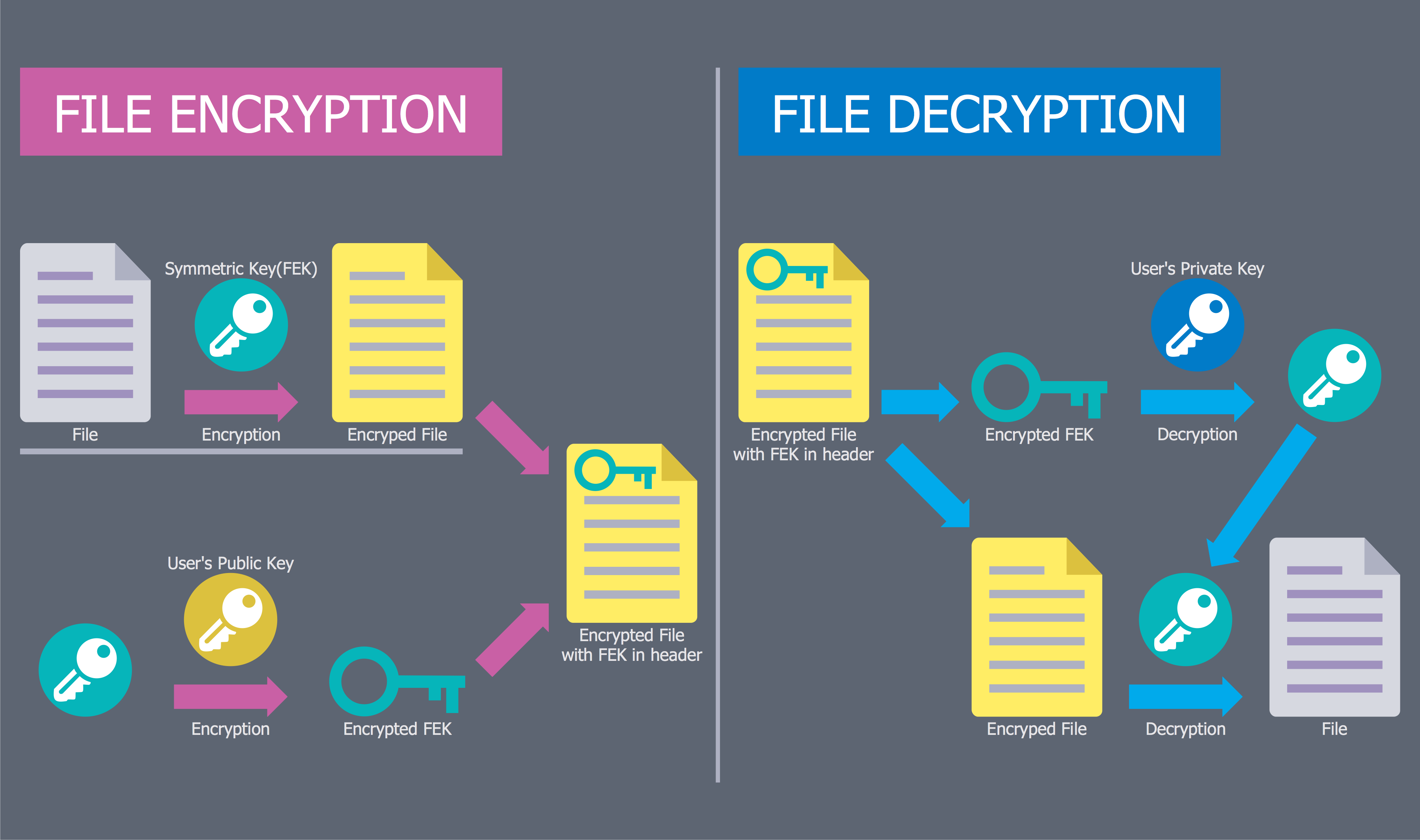
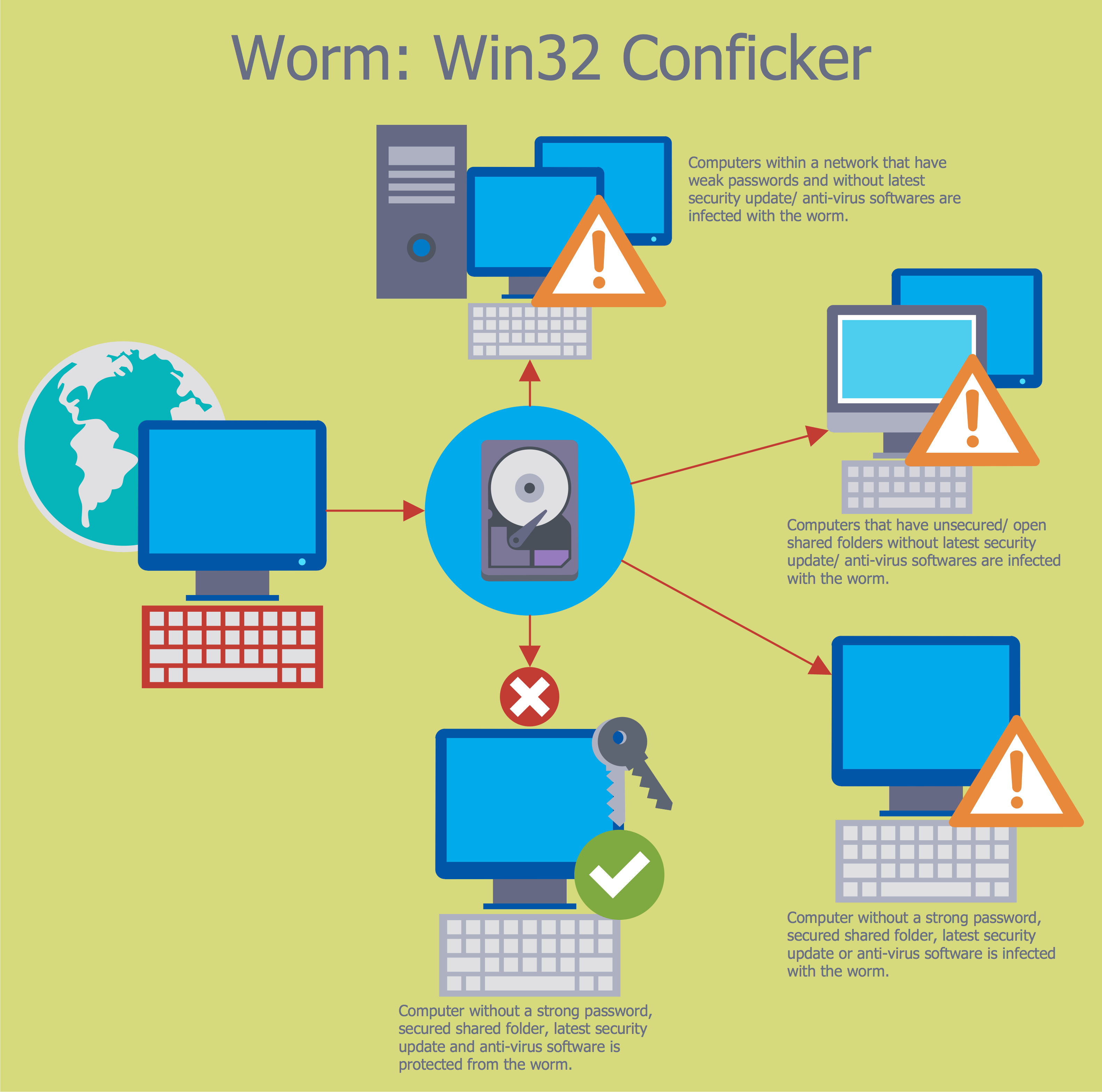
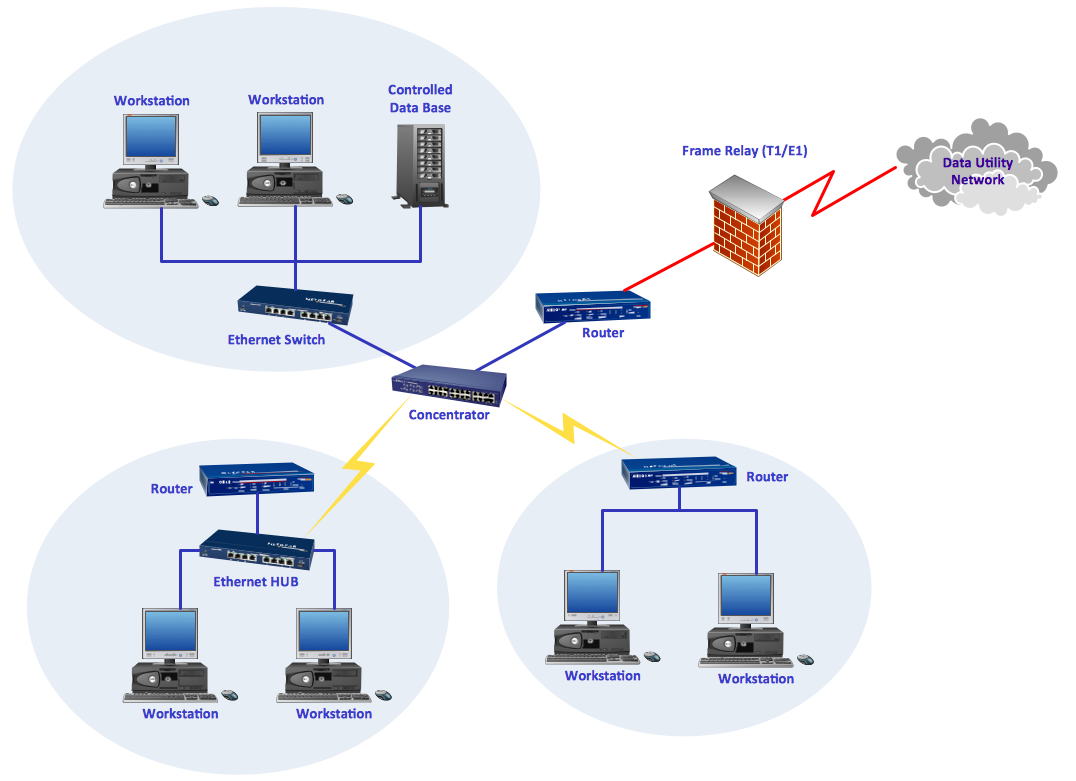
Network Security Diagram
ConceptDraw DIAGRAM diagramming and vector drawing software enhanced with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is the best for effective design professional, colorful and attractive Network Security Diagram of any complexity and degree of detailing.Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw DIAGRAM diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.Network Security Devices
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw DIAGRAM diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them.The samples you see on this page were created in ConceptDraw DIAGRAM using the tools of Network Security Diagrams Solution for ConceptDraw DIAGRAM software. They show protection networks with Firewalls and other network security devices.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
ConceptDraw DIAGRAM Network Diagram Tool
