This interactive voice response (IVR) diagram sample illustrates how ENUM call forwarding can be achieved. It was designed on the base of the Wikimedia Commons file: Call Forwarding with ENUM.jpg. [commons.wikimedia.org/ wiki/ File:Call_ Forwarding_ with_ ENUM.jpg]
"Telephone number mapping is a system of unifying the international telephone number system of the public switched telephone network with the Internet addressing and identification name spaces. Internationally, telephone numbers are systematically organized by the E.164 standard, while the Internet uses the Domain Name System (DNS) for linking domain names to IP addresses and other resource information. Telephone number mapping systems provide facilities to determine applicable Internet communications servers responsible for servicing a given telephone number using DNS queries.
The most prominent facility for telephone number mapping is the E.164 Number Mapping (ENUM) standard. It uses special DNS record types to translate a telephone number into a Uniform Resource Identifier (URI) or IP address that can be used in Internet communications." [Telephone number mapping. Wikipedia]
The IVR diagram example "Call Forwarding with ENUM" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Telephone number mapping is a system of unifying the international telephone number system of the public switched telephone network with the Internet addressing and identification name spaces. Internationally, telephone numbers are systematically organized by the E.164 standard, while the Internet uses the Domain Name System (DNS) for linking domain names to IP addresses and other resource information. Telephone number mapping systems provide facilities to determine applicable Internet communications servers responsible for servicing a given telephone number using DNS queries.
The most prominent facility for telephone number mapping is the E.164 Number Mapping (ENUM) standard. It uses special DNS record types to translate a telephone number into a Uniform Resource Identifier (URI) or IP address that can be used in Internet communications." [Telephone number mapping. Wikipedia]
The IVR diagram example "Call Forwarding with ENUM" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"There are two definitions for wireless LAN roaming:
Internal Roaming (1): The Mobile Station (MS) moves from one access point (AP) to another AP within a home network because the signal strength is too weak. An authentication server (RADIUS) performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A Mobile Station roaming from one access point to another often interrupts the flow of data among the Mobile Station and an application connected to the network. The Mobile Station, for instance, periodically monitors the presence of alternative access points (ones that will provide a better connection). At some point, based on proprietary mechanisms, the Mobile Station decides to re-associate with an access point having a stronger wireless signal. The Mobile Station, however, may lose a connection with an access point before associating with another access point. In order to provide reliable connections with applications, the Mobile Station must generally include software that provides session persistence.
External Roaming (2): The MS (client) moves into a WLAN of another Wireless Internet Service Provider (WISP) and takes their services (Hotspot). The user can independently of his home network use another foreign network, if this is open for visitors. There must be special authentication and billing systems for mobile services in a foreign network." [Wireless LAN. Wikipedia]
This Cisco roaming wireless local area network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Internal Roaming (1): The Mobile Station (MS) moves from one access point (AP) to another AP within a home network because the signal strength is too weak. An authentication server (RADIUS) performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A Mobile Station roaming from one access point to another often interrupts the flow of data among the Mobile Station and an application connected to the network. The Mobile Station, for instance, periodically monitors the presence of alternative access points (ones that will provide a better connection). At some point, based on proprietary mechanisms, the Mobile Station decides to re-associate with an access point having a stronger wireless signal. The Mobile Station, however, may lose a connection with an access point before associating with another access point. In order to provide reliable connections with applications, the Mobile Station must generally include software that provides session persistence.
External Roaming (2): The MS (client) moves into a WLAN of another Wireless Internet Service Provider (WISP) and takes their services (Hotspot). The user can independently of his home network use another foreign network, if this is open for visitors. There must be special authentication and billing systems for mobile services in a foreign network." [Wireless LAN. Wikipedia]
This Cisco roaming wireless local area network diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
This example was designed on the base of the diagram from the article "How secure is that mobile app?" by N.V. Fleming on the website of the U.S. Federal Trade Commission (FTC).
