The vector stencils library "Internet symbols" contains 11 Internet clipart images and symbols for drawing computer network diagrams.
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
The vector stencils library "Internet symbols" contains 11 Internet clipart images and symbols for drawing computer network diagrams.
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
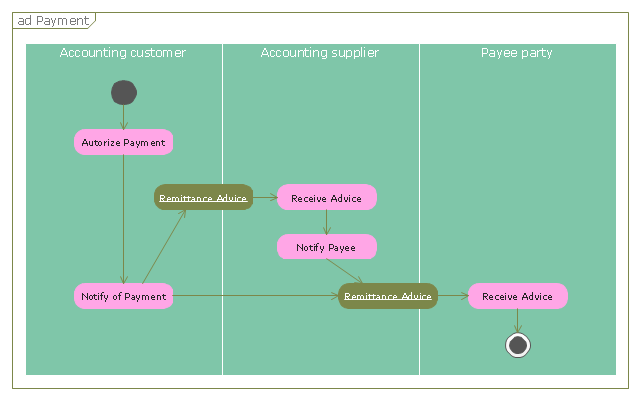
"A payment is the transfer of an item of value from one party (such as a person or company) to another in exchange for the provision of goods, services or both, or to fulfill a legal obligation. ...
Payment methods.
There are two types of payment methods; exchanging and provisioning. Exchanging is to change coin, money and banknote in terms of the price. Provisioning is to transfer money from one account to another. In this method, a third party must be involved. Credit card, debit card, Cheques, money transfers, and recurring cash or ACH (Automated Clearing House) disbursements are all electronic payments methods. Electronic payments technologies are magnetic stripe card, smartcard, contactless card and mobile handset. Mobile handset based payments are called mobile payments." [Payment. Wikipedia]
The UML activity diagram example "Payment process" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
Payment methods.
There are two types of payment methods; exchanging and provisioning. Exchanging is to change coin, money and banknote in terms of the price. Provisioning is to transfer money from one account to another. In this method, a third party must be involved. Credit card, debit card, Cheques, money transfers, and recurring cash or ACH (Automated Clearing House) disbursements are all electronic payments methods. Electronic payments technologies are magnetic stripe card, smartcard, contactless card and mobile handset. Mobile handset based payments are called mobile payments." [Payment. Wikipedia]
The UML activity diagram example "Payment process" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
The vector stencils library "Access and security" contains 17 clipart images of access control and security system equipment which you can easy use in your diagrams and illustrations.
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
The vector stencils library "Internet symbols" contains 11 Internet clipart images and symbols for drawing computer network diagrams.
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
The clip art example "Internet symbols - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
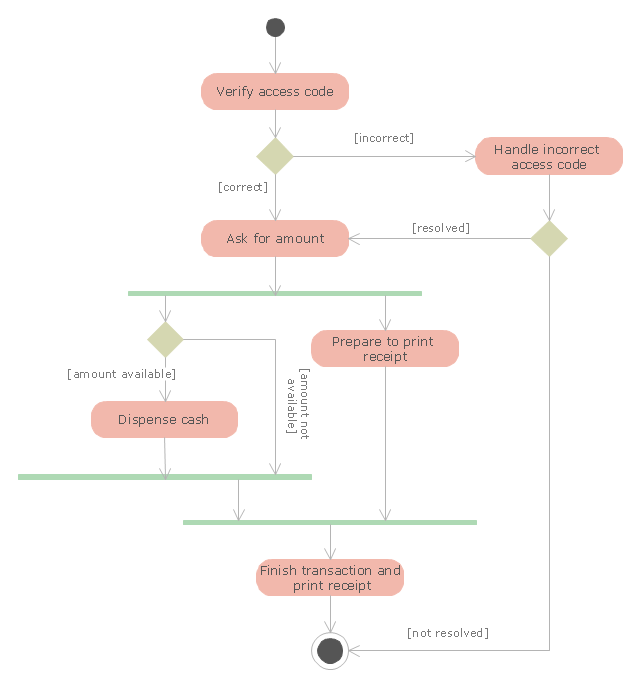
"An automated teller machine or automatic teller machine" (ATM) (American, Australian, Singaporean, Indian, and Hiberno-English), also known as an automated banking machine (ABM) (Canadian English), cash machine, cashpoint, cashline or hole in the wall (British, South African, and Sri Lankan English), is an electronic telecommunications device that enables the clients of a financial institution to perform financial transactions without the need for a cashier, human clerk or bank teller.
On most modern ATMs, the customer is identified by inserting a plastic ATM card with a magnetic stripe or a plastic smart card with a chip that contains a unique card number and some security information such as an expiration date or CVVC (CVV). Authentication is provided by the customer entering a personal identification number (PIN). The newest ATM at Royal Bank of Scotland allows customers to withdraw cash up to £100 without a card by inputting a six-digit code requested through their smartphones.