With ConceptDraw DIAGRAM you can diagram a network or create a computer network diagram using specialized libraries of network components such as computers, hubs, smart connectors etc. that simulate network design topologies and devices, network architectures (all these shapes are parts of network diagram tool ConceptDraw DIAGRAM).
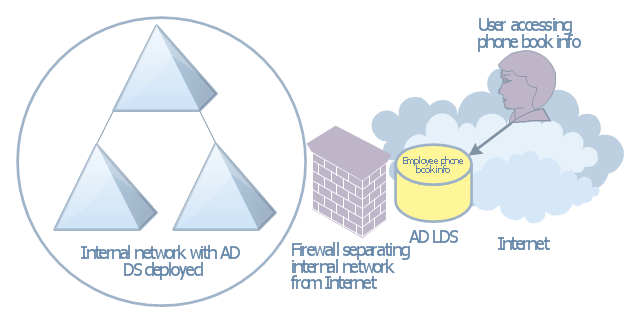
This AD diagram example was created based on the picture "AD LDS as a phone book service" from the book "Active Directory for Dummies".
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Directory services are a great way of providing information that can be fre-
quently retrieved and searched on in a hierarchical way. ... Well, there’s no reason that you can’t create a directory service that’s actually a phone book. Imagine that you need to make a searchable phone directory of your organization available on the Internet. ... This isn’t a difficult task, but it has security repercussions. If you’ve already deployed AD DS and you have the employees’ phone numbers available in that directory, it might not be a good idea to expose your AD DS environment to the Internet for security reasons. Using AD LDS is a great alternative because it can be deployed separately from AD DS and it’s designed to simply provide the information retrieval service that you need without the complications involved with Kerberos authentication and group policies." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "AD LDS as a phone book service" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Surveillance is the monitoring of the behavior, activities, or other changing information, usually of people for the purpose of influencing, managing, directing, or protecting them. This can include observation from a distance by means of electronic equipment (such as CCTV cameras), or interception of electronically transmitted information (such as Internet traffic or phone calls); and it can include simple, relatively no- or low-technology methods such as human intelligence agents and postal interception. ...
