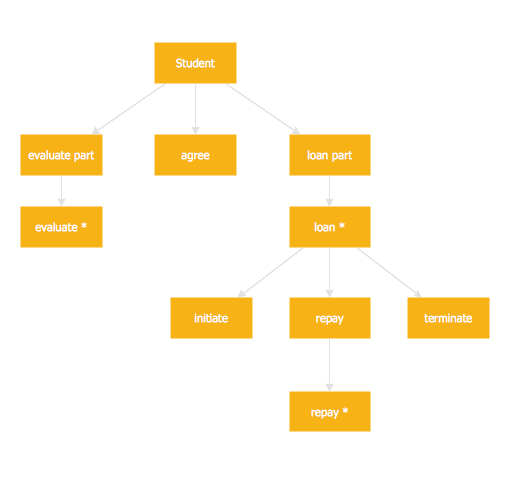
Structured Systems Analysis and Design Method SSADM is the method which is used at projecting and analysis of information systems. SSADM is based on the data flow diagrams. At the description of data flows out of the system and into the system DFD, which denote boundaries of the system, are used.Data Flow Diagram
Data flow diagram (DFD) is the part of the SSADM method (Structured Systems Analysis and Design Methodology), intended for analysis and information systems projection. Data flow diagrams are intended for graphical representation of data flows in the information system and for analysis of data processing during the structural projection. Data flow diagram often used in connection with human process and can be displayed as workflow diagram. The critical Process Flow Diagram is another flowchart technique for designing data flow in connection with organizational processes. The critical Process flow diagram may use different range of symbols than a classic workflow diagram.Jackson Systems
Entity structure diagram (ESD) notations may be created in the ConceptDraw PRO same as any other diagram, including a Jackson Structured Programming (JSP) Diagram. Having the Jackson Structured Programming (JSP) Diagrams solution may simplify the work of drawing the needed illustration representing the given data within only a few minutes. Having the pre-made examples of the JSP diagrams, any ConceptDraw PRO user is able to make his own unique as well as smart looking drawing in a fun and entertaining way.JSD - Jackson system development
Jackson System Development (JSD) is a linear method of system development created by Michael A. Jackson and John Cameron in the 1980s. It comprises the whole software life cycle directly or providing a framework for more specialized techniques.When implementing the Jackson System Development method and designing JSD diagrams, you can succesfully use the powerful and helpful tools of ConceptDraw PRO software extended with Entity-Relationship Diagram (ERD) solution from the Software Development area of ConceptDraw Solution Park.