Using an ATM, customers can access their bank accounts in order to make cash withdrawals, get debit card cash advances, and check their account balances as well as purchase pre-paid mobile phone credit. If the currency being withdrawn from the ATM is different from that which the bank account is denominated in (e.g.: Withdrawing Japanese yen from a bank account containing US dollars), the money will be converted at an official wholesale exchange rate. Thus, ATMs often provide one of the best possible official exchange rates for foreign travellers, and are also widely used for this purpose." [Automated teller machine. Wikipedia]
The UML activity diagram example "Cash withdrawal from ATM" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
On most modern ATMs, the customer is identified by inserting a plastic ATM card with a magnetic stripe or a plastic smart card with a chip that contains a unique card number and some security information such as an expiration date or CVVC (CVV). Authentication is provided by the customer entering a personal identification number (PIN). The newest ATM at Royal Bank of Scotland allows customers to withdraw cash up to £100 without a card by inputting a six-digit code requested through their smartphones.
Using an ATM, customers can access their bank accounts in order to make cash withdrawals, get debit card cash advances, and check their account balances as well as purchase pre-paid mobile phone credit. If the currency being withdrawn from the ATM is different from that which the bank account is denominated in (e.g.: Withdrawing Japanese yen from a bank account containing US dollars), the money will be converted at an official wholesale exchange rate. Thus, ATMs often provide one of the best possible official exchange rates for foreign travellers, and are also widely used for this purpose." [Automated teller machine. Wikipedia]
The UML activity diagram example "Cash withdrawal from ATM" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
The vector stencils library "Mobile and Phones" contains 46 mobile device and telephone icons.
Use it to design your audio, video and multimedia illustrations, presentations, web pages and infographics with ConceptDraw PRO diagramming and vector drawing software.
"A mobile device is a small computing device, typically small enough to be handheld (and hence also commonly known as a handheld computer or simply handheld), having a display screen with touch input and/ or a miniature keyboard...
Early pocket-sized devices were joined in the late 2000s by larger but otherwise similar tablet computers. Input and output of modern mobile devices are often combined into a touch-screen interface.
Smartphones and PDAs are popular among those who wish to use some of the powers of a conventional computer in environments where carrying one would be impractical. Enterprise digital assistants can further extend the available functionality for the business user by offering integrated data capture devices like barcode, RFID and smart card readers." [Mobile device. Wikipedia]
The clipart example "Mobile and Phones" is included in the Audio, Video, Media solution from the Illustrations area of ConceptDraw Solution Park.
Use it to design your audio, video and multimedia illustrations, presentations, web pages and infographics with ConceptDraw PRO diagramming and vector drawing software.
"A mobile device is a small computing device, typically small enough to be handheld (and hence also commonly known as a handheld computer or simply handheld), having a display screen with touch input and/ or a miniature keyboard...
Early pocket-sized devices were joined in the late 2000s by larger but otherwise similar tablet computers. Input and output of modern mobile devices are often combined into a touch-screen interface.
Smartphones and PDAs are popular among those who wish to use some of the powers of a conventional computer in environments where carrying one would be impractical. Enterprise digital assistants can further extend the available functionality for the business user by offering integrated data capture devices like barcode, RFID and smart card readers." [Mobile device. Wikipedia]
The clipart example "Mobile and Phones" is included in the Audio, Video, Media solution from the Illustrations area of ConceptDraw Solution Park.
The vector stencils library "Access and security" contains 17 clipart images of access control and security system equipment which you can easy use in your diagrams and illustrations.
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
- Smart Card Visio Stencil
- Smartcard , secure ID card
- Internet symbols - Vector stencils library | Access and security ...
- Internet symbols - Vector stencils library | Internet symbols - Vector ...
- Internet symbols - Vector stencils library | Network Security | Network ...
- Activity Diagram Of A Smart Card For Paying Parking Fee
- Access and security - Vector stencils library
- Network Icons | Electrical Symbols — Semiconductor Diodes ...
- Cisco IBM. Cisco icons, shapes, stencils and symbols | Database ...
- Internet symbols - Vector stencils library
- IVR Internet - Vector stencils library | Internet symbols - Vector ...
- Design elements - Internet symbols | Internet symbols - Vector ...
- Cloud Computing | What is Cloud Computing | Internet symbols ...
- Virtual networks. Computer and Network Examples | Computer ...
- Access and security - Vector stencils library
- Credit Card Payment Activity Diagram
- Internet symbols - Vector stencils library | Communications - Vector ...
- Internet symbols - Vector stencils library | Design elements - Internet ...
- Invoice payment process - Flowchart | Accounting Flowchart ...
- UML activity diagram (swimlanes) - Template
- ERD | Entity Relationship Diagrams, ERD Software for Mac and Win
- Flowchart | Basic Flowchart Symbols and Meaning
- Flowchart | Flowchart Design - Symbols, Shapes, Stencils and Icons
- Flowchart | Flow Chart Symbols
- Electrical | Electrical Drawing - Wiring and Circuits Schematics
- Flowchart | Common Flowchart Symbols
- Flowchart | Common Flowchart Symbols



-internet-symbols---vector-stencils-library.png--diagram-flowchart-example.png)