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
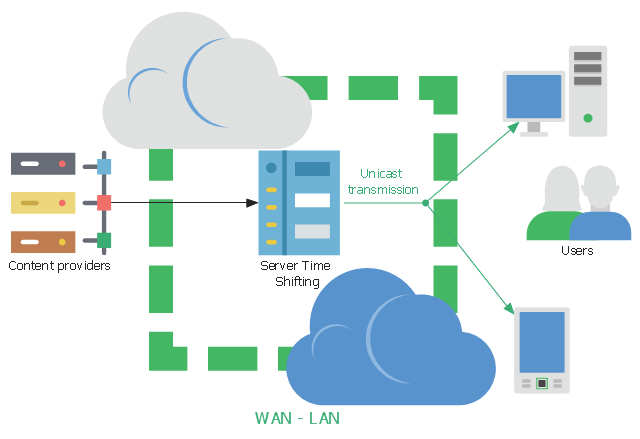
This network diagram sample shows the video on demand (VoD) architecture in a network video recorder (NVR) enviroment. It was designed on the base of Wikimedia Commons file: BaixdemandaArchitecture.png.
[commons.wikimedia.org/ wiki/ File:BaixdemandaArchitecture.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Video on demand (display) (VOD) are systems which allow users to select and watch/ listen to video or audio content when they choose to, rather than having to watch at a specific broadcast time. IPTV technology is often used to bring video on demand to televisions and personal computers." [Video on demand. Wikipedia]
The network diagram example "VoD architecture in a NVR enviroment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and
Communications solution from the Illustration area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:BaixdemandaArchitecture.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Video on demand (display) (VOD) are systems which allow users to select and watch/ listen to video or audio content when they choose to, rather than having to watch at a specific broadcast time. IPTV technology is often used to bring video on demand to televisions and personal computers." [Video on demand. Wikipedia]
The network diagram example "VoD architecture in a NVR enviroment" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and
Communications solution from the Illustration area of ConceptDraw Solution Park.
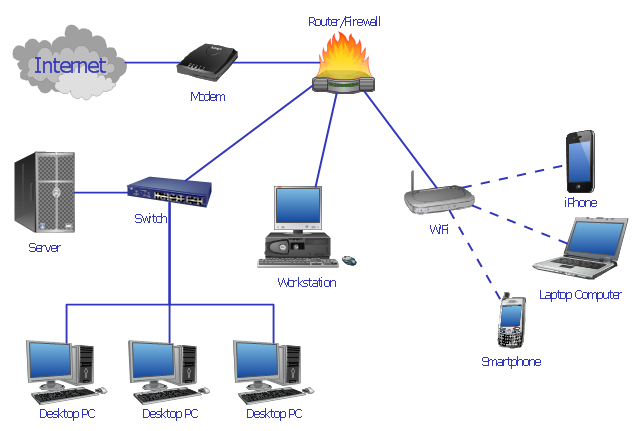
"Network planning and design is an iterative process, encompassing topological design, network-synthesis, and network-realization, and is aimed at ensuring that a new telecommunications network or service meets the needs of the subscriber and operator. Network planning process involves three main steps: 1) Topological design: This stage involves determining where to place the components and how to connect them. 2) Network-synthesis: This stage involves determining the size of the components used, subject to performance criteria such as the Grade of Service (GoS). 3) Network realization: This stage involves determining how to meet capacity requirements, and ensure reliability within the network." [Network planning and design. Wikipedia]
This computer network system design diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
This computer network system design diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
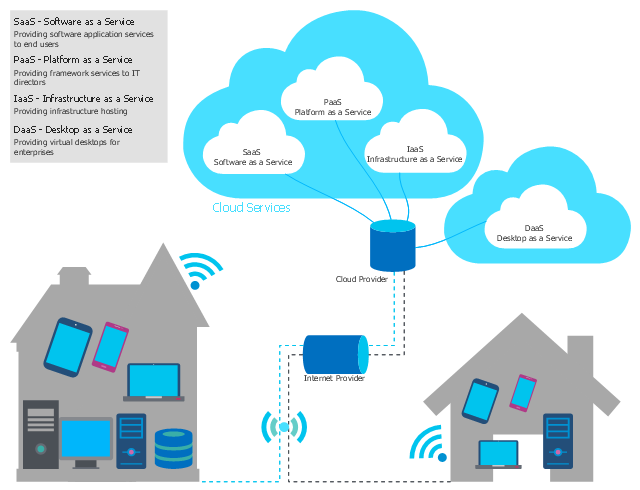
This cloud computing diagram example was drawn on the base of Wikimedia Commons file: Schéma-Cloud-Computing.png. [commons.wikimedia.org/ wiki/ File:Schéma-Cloud-Computing.png]
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
"Service models
Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service." [Cloud computing. Wikipedia]
The example "Cloud computing diagram" was drawn using ConceptDraw PRO software extended with the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution 3.0 Unported license. [creativecommons.org/ licenses/ by/ 3.0/ deed.en]
"Service models
Though service-oriented architecture advocates "everything as a service" (with the acronyms EaaS or XaaS or simply aas), cloud-computing providers offer their "services" according to different models, which happen to form a stack: infrastructure-, platform- and software-as-a-service." [Cloud computing. Wikipedia]
The example "Cloud computing diagram" was drawn using ConceptDraw PRO software extended with the Cloud Computing Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Network Diagram Software Logical Network
ConceptDraw Network Diagram is ideal for network engineers and network designers who need to draw Logical Network diagrams.