Total Quality Management Value
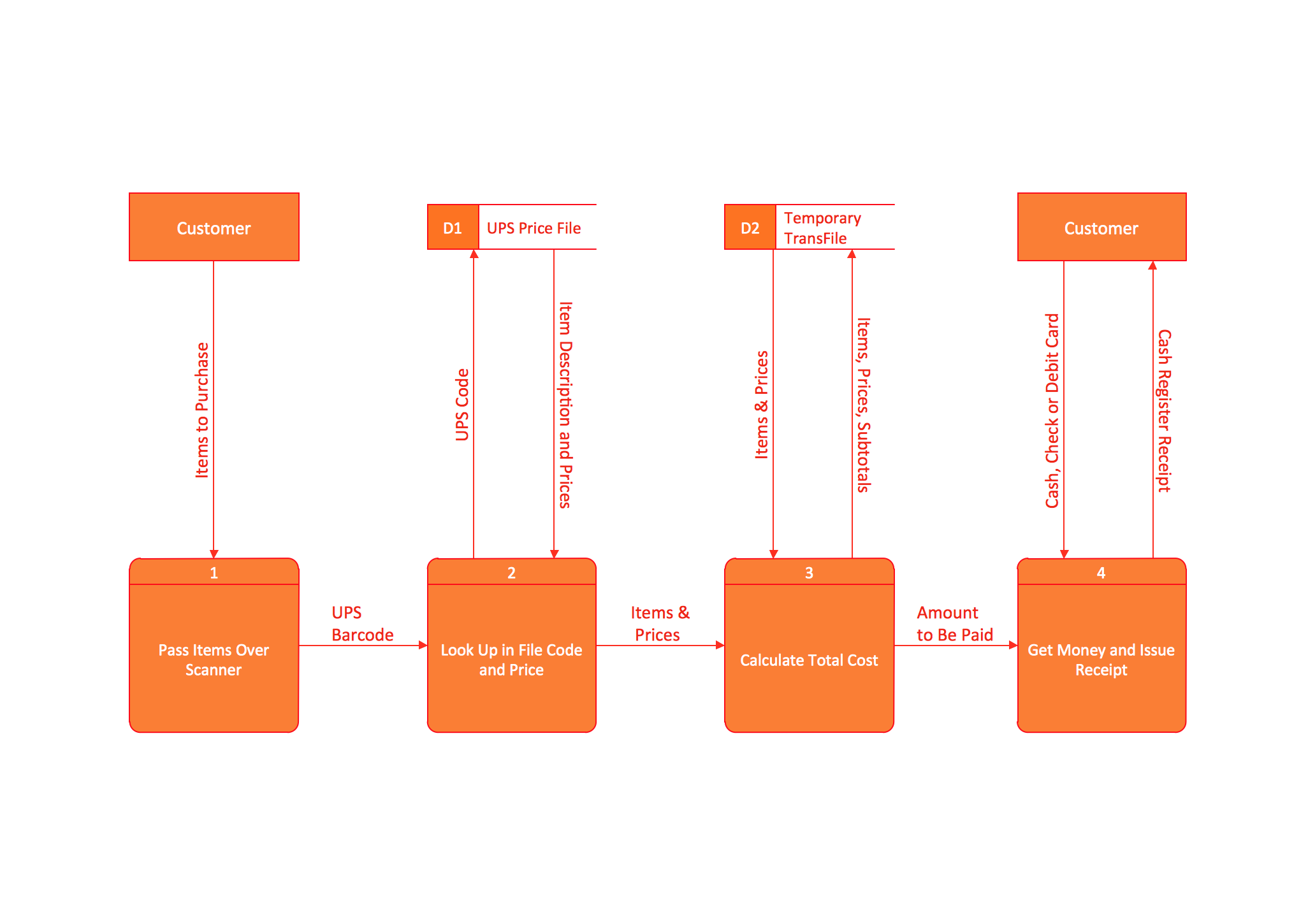
The Total Quality Management Diagram solution helps you and your organization visualize business and industrial processes. Create Total Quality Management diagrams for business process with ConceptDraw software.Data Flow Diagram (DFD)
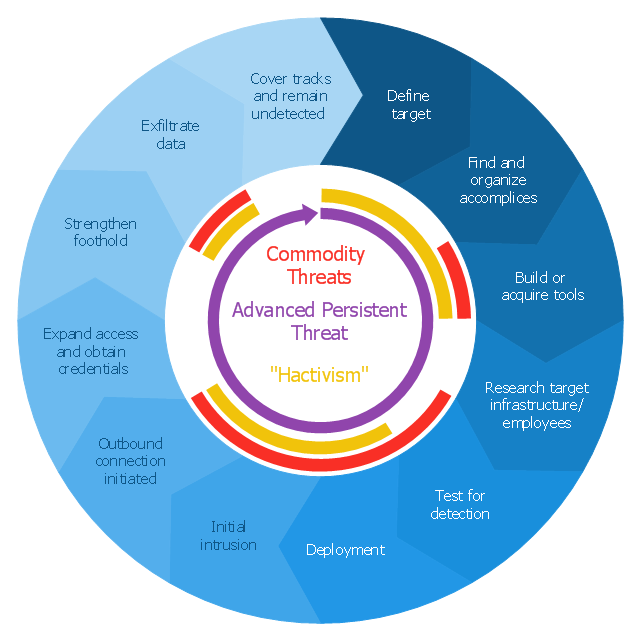
This example is created using ConceptDraw PRO enhanced with solution Data Flow Diagrams. This diagram shows one of the business processes to simplify and accelerate understanding, analysis, and representation.This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
- The System Life Cycle Consists Of
- Systems development life cycle | Circular Arrows Diagrams | Circular ...
- Draw A Sketch Of System Development Cycle
- Systems development life cycle | SSADM Diagram | Process ...
- BPM life cycle | Systems development life cycle | Innovation life cycle ...
- Systems development life cycle | Explain System Development ...
- Systems development life cycle | Circular Arrows Diagrams | Data ...
- Systems development life cycle | DFD - Process of account ...
- Product life cycle graph | Push Notification Lifecycle Overview ...
- Systems development life cycle | SSADM Diagram | Circular Flow ...
- ERD | Entity Relationship Diagrams, ERD Software for Mac and Win
- Flowchart | Basic Flowchart Symbols and Meaning
- Flowchart | Flowchart Design - Symbols, Shapes, Stencils and Icons
- Flowchart | Flow Chart Symbols
- Electrical | Electrical Drawing - Wiring and Circuits Schematics
- Flowchart | Common Flowchart Symbols
- Flowchart | Common Flowchart Symbols