Surveillance is very useful to governments and law enforcement to maintain social control, recognize and monitor threats, and prevent/ investigate criminal activity. With the advent of programs such as the Total Information Awareness program and ADVISE, technologies such as high speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of their subjects." [Surveillance. Wikipedia]
[itl.nist.gov/ iad/ 894.01/ tests/ avss/ 2009/ ]
The example "Camera layout schematic" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
Surveillance is very useful to governments and law enforcement to maintain social control, recognize and monitor threats, and prevent/ investigate criminal activity. With the advent of programs such as the Total Information Awareness program and ADVISE, technologies such as high speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of their subjects." [Surveillance. Wikipedia]
[itl.nist.gov/ iad/ 894.01/ tests/ avss/ 2009/ ]
The example "Camera layout schematic" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
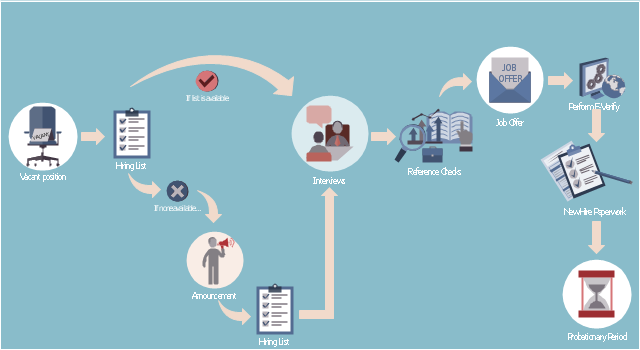
This HR infographics example was designed on the base of flowchart "Hiring Process" from the website of the Idaho Division of Human Resources.
"... hiring process flowchart outlining the steps to fill a vacant position." [dhr.idaho.gov/ hiringprocess.html]
"What is a hiring list and what are they for?
A hiring list consists of applicants who completed and passed the examination for a vacant classified position.
The applicants are ranked on the hiring list in order from highest to lowest score." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Hiring%20 List%20 Guidance.pdf]
"Announcements.
Announcing a vacant position benefits the agency by allowing a wide array of applicants the opportunity to compete for job openings, resulting in a more qualified employee. The State Merit System requires all appointments, promotions and separations in the classified service to be based on competence, valid job requirements, and individual performance." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Announcement.pdf]
"Conducting A Lawful Employment Interview.
Interviewing prospective employees is one of the most important activities employers do. The employer’s objective of an interview is to determine whether an applicant is suitable for an available position. The interview provides the employer an opportunity to obtain in-depth information about a job applicant’s skills, work history, and employment background for this purpose." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Conducting%20 a%20 Lawful%20 Employment%20 Interview.pdf]
"Reference Checks.
References should be checked after a successful interview with a candidate, but before you offer them the position. If after interviewing there are several candidates that are qualified for the position, reference checks are also a way to further distinguish who might best fit within your agency." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Reference%20 Checks.pdf]
"Making the job offer.
Before offering the position to your selected candidate, be sure to speak with your HR and fiscal staff. They may have some suggestions for negotiating the starting salary, etc.
Job Offer Letter.
... A job offer letter should be given to the newly hired employee after you have verbally negotiated the terms of employment. This letter confirms the conditions of employment the selected candidate has accepted and gives them information for their first day." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Making%20 the%20 job%20 offer.pdf]
"E-verify.
To ensure compliance with the Governor’s Executive Order 2009-10, all
State Agencies are encouraged to participate in E-verify.
E-verify is an internet based system that allows an employer, using information reported on an employee’s Form I-9, to determine the eligibility of that employee to work in the United States.
The E-Verify system is operated by the U.S. Department of Homeland Security in partnership with the Social Security Administration and its use is free of charge to employers." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ EVerify%20 Statement.pdf]
"New Hire Paperwork.
There are several important forms for the new employee to fill out." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ New%20 Hire%20 Paperwork.pdf]
"Probationary Period.
All appointments and promotions into classified positions require a probationary period of 1,040 hours
except for peace officers who must serve 2,080 hours.
The probationary period is a working test period to evaluate the work performance of the employee and to determine their suitability for the position." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Probationary%20 Period%20 for%20 Hiring%20 Process.pdf]
The HR infographics example "Hiring process workflow" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the HR Flowcharts solution from the Management area of ConceptDraw Solution Park.