This interactive voice response (IVR) diagram sample shows how does the hosted PBX work. It was designed on the base of the Wikimedia Commons file: Hosted pbx.jpg. [commons.wikimedia.org/ wiki/ File:Hosted_ pbx.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A private branch exchange (PBX) is a telephone exchange or switching system that serves a private organization and performs concentration of central office lines or trunks and provides intercommunication between a large number of telephone stations in the organization. ...
Virtual PBX systems or hosted PBX systems deliver PBX functionality as a service, available over the public switched telephone network (PSTN) or the Internet. Hosted PBXs are typically provided by a telephone company or service provider, using equipment located in the premises of a telephone exchange or the provider's data center. This means the customer does not need to buy or install PBX equipment. Generally the service is provided by a lease agreement and the provider can, in some configurations, use the same switching equipment to service multiple hosted PBX customers." [Business telephone system. Wikipedia]
The IVR diagram example "Hosted PBX" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A private branch exchange (PBX) is a telephone exchange or switching system that serves a private organization and performs concentration of central office lines or trunks and provides intercommunication between a large number of telephone stations in the organization. ...
Virtual PBX systems or hosted PBX systems deliver PBX functionality as a service, available over the public switched telephone network (PSTN) or the Internet. Hosted PBXs are typically provided by a telephone company or service provider, using equipment located in the premises of a telephone exchange or the provider's data center. This means the customer does not need to buy or install PBX equipment. Generally the service is provided by a lease agreement and the provider can, in some configurations, use the same switching equipment to service multiple hosted PBX customers." [Business telephone system. Wikipedia]
The IVR diagram example "Hosted PBX" was designed using ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
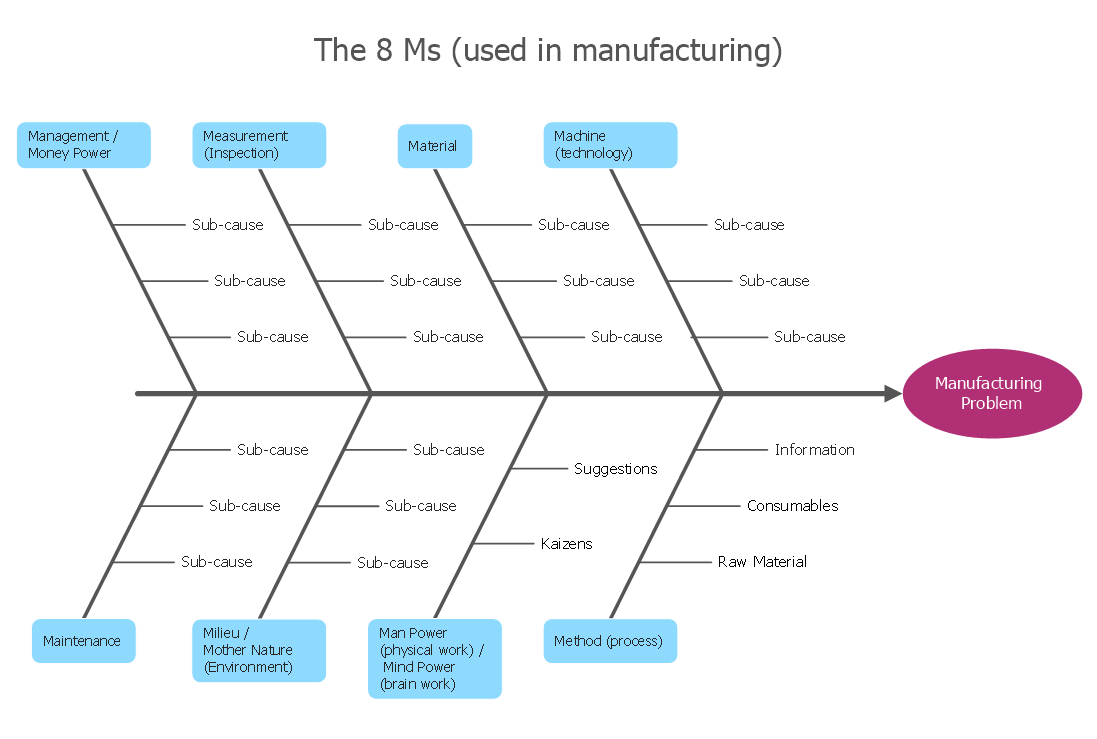
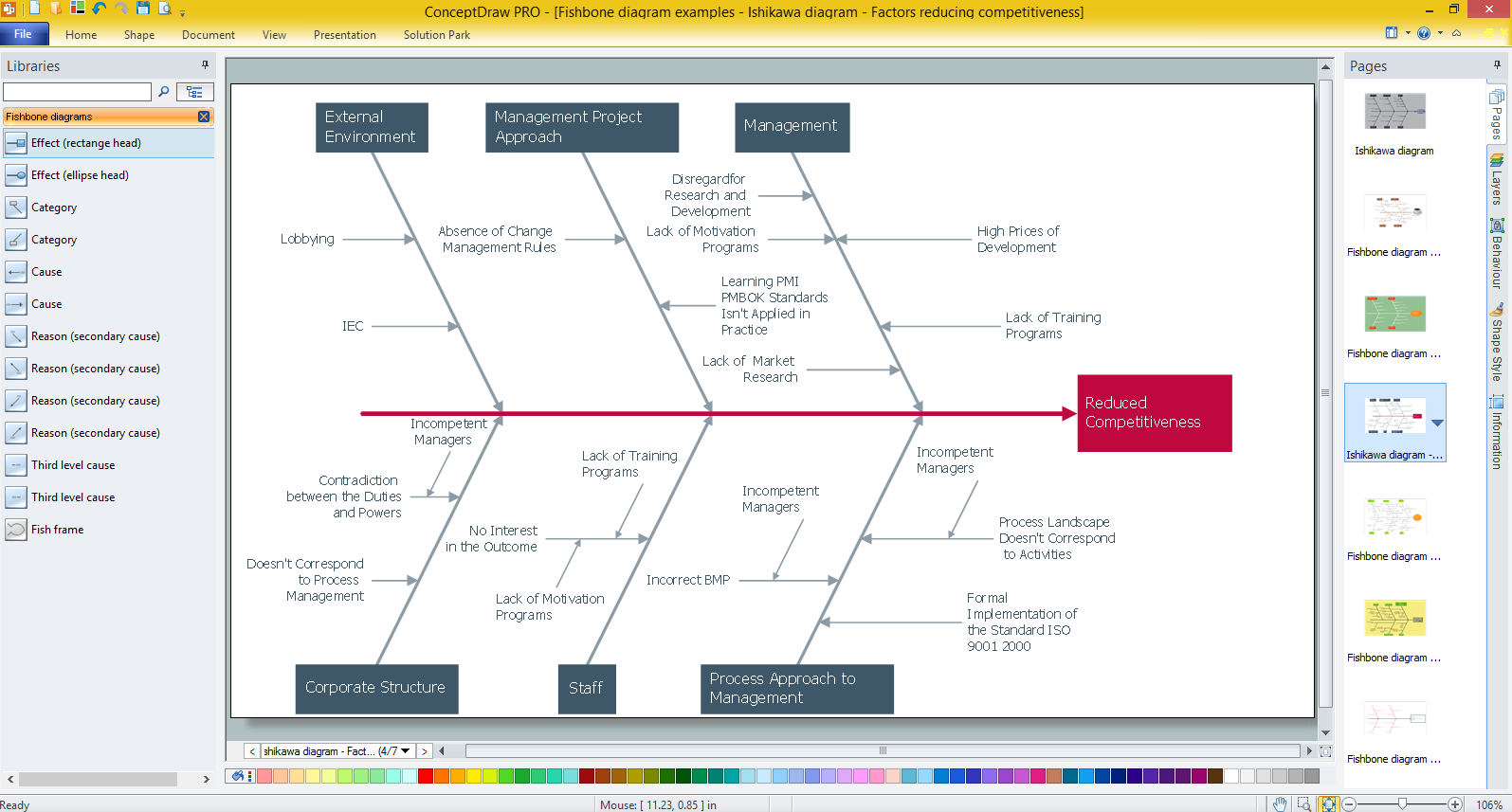
How Do Fishbone Diagrams Solve Manufacturing Problems
How do Fishbone diagrams solve manufacturing problems? Fishbone diagrams are successfully used in various fields of industries and manufacturing to analyze the set of possible causes and their effects. Fishbone diagram provides a process to clearly define the “Effect” and then puts you to thinking about the possible causes, based on the categories of common problems in manufacturing.ConceptDraw PRO application extended with Fishbone Diagrams solution lets you construct Fishbone diagrams and represent globally recognized standards for manufacturing 6 Ms and 8 Ms.
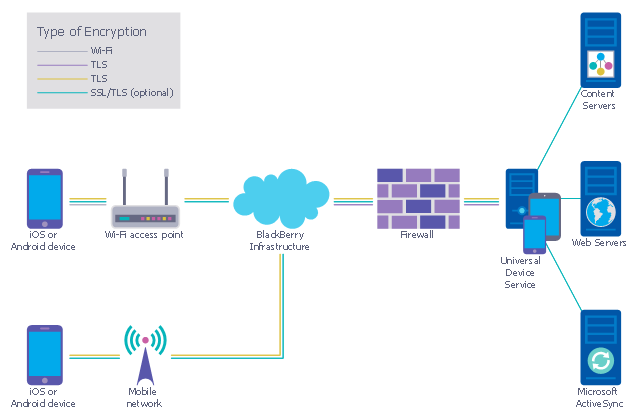
This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
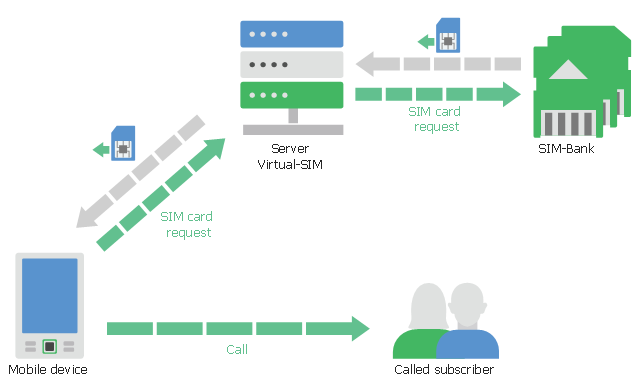
This telecommunication diagram sample shows the virtual-SIM principle of operation. It was designed on the base of Wikimedia Commons file: Схема-работы-Virtual-SIM.jpg.
[commons.wikimedia.org/ wiki/ File:%D0%A1%D1%85%D0%B5%D0%BC%D0%B0-%D1%80%D0%B0%D0%B1%D0%BE%D1%82%D1%8B-Virtual-SIM.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 4.0 International license. [creativecommons.org/ licenses/ by-sa/ 4.0/ deed.en]
Virtual SIM is technical solution of SIM card virtualization. It provides remote online access to the SIM card by means of additional equipment as modem with voice access or additional mobile device. [ru.wikipedia.org/ wiki/ Virtual_ sim]
The telecom diagram example "Virtual-SIM principle of operation" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:%D0%A1%D1%85%D0%B5%D0%BC%D0%B0-%D1%80%D0%B0%D0%B1%D0%BE%D1%82%D1%8B-Virtual-SIM.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 4.0 International license. [creativecommons.org/ licenses/ by-sa/ 4.0/ deed.en]
Virtual SIM is technical solution of SIM card virtualization. It provides remote online access to the SIM card by means of additional equipment as modem with voice access or additional mobile device. [ru.wikipedia.org/ wiki/ Virtual_ sim]
The telecom diagram example "Virtual-SIM principle of operation" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computers and Communications solution from the Illustration area of ConceptDraw Solution Park.