"... hiring process flowchart outlining the steps to fill a vacant position." [dhr.idaho.gov/ hiringprocess.html]
"What is a hiring list and what are they for?
A hiring list consists of applicants who completed and passed the examination for a vacant classified position.
The applicants are ranked on the hiring list in order from highest to lowest score." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Hiring%20 List%20 Guidance.pdf]
"Announcements.
Announcing a vacant position benefits the agency by allowing a wide array of applicants the opportunity to compete for job openings, resulting in a more qualified employee. The State Merit System requires all appointments, promotions and separations in the classified service to be based on competence, valid job requirements, and individual performance." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Announcement.pdf]
"Conducting A Lawful Employment Interview.
Interviewing prospective employees is one of the most important activities employers do. The employer’s objective of an interview is to determine whether an applicant is suitable for an available position. The interview provides the employer an opportunity to obtain in-depth information about a job applicant’s skills, work history, and employment background for this purpose." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Conducting%20 a%20 Lawful%20 Employment%20 Interview.pdf]
"Reference Checks.
References should be checked after a successful interview with a candidate, but before you offer them the position. If after interviewing there are several candidates that are qualified for the position, reference checks are also a way to further distinguish who might best fit within your agency." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Reference%20 Checks.pdf]
"Making the job offer.
Before offering the position to your selected candidate, be sure to speak with your HR and fiscal staff. They may have some suggestions for negotiating the starting salary, etc.
Job Offer Letter.
... A job offer letter should be given to the newly hired employee after you have verbally negotiated the terms of employment. This letter confirms the conditions of employment the selected candidate has accepted and gives them information for their first day." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Making%20 the%20 job%20 offer.pdf]
"E-verify.
To ensure compliance with the Governor’s Executive Order 2009-10, all
State Agencies are encouraged to participate in E-verify.
E-verify is an internet based system that allows an employer, using information reported on an employee’s Form I-9, to determine the eligibility of that employee to work in the United States.
The E-Verify system is operated by the U.S. Department of Homeland Security in partnership with the Social Security Administration and its use is free of charge to employers." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ EVerify%20 Statement.pdf]
"New Hire Paperwork.
There are several important forms for the new employee to fill out." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ New%20 Hire%20 Paperwork.pdf]
"Probationary Period.
All appointments and promotions into classified positions require a probationary period of 1,040 hours
except for peace officers who must serve 2,080 hours.
The probationary period is a working test period to evaluate the work performance of the employee and to determine their suitability for the position." [dhr.idaho.gov/ PDF%20 documents/ Flowchart/ Probationary%20 Period%20 for%20 Hiring%20 Process.pdf]
The HR infographics example "Hiring process workflow" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the HR Flowcharts solution from the Management area of ConceptDraw Solution Park.
Network Visualization with ConceptDraw DIAGRAM
ConceptDraw makes the entire process of network visualization easier thanks to the numerous ready-to-use objects included in the package for presentation of network equipment, LDAP directory symbols and many other objects that symbolize resources in most various representations.- Network Security | Types of Flowchart - Overview | Process ...
- Internet symbols - Vector stencils library | Access and security ...
- Internet symbols - Vector stencils library | | Network Security ...
- Network Security Model | Network Security | Secure Wireless ...
- Network Security . Computer and Network Examples | Cisco security ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Cyber Security Degrees | | Network Security Diagrams | What Is ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- Camera layout schematic | Security and Access Plans | Security ...
- | | | Internet Clipart
- Diagram Of Idea Of Internet
- How to Create a CCTV Diagram in ConceptDraw PRO | Security and ...
- Camera layout schematic | Marketing Diagrams | Computers and ...
- Camera layout schematic | Security and Access Plans | How to ...
- Cloud Computing | AWS Administration and Security - Vector ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Network Architecture | AWS Architecture Diagrams | Information ...
- Security and Access Plans | How to Draw a Security and Access ...
- Design elements - Internet symbols | Internet symbols - Vector ...
- Cisco security - Vector stencils library
- ERD | Entity Relationship Diagrams, ERD Software for Mac and Win
- Flowchart | Basic Flowchart Symbols and Meaning
- Flowchart | Flowchart Design - Symbols, Shapes, Stencils and Icons
- Flowchart | Flow Chart Symbols
- Electrical | Electrical Drawing - Wiring and Circuits Schematics
- Flowchart | Common Flowchart Symbols
- Flowchart | Common Flowchart Symbols