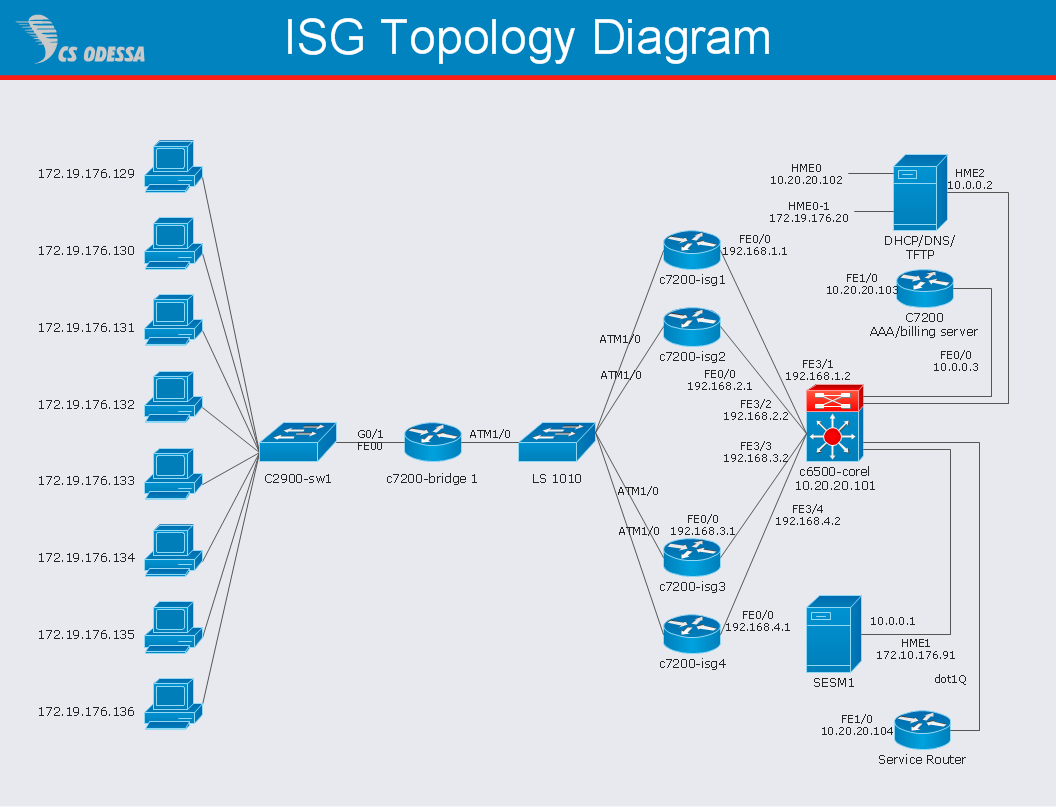
Network Diagram Software ISG Network Diagram
Drawing ISG Network Diagram using ConceptDraw PRO stencils
The vector stencils library "Computer network" contains 51 symbols of computer network devices and equipment for drawing computer network diagrams.
"Network Mapping Software.
A number of software tools exist to design computer network diagrams / or generate visual maps of networks, servers, storage, services, data centers, and other peripherals. Broadly, there are two types of software tools - those that help create diagrams manually and those that generate them using automated / semi-automated approaches.
Type of Software.
(1) Manual - allows users to design and draw logical and physical topology diagrams by manually placing icons and connections.
(2) Automated - generate topology diagrams / maps by traversing the network and automatically discovering resident devices or by importing network data." [Comparison of network diagram software. Wikipedia]
ConceptDraw PRO is the software for manual design of computer network diagrams. The solutions of the Computer and Networks area in ConceptDraw Solution Park extend ConceptDraw PRO with vector stencils libraries, templates and examples for creating the computer network diagrams.
The symbols example "Computer network - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
"Network Mapping Software.
A number of software tools exist to design computer network diagrams / or generate visual maps of networks, servers, storage, services, data centers, and other peripherals. Broadly, there are two types of software tools - those that help create diagrams manually and those that generate them using automated / semi-automated approaches.
Type of Software.
(1) Manual - allows users to design and draw logical and physical topology diagrams by manually placing icons and connections.
(2) Automated - generate topology diagrams / maps by traversing the network and automatically discovering resident devices or by importing network data." [Comparison of network diagram software. Wikipedia]
ConceptDraw PRO is the software for manual design of computer network diagrams. The solutions of the Computer and Networks area in ConceptDraw Solution Park extend ConceptDraw PRO with vector stencils libraries, templates and examples for creating the computer network diagrams.
The symbols example "Computer network - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Computer and Networks solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-and-networks
Create Fishbone Diagrams with the ConceptDraw
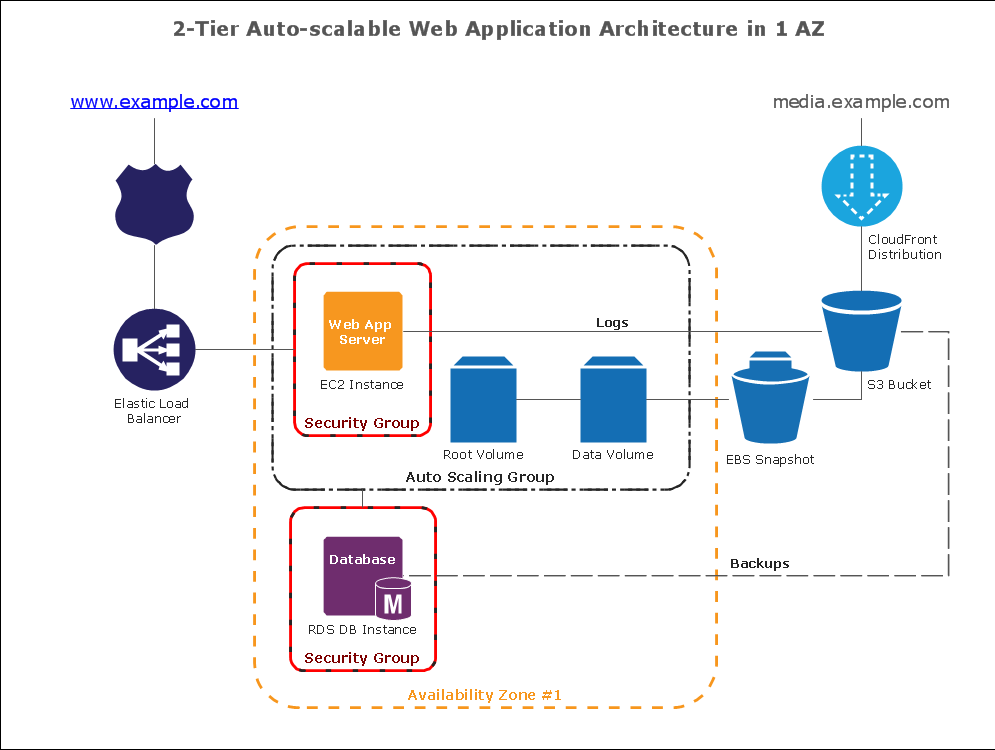
ConceptDraw PRO has the powerful tools for rapid drawing Fishbone diagrams and identifying many possible causes for an effect for problem solving. Causes can be grouped into major categories to identify these sources of variation. Easy create Fishbone diagrams with the ConceptDraw PRO software and Fishbone Diagrams solution included to ConceptDraw Solution Park!How To create Diagrams for Amazon Web Services architecture
Want to create Diagrams for Amazon Web Services architecture? ConceptDraw Solution Park with AWS architecture Solution will help you!- Smart Phone To Access Everything Diagram
- Fault Tree Diagram For Smartphone Failure
- Server Smartphone Communication Diagram
- Diagram Smartphone
- Android UI Design | MS Visio Look a Like Diagrams | Basic ...
- Diagram Of A Local Area Network Comprising Of A Modern A ...
- Local Area Network Diagram
- Roaming wireless local area network diagram
- Smartphone Vector For Diagram
- Smartphone
- Top 5 Android Flow Chart Apps | Data Flow Diagrams | Technical ...
- Visio Files and ConceptDraw | Active Directory Diagram | Network ...
- Smartphone Diagram
- Vector stencils library | Smartphone Ringing
- Visio Stencil Smartphone Free
- Wireless access point - Network diagram | Hotel Network Topology ...
- Mobile app security
- Computer network diagram | IVR mobile - Vector stencils library ...
- UML interaction overview diagram - System authentication ...
- Mobile app security | Tree Network Topology Diagram | Network ...
- ERD | Entity Relationship Diagrams, ERD Software for Mac and Win
- Flowchart | Basic Flowchart Symbols and Meaning
- Flowchart | Flowchart Design - Symbols, Shapes, Stencils and Icons
- Flowchart | Flow Chart Symbols
- Electrical | Electrical Drawing - Wiring and Circuits Schematics
- Flowchart | Common Flowchart Symbols
- Flowchart | Common Flowchart Symbols